Encryptors were found in the PyPI repository: three malicious packages at once (requesys, requesrs and requesr), engaged in typesquatting and faking the popular Requests package. All three packages were ransomware and, as it turned out, were created by a bored schoolboy.
Let me remind you that we also reported that Malicious PyPI Packages Steal AWS Accounts, and also that Popular PyPI ctx Package Stole Developer’s Data.Sonatype experts who discovered the malware say that anyone who mistakenly downloads and uses these packages in their projects falls victim to a rather strange ransomware malware.
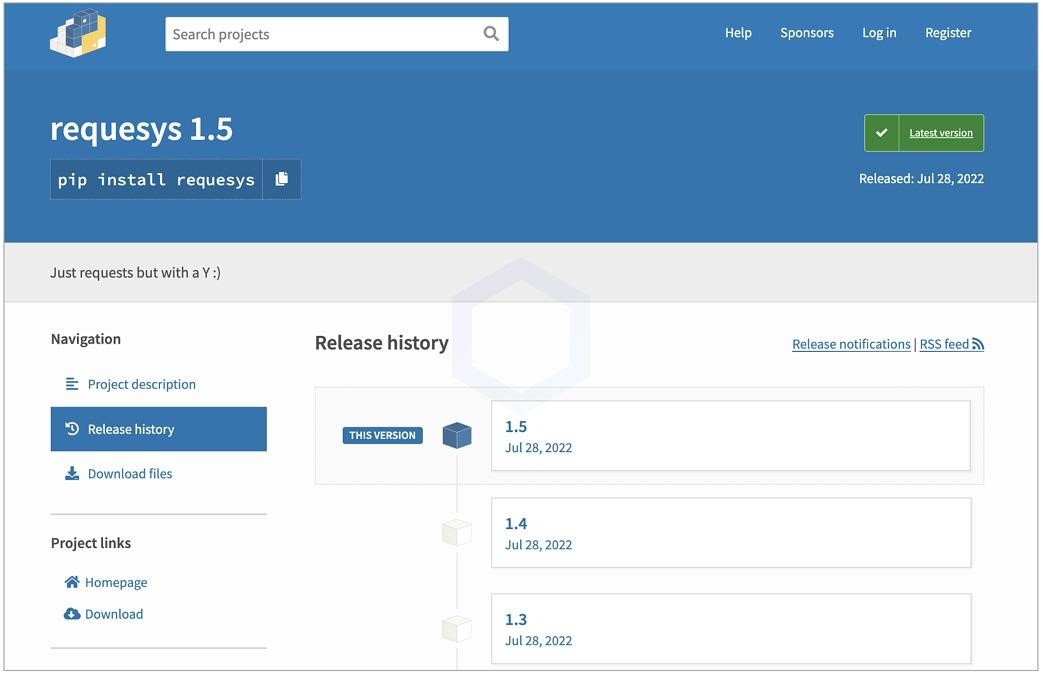
So, all versions of the requesys package (it was downloaded about 258 times) contained scripts that first viewed folders such as Documents, Downloads and Pictures in Windows, and then started encrypting files.
At the same time, versions 1.0-1.4 contained the encryption and decryption code presented in clear text, and version 1.5 already showed an obfuscated base64 executable file, which made the analysis a little more difficult.
The malware used the Fernet module from the cryptographic library for symmetric key encryption. Fernet was also used to generate a random encryption key, which was later used by the victim to decrypt the data.
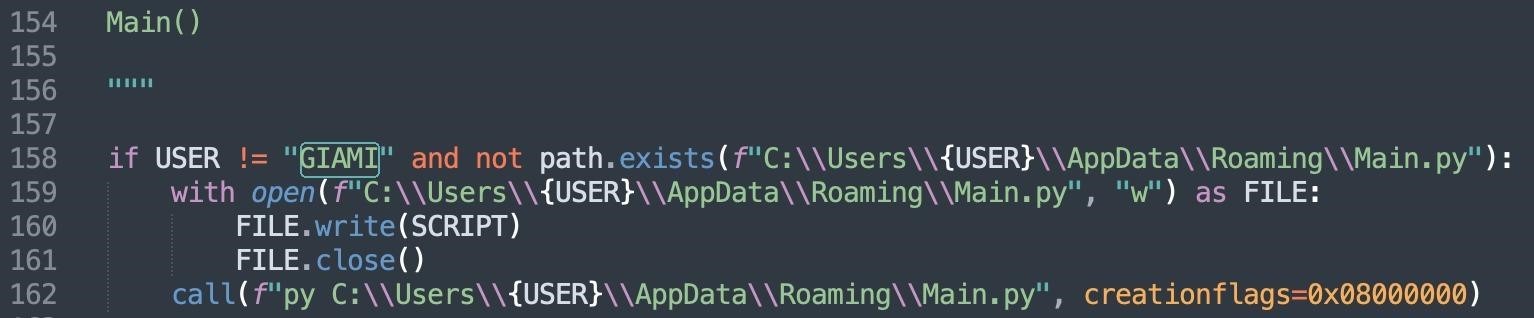
Interestingly, one funny feature was found in the code: the malicious script was only run if the username of the Windows PC was different from “GIAMI”. Obviously, this is the username of the malware author himself.
If everything went well and the ransomware ran on the victim’s system, the affected user saw a pop-up message with further instructions: they were asked to contact the author of the b8ff package, also known as OHR (Only Hope Remains), via the Discord server.

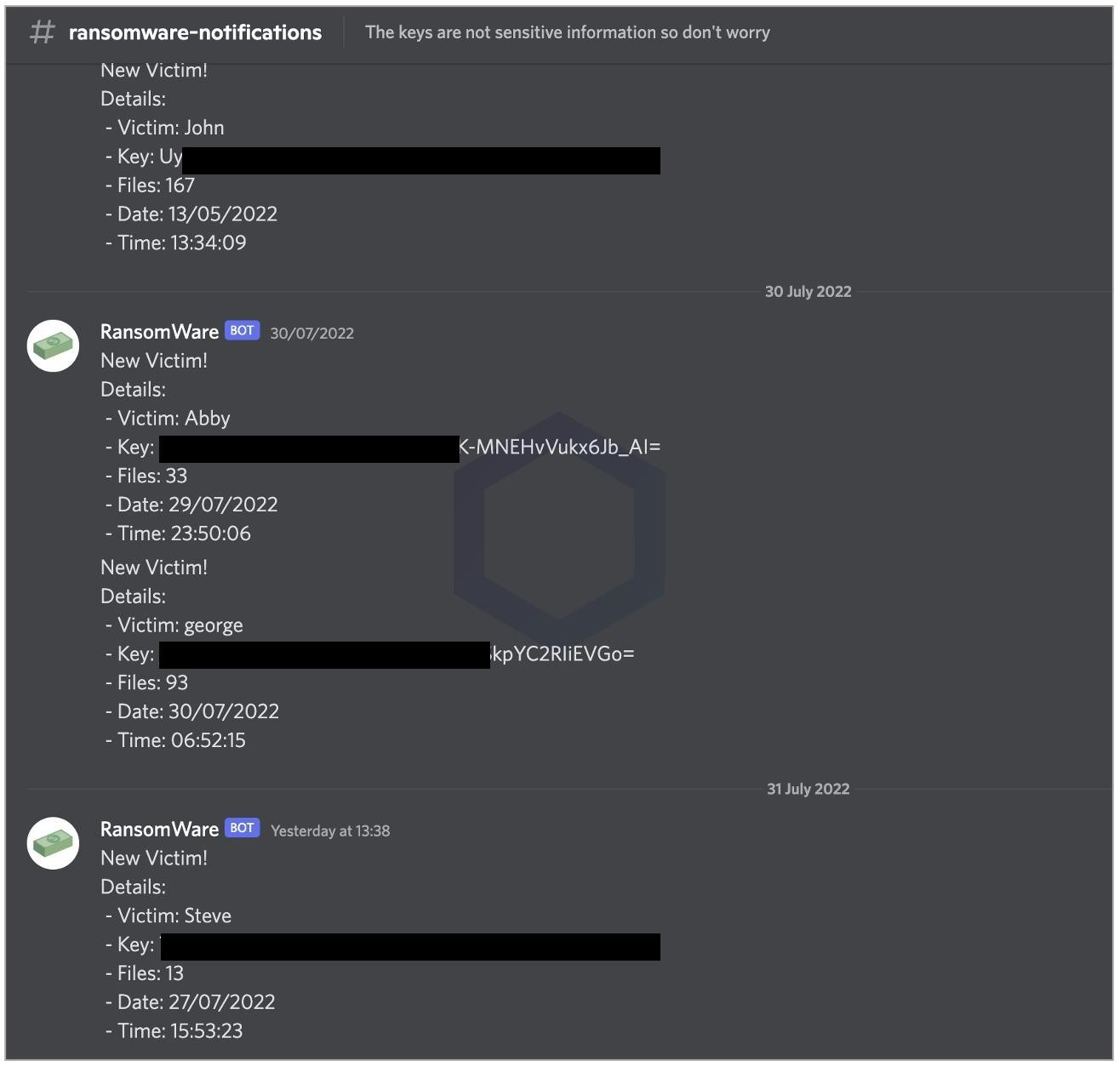
The researchers say that anyone could get into the hacker’s Discord server. There, they discovered the “#ransomware-notifications” channel, which contained a list of usernames for 15 victims who installed and ran a malicious package from PyPI. The auto-generated messages also showed decryption keys that victims could use to decrypt their requesys-locked files.
As already mentioned, version 1.5 was slightly more complex, obfuscated, and shipped as a 64-bit Windows executable. But in general, this EXE acted the same as the malware of previous versions, that is, it generated an encryption / decryption key, uploaded a copy of the key to the author’s Discord, encrypted files, and encouraged victims to go into the data rescue channel.
Analysts say that they managed to identify the author of this simple malware without much difficulty: OHR (Only Hope Remains) or b8ff published the exploit code on GitHub (with a note that the author is not responsible in case of misuse) and, without hiding, used the same nickname in PyPI, Discord, GitHub and other sites. It turns out that OHR even has a YouTube channel with some pretty innocuous hacking tutorials (now removed).
However, the Typesquatter packages did not contain any disclaimer, meaning in their case there were no claims or notices that the packages were published as part of ethical research, and OHR did not try to keep people from infecting their PCs. On the contrary, the packages launched malicious scripts immediately after installation.
As a result, the researchers decided to contact the author of the ransomware and find out about his motives. B8ff made contact easily and informed Sonatype that the ransomware script in these packages was “fully open source” and it was a part of a project that was being created “for fun”. Despite the fact that the packages did encrypt user data, the author stated that they are technically harmless.
B8ff told the experts that he is from Italy and described himself as a schoolboy who is just learning to develop and has only recently become interested in exploits and the ease of creating them.
Experts have alreadyy notified PyPI of their discovery, but have not yet received a response. However, after speaking with experts, b8ff himself helped to prevent further attacks and renamed the requesys package so that developers who misspelled requests in the name would not accidentally download ransomware. Two other packages have been completely removed from PyPI (although it is not clear whether the author himself voluntarily or the PyPI administrators).

