The Termite virus falls under the Babuk ransomware family. Malware of such sort encrypts all the data on your PC (images, text files, excel sheets, audio files, videos, etc) and appends its extra extension to every file, creating...
Ransomware
XSHC Ransomware (TrustFiles@skiff.com) Virus Removal
Our team researched and described the Xshc virus, which belongs under the Dharma ransomware family. Malware of such sort encrypts all user’s data on the computer (photos, text files, excel sheets, music, videos, etc) and...
News
Internet Archive Data Breach! 31 Million Users Affected, Website Offline
The Internet Archive, renowned for its “Wayback Machine”, has suffered a significant data breach. A threat actor compromised the website, stealing a user authentication database containing information on 31 million...
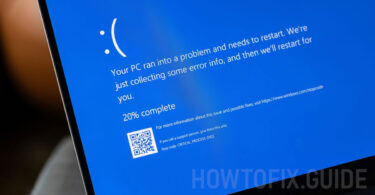
KB5043145 Microsoft Windows 11 Update That Turns a Working PC into a Non-Working One
Last week, Microsoft released an optional update for the Windows 11 operating system, introducing some new features to the Start menu, Taskbar, and Lock screen. Unfortunately, for some users, this update has led to PC...
SurveyLama Data Breach Leaks Info of 4.4 Million Users
In February 2024, a popular online survey platform SurveyLama suffered a data breach. The incident leaked the personal information of more than 4.4 million users, putting their private data and sensitive information at risk. This...
PyPI is Plagued by a New wave of Malicious Packages
The Python Package Index suspended new project creations and user registrations due to a wave of malicious package uploads. Service was restored to normal operations approximately ten hours later without revealing explicit...
Hijackers
Daringnessprattledjeremiani Pop-up Virus — How to Remove Unwanted Ads?
Daringnessprattledjeremianic.com pop-ups that appear while surfing the Web are the outcome of a malicious software activity that resides inside your web browser. Such pop-ups emerge in excessive quantities, diverting and...
Chtneomuli Pop-up Ads Removal — How to Fix Your Browser?
Chtneomulic.com pop-ups that you can see while surfing the Internet are the result of a malicious software infection that resides in your browser. Such pop-ups emerge in excessive quantities, disrupting and irritating you. Most...
Unlockcontent.org Ads Removal Guide — Fix Push Notification
BreezeNotify Pop-up Ads Removal — How to Fix Your Browser?
Tomoutcolip.co.in Notification Removal — How to Fix Your Browser
News-bnexike.xyz Pop-up Virus — How to Remove Unwanted Ads?
Notifynow.pro Ads Removal Guide — Fix Push Notification
News-bnehuru.today Ads Removal Guide — Fix Push Notification
Malware
Trojan:MSIL/Disdroth!MTB Trojan Virus (Disdroth Removal)
The Trojan:MSIL/Disdroth!MTB notification means that your system has a problem. Giving it a go may end up with some really bad consequences. Disdroth is a virus that aims at exposing your PC to further malware injection. Most of...
Trojan:Win32/Pomal!rfn Trojan Virus (Pomal Removal)
The Trojan:Win32/Pomal!rfn notification means that your computer has a problem. Allowing it to run may end up with really bad consequences. Pomal is a malicious application that aims at exposing your system to further malware...
Trojan:Win32/StealC!MTB Trojan Virus (Stealer Removal)
Plariumplayinfo.exe Virus ⛏️ (Coin Miner Trojan) Removal
Trojan:Win32/PWSteal.A Trojan Virus (PWSteal Removal)
Trojan:JS/FakeUpdate.HNAP!MTB Trojan Virus (FakeUpdate Removal)
Behavior:Win32/DefenseEvasion.I!ml Trojan Virus (DefenseEvasion Removal)
Trojan:Win32/Rozena.ALR!MTB Trojan Virus (Rozena Removal)
⚡ Phishing Scams
Ventness.com Review: Is It A Scam Or Legit?
Is Findsagua.com Safe or a Scam? Crucial Info Here
Is Wayofwade.at A Scam? The Hard Facts You Need To Know
Sgtnigssdesilns.shop Fact Check: Legitimate or Shady...
Mixloco.com Review: Avoid Scam Website at All Costs
Is Ivyheifer.com Legit or a Scam? What You Need to Know
Unwanted Programs
SwiftSeek Extension Virus: Easy Removal Instructions
The redirection to SwiftSeek means that you are infected with search hijacker malware. Such a pest tries to modify your browser in order to earn money on advertising. Hijacker that redirects your queries to SwiftSeek site usually...
PUABundler:Win32/MemuPlay PUA Virus (MemuPlay Removal)
The PUABundler:Win32/MemuPlay detection means that your computer has a problem. Allowing it to keep running may lead to really bad consequences. Unwanted programs are not as outright dangerous as common viruses, but still can...
💡 Tutorials
What is the ERR_ADDRESS_INVALID Error and How to Fix it?
ERR_ADDRESS_INVALID is an error that can occur when attempting to access a website. This error can be caused ya variety of issues, including DNS issues, network configuration problems, incorrect browser settings, or a problem...
GridinSoft Online Virus Scanner – How To Check File for Viruses?
Online virus scanner may be quite a useful thing in different situations. Folks know and appreciate VirusTotal, but what if I tell you that almost every single antivirus program listed on the service does not show its full...