Threat actors have used fake websites advertising popular video conferencing software to deliver malware. Frauds particularly mimic Zoom, Google Meet and Skype, and bear on typosquatting techniques. They distributed SpyNote RAT for Android platforms and njRAT and DCRat for Windows systems.
Fake Video Meeting Sites Deliver Malware
Since December 2023, threat actors have used fake websites advertising popular video conferencing software to deliver malware. The key feature of these sites is that they are in Russian and closely resemble their legitimate counterparts, luring victims into downloading disguised malware. The malware downloaded from such sites is Remote Access Trojans (RATs) such as SpyNote RAT for Android platforms and njRAT/DCRat for Windows systems. Researchers say that such an attack vector has been active since at least late 2022. It targets Asian countries, mainly China, Hong Kong, Japan, and Singapore.
Remote Access Trojans is a type of malware that grants attackers with backdoor access to the infected system. These malicious programs can record audio and video, capture screenshots, deploy other malware and steal sensitive data. Once installed, they often operate stealthily in the background, making them difficult to detect. Remote access trojans, along with dropper malware, are commonly used to gain initial access in cyberattacks.
How Does It Work?
The attacker used fake online meeting sites in Russian hosted on a single IP address. Following the bait on Android leads to downloading a malicious APK file, and clicking on Windows downloads a BAT file that results in a RAT payload. A fake site, join-skype[.]info, was created to deceive users into downloading a fake Skype app. Another fake site, online-cloudmeeting[.]pro mimicked Google Meet. The Windows link led to a BAT file that downloaded the final payload named ZoomDirectUpdate.exe, containing DCRat. The Android link led to a SpyNote RAT APK file named meet.apk.
In late January, analysts discovered another fraudulent Zoom website at the URL us06webzoomus[.]pro/l/62202342233720Yzhkb3dHQXczZG1XS1Z3Sk9kenpkZz09/. The site includes a subpath that looks similar to a Zoom meeting ID. If the Google Play link is clicked, a file called Zoom02.apk with SpyNote RAT inside is downloaded. The Windows button downloads a BAT file that, in turn, downloads a DCRat payload. The bogus Zoom page displays a domain similar to the real Zoom domain and a link to the malicious APK file.
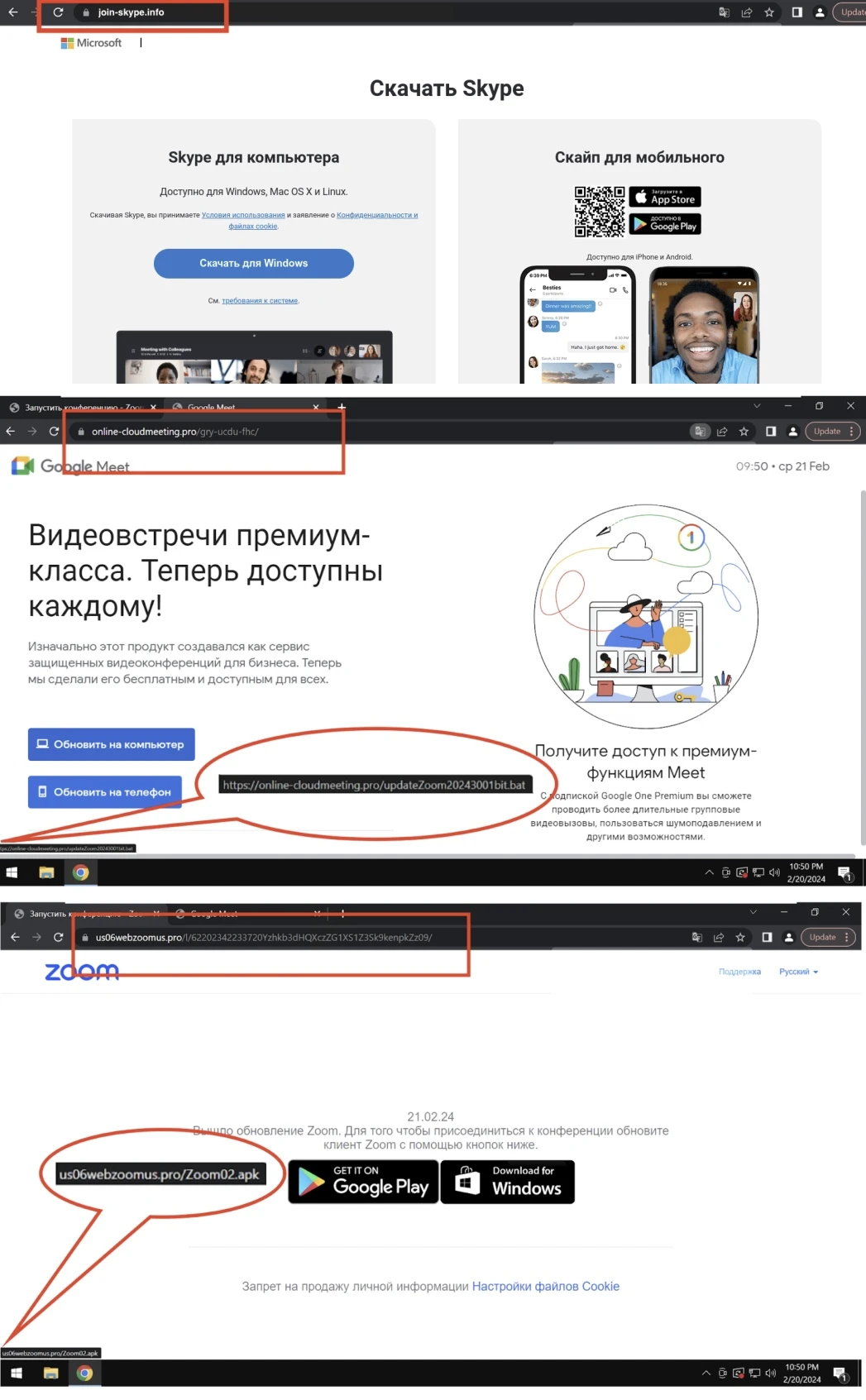
Fake video meeting websites (source: Zscaler)
Phony Google Meet and Zoom websites that host DCRat also have two Windows executable files named driver.exe and meet.exe (inside gry-ucdu-fhc.zip), both being njRAT. These files suggest that the attacker intends to use them in future campaigns. It is worth noting that the threat actor was not targeting iOS users with malware because all the links for iOS users lead to legitimate resources.
How to Avoid Fake Websites?
Phishing remains a severe threat, both from the perspective of privacy and malware risks. Protecting both simultaneously requires having a solid anti-malware solution on hand. GridinSoft Anti-Malware is a perfect solution for this case, that boasts of both advanced detection and network security systems, that will reliably protect you even in sophisticated attacks.
To see whether the website you’re browsing is trustworthy, consider using GridinSoft Malicious URL Scanner. This free website scanner utility that will show you whether you can trust the page, or not.


Yes, they’re an SCAM they also scammed me. Using Paypal offers no protection or refund of your purchase