Researchers have described a new application-layer attack vector based on the User Datagram Protocol (UDP), called Loop DoS. Such attacks can “close” network services in an endless loop, creating large traffic volumes that eventually lead to denial of service.
Loop DoS Attack Vector Targets App-Layer Protocols
Cybersecurity experts from the CISPA Helmholtz Center for Information have discovered a new type of attack coined “Loop DoS” that could affect hundreds of thousands of computer systems. This type of attack targets application servers that use the User Datagram Protocol (UDP). The vulnerability, designated CVE-2024-2169, is related to insufficient data packet verification in the UDP protocol implementation, making it vulnerable to IP address spoofing.
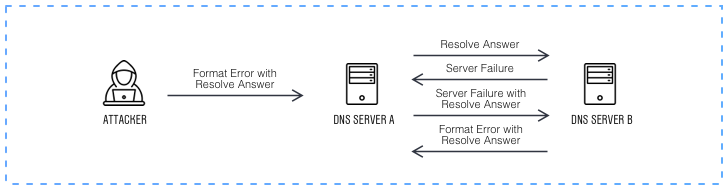
How does the Loop DoS attack work?
In a nutshell, the essence of the attack is that attackers establish infinite communication between application servers. This causes a continuous exchange of messages between them and creates a vast amount of traffic. According to the researchers, such an attack can “close” network services in an endless loop by overwhelming their bandwidth. This poses a threat to Broadcom, Honeywell, Microsoft, and MikroTik systems and, in total, affects around 300,000 hosts and their associated networks. As a result, it overloads systems and makes them unavailable for normal use.
Attack Vector Details
Loop DoS is based on a vulnerability in implementing the UDP protocol, which is prone to IP spoofing and does not provide proper packet inspection. An attacker exploiting this vulnerability can initiate communication with the first server by spoofing the network address of the second server and sending forged UDP packets with the victim’s IP address. The servers respond, leading to excess traffic and a reflexive denial of service (DoS) attack. While there is no evidence that this kind of attack has been exploited in real-world conditions, researchers warn that the vulnerability exists.
Overall, the mechanism resembles Reflect DDoS attacks, that involves the very same trick of sending a forged package. However, this tactic supposes triggering a response of many network devices to a single target. Loop DoS, on the other hand, aims at jamming the entire network by causing large numbers of devices to chaotically communicate with each other.
Who is in the Risk Group?
Experts note that numerous products may be affected, including Broadcom, Cisco, Honeywell, Microsoft, MikroTik, and Zyxel. In addition, various implementations of the UDP protocol are suitable for this: DNS, NTP, TFTP, Echo, Active Users, QOTD, Daytime, Chargen, and Time. While some protocols are obsolete, others are still actively used for basic network functions. Among others are time synchronization, domain name resolution, and unauthenticated file transfers.
The problem is that even attackers can’t stop the loop once they start it. This process can continue until all available server resources are completely exhausted. However, this will make them immune to legitimate requests.
Companies Reaction
Several vendors have confirmed that their products are vulnerable to Loop DoS. Among them are Broadcom, Cisco, Honeywell, Microsoft, and MikroTik. Broadcom has already released a patch for the attack, which may only affect some of its older routers. Microsoft stated that the attack did not cause the host to crash, but it would consider a future fix for the problem in Windows. MikroTik, on the other hand, promised to release a patch soon. Cisco responded by fixing the issue under the identifier CVE-2009-3563 back in 2009. Lastly, Zyxel confirmed that some of its older products are affected by Loop DoS but will no longer receive patches.
Mitigation Tactics
To prevent the risk of Loop DoS attacks, you must install the latest patches from vendors or replace solutions that no longer receive updates. It also recommends disabling unnecessary UDP services and applying firewall rules and access control lists for UDP applications. In addition, it suggests using anti-spoofing solutions such as BCP38 and Unicast Reverse Path Forwarding (uRPF), as well as Quality-of-Service (QoS) measures. These measures will help limit network traffic, protect against network loop abuse, and, as a result, minimize risk.

