Malicious packages were again found in the PyPI repository – this time the libraries were caught stealing confidential information, including credentials from AWS, and after the theft, the information was stored in .TXT files, available to everyone.
Another problem in PyPT was discovered by Sonatype specialists. They say that the following packages showed suspicious activity:- loglib-modules;
- pyg-modules;
- pygrata;
- pygrata-utils;
- hkg-sol-utils.
Let me remind you that we also wrote that Popular PyPI ctx Package Stole Developer’s Data, and also that PyPI repository got rid of 11 packages that were stealing Discord tokens and passwords.
While the first two packages tried to imitate the names of real-life popular projects, trying to deceive inattentive or inexperienced users, the other three did not have a pronounced targeting. It is noted that all five libraries showed similar code and links.
Experts write that the loglib-modules and pygrata-utils packages were created to steal data, including credentials from AWS, network interface information, and environment variables. That being said, the almost-named pygrata package did not have its own data stealing functionality, but used pygrata-utils as a dependency. For this reason, four malicious packages were removed from PyPI almost immediately after discovery, and pygrata lingered in the repository longer, because this library itself did not pose a threat.
One of the most interesting features of this campaign was that after the data was transferred to the PyGrata[.]com domain, the stolen credentials were stored in cleartext .TXT files. Worse, the endpoint was badly protected, so analysts were able to access it and study the stolen information.
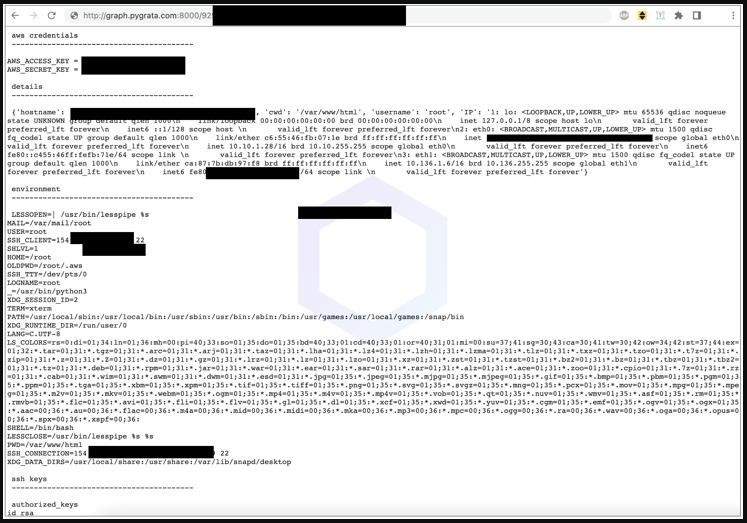
Trying to act ethically and remembering that they might have missed something, the researchers contacted the owners of the domain, informing them of their findings and requesting an explanation. Shortly thereafter, the endpoint disappeared from the public domain, and Sonatype never received a response. This seems to indicate that the data theft was not carried out for research purposes.
Sonatype experts note that even if it was some kind of pentest, and the operators of this campaign did not intend to abuse the stolen information, the presence of these packages in PyPI still put users at risk, since their credentials were eventually leaked to the side and were freely available to everyone.

