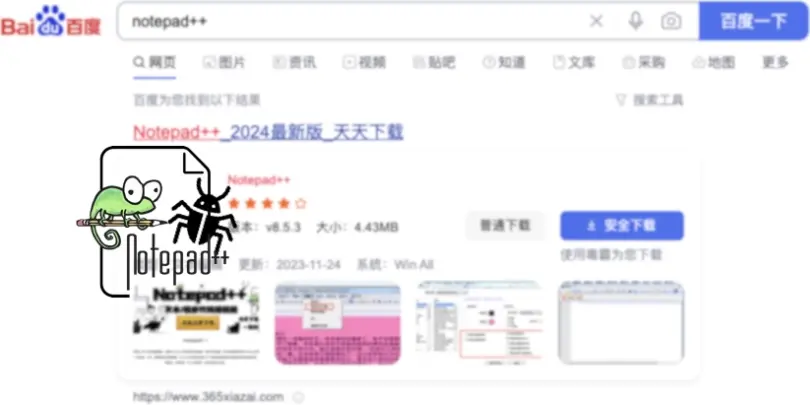
Chinese users are faced with malicious search ads. These ads mainly plague Baidu search engine, spreading malware by promoting fake freeware downloading pages.
Baidu Malvertising Campaign Spreads Backdoors
A fresh report reveals that users of Baidu, one of China’s most popular search engines, were affected by phishing sites in search results. Investigators have identified two related cases of malvertising, in which modified versions of popular text editors were distributed through search engines like Baidu. In the first case, the malicious resource appeared in the advertisement section, while in the second case, it was at the top of regular search results.
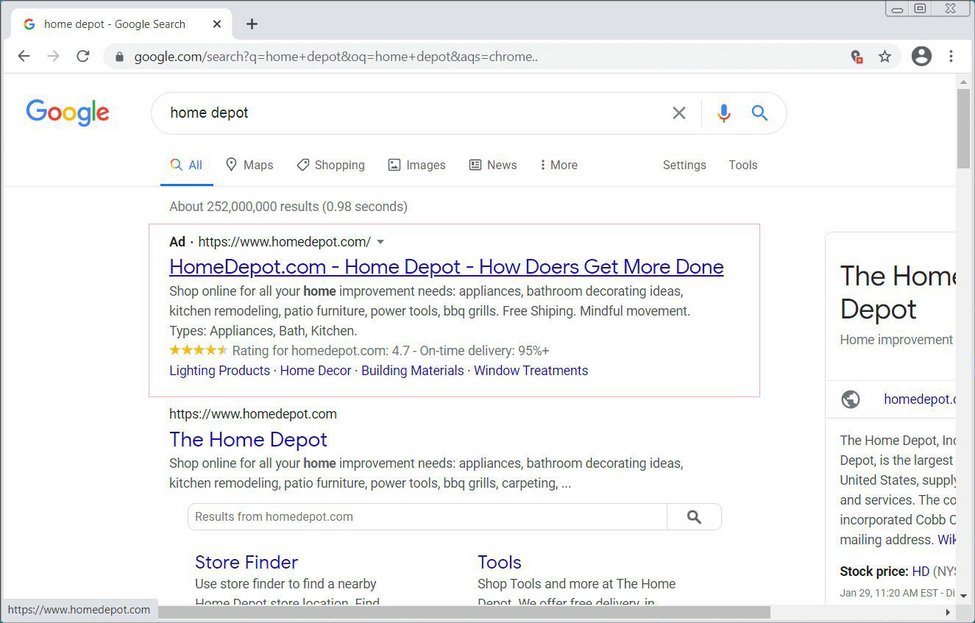
Example of malvertising at the top of search results
Malvertising is a tactic used to direct users to malicious websites using legit advertising engines. The latter usually places ads at the top of search results, which increases visibility of a scam. To make it look more legit, frauds use typosquatting, so it is harder for inattentive victims to see the difference. In this way, the malicious site associated with the Notepad++ search disguises itself as legit. It enticed users to download something that appears to be Notepad++ but delivers a variant named Notepad‐‐. However, we will talk further about what the user really gets.
Infection Mechanism
As I said above, it all starts with the malicious ad that appears on top of search results. The promotion directs the user to a phishing Notepad ++ site that masquerades as a real one. Clicking the link downloads the text editor for the specified operating system. However, the malicious links redirect users to potentially harmful content.
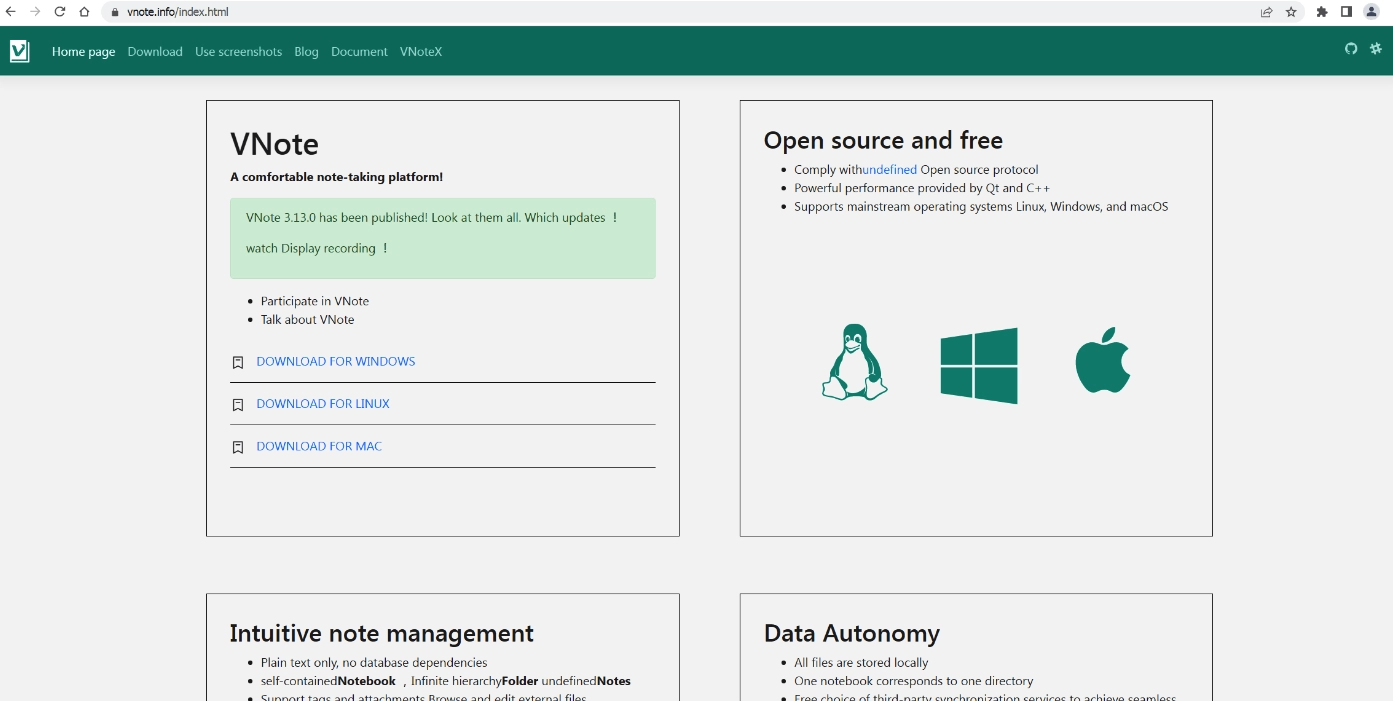
Fake website
Security researchers have dissected the malicious versions of the text editors for Linux and macOS, uncovering subtle yet significant differences from their legitimate counterparts. These malicious versions exhibit backdoor functionalities, potentially leading to unauthorized access and data compromise on infected systems.
The backdoor applications establish communication with a C2 server via HTTPS, allowing threat actors to issue commands remotely. These commands include SSH connections, launching new agents, terminating processes, and even taking screenshots. Further investigation reveals a connection between the infected applications distributed through different sites, suggesting a coordinated effort by threat actors to maximize their reach and impact.
Safety Recommendations
Unfortunately, this is not the first incident of search advertising abuse. These days, we see an increase in the number of such frauds across pretty much all search engines. Unclear rules and dubious moderation of adverts make this area a fertile ground for scammers. However, I have some practical tips to help you avoid unpleasant consequences.
The first rule is to be careful where you click. I strongly recommend avoiding clicking on search results links that say “Sponsored” next to them. Instead, always use the official website of the application you want to download.
The second and equally important tip is to use an advanced security solution such as GridinSoft Anti-Malware. Thanks to its built-in Internet security module, it blocks phishing sites, thus preventing unwanted downloads. It can also scan your device for threats and neutralize them.