In February 2024, a popular online survey platform SurveyLama suffered a data breach. The incident leaked the personal information of more than 4.4 million users, putting their private data and sensitive information at risk. This...
Author - Emma Davis
PyPI is Plagued by a New wave of Malicious Packages
The Python Package Index suspended new project creations and user registrations due to a wave of malicious package uploads. Service was restored to normal operations approximately ten hours later without revealing explicit...
Loop DoS Attack
Researchers have described a new application-layer attack vector based on the User Datagram Protocol (UDP), called Loop DoS. Such attacks can “close” network services in an endless loop, creating large traffic volumes...
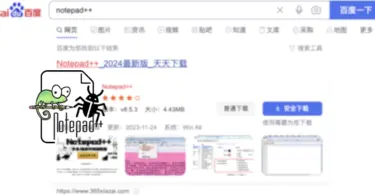
Malvertising in Baidu Targeting Chinese Users
Chinese users are faced with malicious search ads. These ads mainly plague Baidu search engine, spreading malware by promoting fake freeware downloading pages. Baidu Malvertising Campaign Spreads Backdoors A fresh report reveals...
Fake Zoom and Google Meet Sites Deliver Malware
Threat actors have used fake websites advertising popular video conferencing software to deliver malware. Frauds particularly mimic Zoom, Google Meet and Skype, and bear on typosquatting techniques. They distributed SpyNote RAT...
Free Rhysida Ransomware Decryptor Published
South Korean researchers have made a significant breakthrough in the fight against ransomware, unveiling a decryption tool that exploits a critical flaw in the encryption algorithm of Rhysida ransomware. However, such a...
Zloader is Back, Possessing New Capabilities & Tricks
An infamous Zloader malware is back, according to the most recent report of malware sandbox ANY.RUN. The researchers not only detected the rise in activity of the before-offline malware, but also managed to analyze the new sample...
TeamCity Critical Vulnerability Uncovered, Update Now
JetBrains recently discovered a critical authentication bypass vulnerability in TeamCity On-Premises servers. This flaw could allow attackers to execute remote code without user interaction, gaining admin privileges on affected...
White Phoenix Decryptor Tool Online Version Released
White Phoenix decryptor receives an upgrade with the online version. CyberArk, the developer, created a convenient web interface – a big step up from the published source code, as it was previously. The decryptor offers to...
Ransomware Victims Keep Refusing to Pay, Researchers Report
Ransomware is losing effectiveness, and victims increasingly refuse to pay the ransom. Specialists have been observing this trend since the middle of 2021, and some factors contribute to it, which we will discuss below...