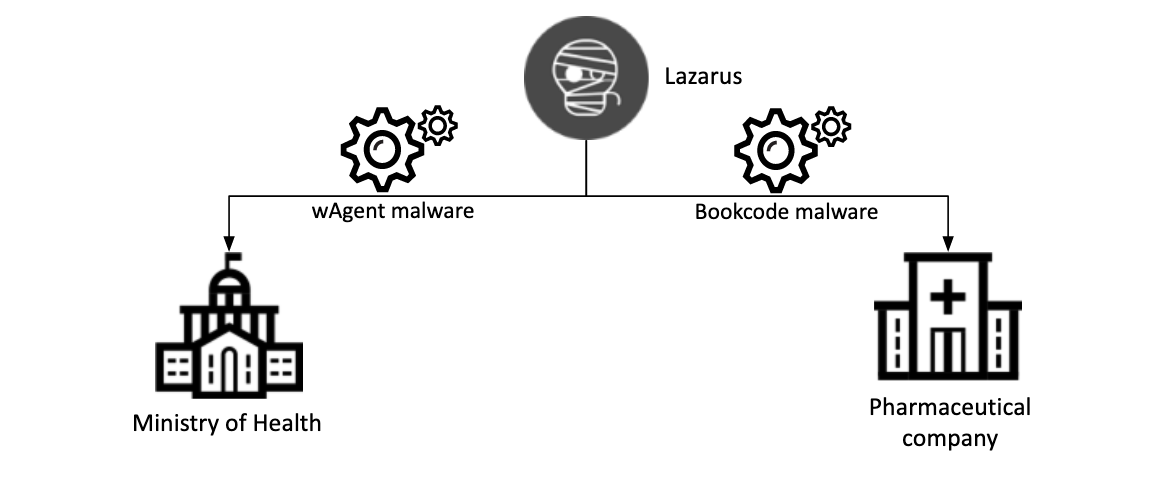
Researchers at Kaspersky Lab have prepared a report on the activity of the North Korean hack group Lazarus, which is interested in data on vaccines against COVID-19 and recently attacked two organizations involved in research on this topic.
According to the company, new Lazarus attacks occurred in September and October 2020, targeting the Ministry of Health, as well as an unnamed pharmaceutical company authorized to manufacture and distribute COVID-19 vaccines, signaling a clear interest in coronavirus research by hackers.The attack on the Ministry of Health was recorded on October 27, 2020: two Windows servers were hacked. Experts were unable to determine the initial vector of infection, but as a result of the incident, attackers were able to install a complex cluster of malwares on compromised servers.
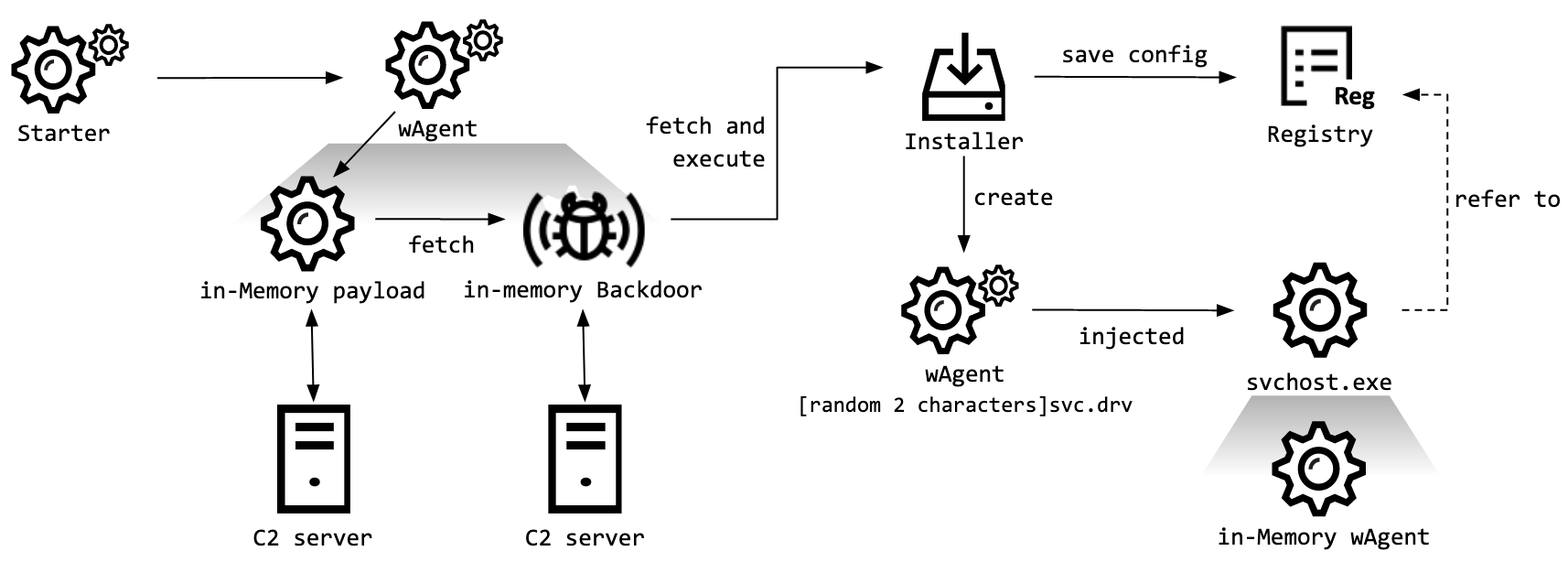
Kaspersky Lab tracks this malware as wAgent, and it was previously used to attack cryptocurrency companies. The main component of this malware works only in memory and receives additional payloads from the attackers’ remote server.
The second incident involved affected an unnamed pharmaceutical company and occurred on September 25, 2020. According to company telemetry, this time the Lazarus team deployed the Bookcode malware previously reported by ESET.
The infection was a result of an attack on the supply chain and hacking of a South Korean software company.
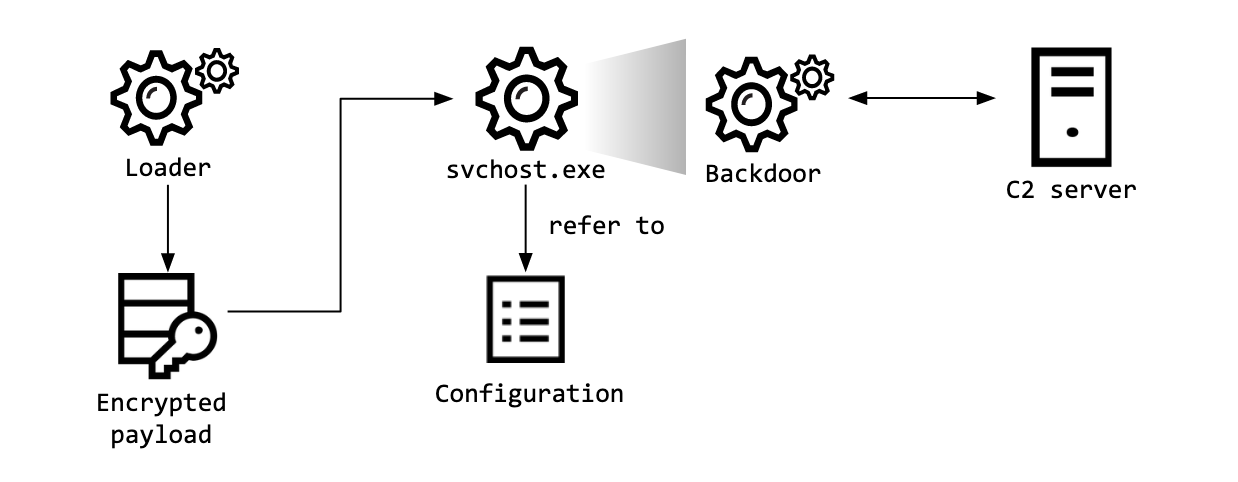
Both malwares were designed to act as full-featured backdoors, giving their operators complete control over the infected machines. Each attack used different tactics, techniques and procedures, but the researchers believe that Lazarus is behind both incidents.
Using wAgent, the attackers executed various shell commands to collect information from victims’ machines. An additional payload was also deployed on the infected servers, including the mechanism of stable presence in the system.
The BookCode backdoor, in turn, was used to collect system and network information from the victim’s network, as well as a SAM dump containing password hashes. The attacker also tried to gather information about other machines on the network, probably planning to develop the attack further.
Let me remind you that vulnerability in Kaspersky Anti-Virus allowed cybercriminals monitoring users, while Russian hackers tried to steal COVID-19 research data.