Kaspersky Lab anti-virus products contained a vulnerability that exposed the user’s unique identifier to the websites that he visited.
Thus, these sites, as well as a number of other third-party services, could track all user’s movement on the Web.The vulnerability received the identifier CVE-2019-8286. Security researcher Ronald Eikenberg reported it.
“The Kaspersky software worked essentially as well or as badly as Windows Defender. One day, however, I made a strange discovery. I looked at the HTML source code of an arbitrary website and came across the strange line of code”, — reports Ronald Eikenberg.
This is a code stripe:
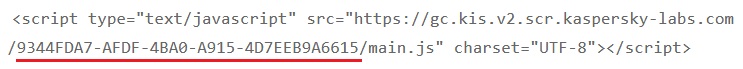
The problem exists due to the incorrect operation of the Kaspersky URL Advisor module designed for URL scanning. This module is present in Kaspersky Lab anti-virus programs.
By default, Kaspersky Internet Security embeds a remotely stored JavaScript file in the HTML of each visited page. This happens even in private browsing mode.
During the study, Eikenberg found that the URL of this JavaScript file contains a string that is unique for every single user of Kaspersky Lab anti-virus.
“When I checked the HTML source of other websites displayed in my browser, I found the strange code on each and every page. Without exception, even on the website of my bank, a script from Kaspersky was introduced. So I had an inkling that the Kaspersky software might have something to do with it”, — reports Ronald Eikenberg.
It turns out that this is some kind of identifier that can be used to track a user on the Web.
“This approach is not a good idea, because other scripts that work in the context of the domain can access the HTML code at any time. Therefore, they will have access to the unique identifier that every Kaspersky product is hanged on”, — the researcher writes.
Ekenberg reported about problem to the developers of Kaspersky Lab, and the latter responded promptly, recognizing the problem and resolving it. The antivirus company also published information about the vulnerability on its website.
Read also: ExtraHop experts believe that corporate security software can transfer data to the third parties
Additionally, the German CERT-Bund has issued a warning entry in the National Vulnerability Database of the US-CERT regarding the information leak. Furthermore, there is an entry in the National Vulnerability Database of the US-CERT.

