Information security researcher Pierre Kim published a report, in which he said that 28 backdoors and a number of other vulnerabilities were found in the firmware of the popular routers of the Chinese company FiberHome Networks, widely used in South America and Southeast Asia.
Problems were found in two models of FTTH ONT routers: FiberHome HG6245D and FiberHome RP2602. FTTH ONT stands for Fiber-to-the-Home Optical Network Terminal. This refers to special devices installed at the ends of fiber optic cables. Such devices are designed to convert signals transmitted over fiber optic cables into classic Ethernet and Wi-Fi.Kim notes that the control panel of both devices is not accessible through the external IPv4 interface, making attacks impossible through the Internet. Telnet is also disabled by default, as it is often abused by botnets.
With this feature, the expert begins a long list of backdoors and vulnerabilities that he found in the FiberHome HG6245D and FiberHome RP2602 firmware. At the same time, Kim writes that, in his opinion, some backdoors were introduced by the manufacturer himself and appeared in the code intentionally.
The researcher describes the following problems:
- the control interface leaks device information, if it is accessed from a browser with a disabled JavaScript. In particular, the device’s MAC address has leaked;
- the backdoor allows an attacker to use the device’s MAC address to establish a Telnet connection to the router by sending a specially crafted HTTPS request [https://[ip]/telnet?Enable=0&key=calculated(BR0_MAC)];
- passwords and authentication cookies of the admin panel are stored in plain text in HTTP logs;
- the management interface is protected by a hard-coded SSL certificate stored on the device, it can be downloaded for MitM attacks;
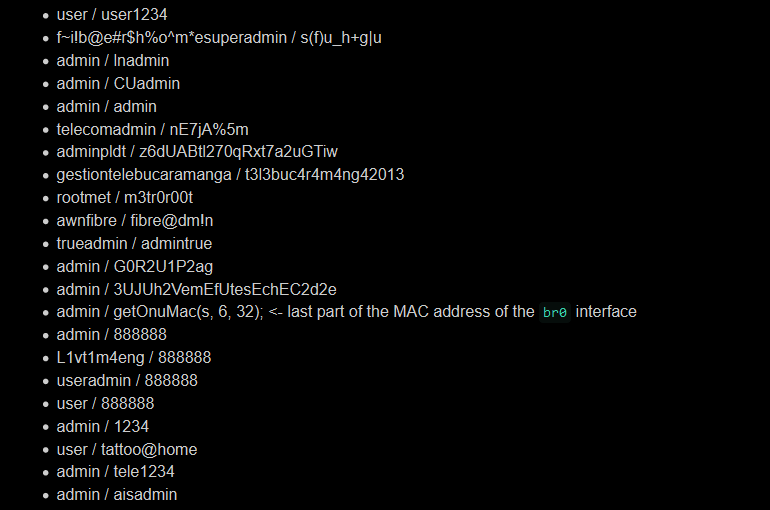
- The web server (control panel) contains 22 pairs of hard-coded credentials that Kim believes were deliberately added and used by various ISPs.
- the firmware contains hard-coded credentials to manage the device via TR-069;
- the encrypted web server binary also contains credentials, and the XOR key for decrypting them is also in the binary, which makes encryption useless. As Kim points out, this is the same XOR key that is used in the firmware of C-Data devices and also has similar backdoor problems;
- a hard-coded root password for the Telnet server was also found, although the server is disabled by default;
- In addition, the firmware includes various sets of hard-coded credentials for the low-level Telnet account (Kim found four pairs);
- a privilege escalation vulnerability in the Telnet daemon allows attackers to elevate their privileges to the root level;
- Telnet authentication can be bypassed in two different ways;
- You can use a denial-of-service error to completely fail Telnet.
- passwords from various router services are stored in clear text inside the firmware or in NVRAM.
Kim writes that he discovered all the listed bugs back in January 2020 and then notified the manufacturer about them, but he never received any response from the company. As a result, the researcher does not know if any of these vulnerabilities have been fixed, since he has not tested new versions of firmware.
The expert warns that these backdoors and vulnerabilities can affect other FiberHome Networks devices since most manufacturers use the same firmware or change it only slightly for different devices.
Let me remind you about the fact that Zyxel firewalls and VPN gateways contain a built-in backdoor.

