More than 100,000 Zyxel devices contain a built-in backdoor. They have a hard-coded zyfwp account with an unchangeable password.
An unauthenticated remote attacker could gain access to a vulnerable system via ssh or a web interface using hardcoded credentials and gain administrator privileges.<
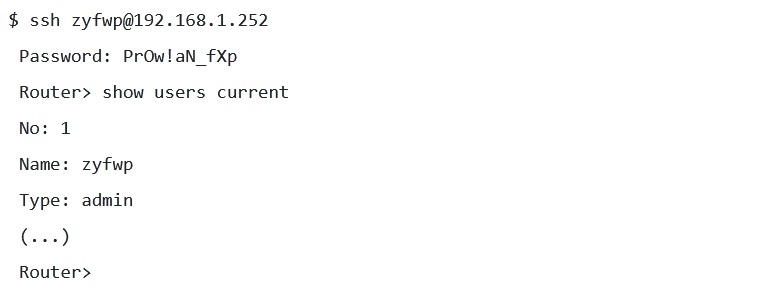
The vulnerability has a maximum severity level of 10 on the CVSS scale.
The vulnerability affects many of Zyxel’s popular business-class product lines, typically deployed on private corporate and government networks.
This includes the following devices:
- Advanced Threat Protection (ATP) series – used primarily as a firewall
- Unified Security Gateway (USG) series – used as a hybrid firewall and VPN gateway
- USG FLEX series – used as a hybrid firewall and VPN gateway
- VPN series – used as a VPN gateway
- NXC series – used as WLAN access point controller
Zyxel was notified about the issue at the end of November and partially fixed the vulnerability on December 18. The vulnerability was fixed in the ZLD V4.60 Patch1 firmware, and for the NXC2500 and NXC5500 access point controllers a patch will be released in April 2021.
The problem is aggravated by the fact that the VPN service and the web interface for device management use port 443 by default, which is why many users left port 443 open for external requests and, thus, in addition to the VPN connection point, they also left the ability to access the web. -interface. According to preliminary estimates, more than 100 thousand vulnerable devices with an open 443 port are available on the network.
Last year, Zyxel patched a critical vulnerability in its network attached storage (NAS), which has been already exploited by cybercriminals in real-world attacks.
Vulnerability CVE-2020-9054 could allow an unauthorized attacker to remotely execute arbitrary code. This allows an attacker to exploit the vulnerability by including certain characters in the username and injecting commands with web server privileges. It can then use the device’s built-in setup id utility to run commands with superuser privileges.
Let me remind you that I talked about the New Mirai malware version attacks Zyxel devices.

