Hackers are attacking a serious vulnerability in the popular Elementor Pro plugin for WordPress, which is installed on more than 11 million sites.
Let me remind you that we also reported that OptinMonster WordPress plugin lets to inject code into vulnerable sites, and also that Hackers Scanned 1.6 Million WordPress Sites Looking for a Vulnerable Plugin.Just as cybersecurity experts warned: About 30% of critical vulnerabilities in WordPress plugins remain unpatched.
The vulnerability discovered in March affects version 3.11.6 and all previous ones, allowing authorized users (shop buyers or site members) to change the resource settings or completely seize control over it.
The problem was discovered by NinTechNet researcher Jerome Bruandet on March 18, 2023, and the expert has already shared the technical details of the bug and how it can be exploited.
Bruande writes that the vulnerability is due to an access control violation on the WooCommerce plugin module (elementor-pro/modules/woocommerce/module.php), which allows anyone to change the parameters in the database without proper validation. That is, to exploit the vulnerability, the site must have a WooCommerce plugin installed that uses the corresponding vulnerable module in Elementor Pro.
The vulnerability is exploited through the vulnerable AJAX action pro_woocommerce_update_page_option, where input validation is poorly implemented and there is no capability check.
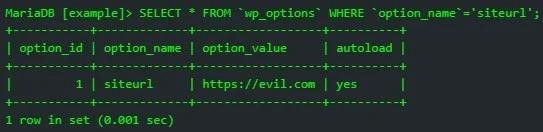
WordPress security firm PatchStack warned that hackers are already actively exploiting this vulnerability to redirect visitors to malicious domains (away[.]trackersline[.]com) or upload backdoors to hacked resources.
Experts say the backdoor was discovered while studying these attacks is called wp-resortpark.zip, wp-rate.php or lll.zip. Most attacks targeting vulnerable sites originate from three IP addresses: 193.169.194.63, 193.169.195.64, and 194.135.30.6.
Although details about the backdoors are still scarce, Bleeping Computer reports that a sample lll.zip archive contains a PHP script that allows a remote attacker to upload additional files to a compromised server.
Journalists emphasize that such a backdoor will allow an attacker to gain full access to a WordPress site, for example, to steal data or install additional malware.
All site administrators of sites that are using the Elementor Pro plugin should update to the patched version 3.11.7 or later as soon as possible (latest available version is 3.12.0). All previous versions are vulnerable.