Wordfence researchers discovered a massive campaign in which hackers scanned about 1.6 million WordPress sites.
The hackers were looking for a vulnerable Kaswara Modern WPBakery Page Builder plugin that allows to upload files without authentication.The fact is that the Kaswara Modern WPBakery Page Builder plugin was abandoned by the author some time ago, and after that they found a critical vulnerability CVE-2021-24284 in it. The bug allows unauthenticated attackers to inject malicious Javascript code onto websites, because due to the bug, any version of the plugin enables downloading and deleting files, which can ultimately lead to resource seizure.
Let me remind you that we also reported that Fake jQuery Migrate plugin infected many WordPress sites, and also that Due to vulnerability in File Manager plugin attacked millions of WordPress sites.
Scans work like this: attackers send a POST request to wp-admin/admin-ajax/php, trying to use the uploadFontIcon plugin’s AJAX function to upload a malicious payload (a ZIP file containing a PHP file).
This file, in turn, launches the NDSW Trojan, which injects JavaScript into legitimate files on target sites to redirect visitors to malicious resources, including phishing and malware sites.
Defiant analysts report that 1,599,852 unique sites have already been crawled, although only a small fraction of them actually used the vulnerable plugin.
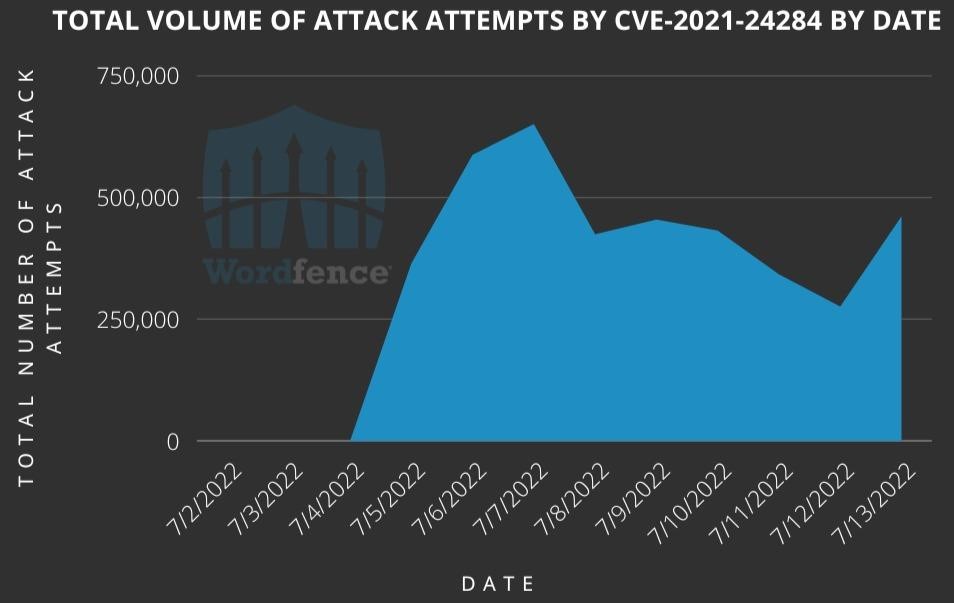
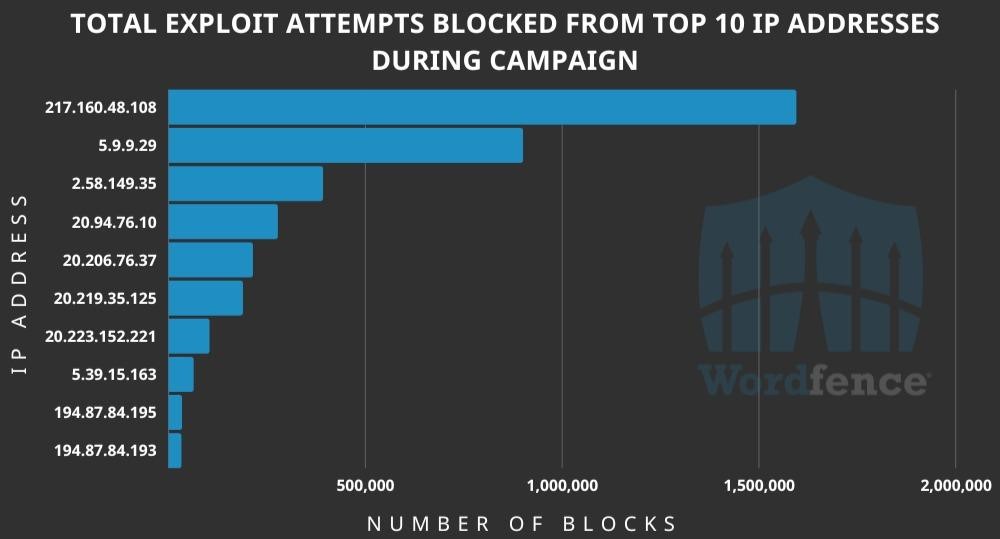
According to Wordfence telemetry, the attacks began on July 4 and continue to this day: on average, attackers make 443,868 scan attempts per day. At the same time, attacks come from 10,215 different IP addresses, with some of them generating millions of requests, while others show much less activity.
It is noted that attackers use the following file names for their ZIP payloads: inject.zip, king_zip.zip, null.zip, plugin.zip and ***_young.zip. These files, as well as the presence of the line “; if(ndsw==” in any of the JavaScript files indicate a compromise.
Anyone who still uses the Kaswara Modern WPBakery Page Builder plugin is advised to remove it from their site as soon as possible.

