The Midnight hacker group, recently discovered by information security experts, parasitizes on the attacks of other intruders.
Fake ransomware attempts to claim responsibility for attacks by extorting money from victims under the threat of revealing allegedly stolen data and DDoS attacks.Let me remind you that we also wrote that CyberWare group hackers attack scammers using ransomware, and also that More than 25 hacker groups work under the “Ransomware as a Service” model.
Information security experts say that Midnight activity began on March 16, 2023, when the group began attacking American companies. The group uses information about data leaks and company hacks to try to impersonate the organizer of these attacks.
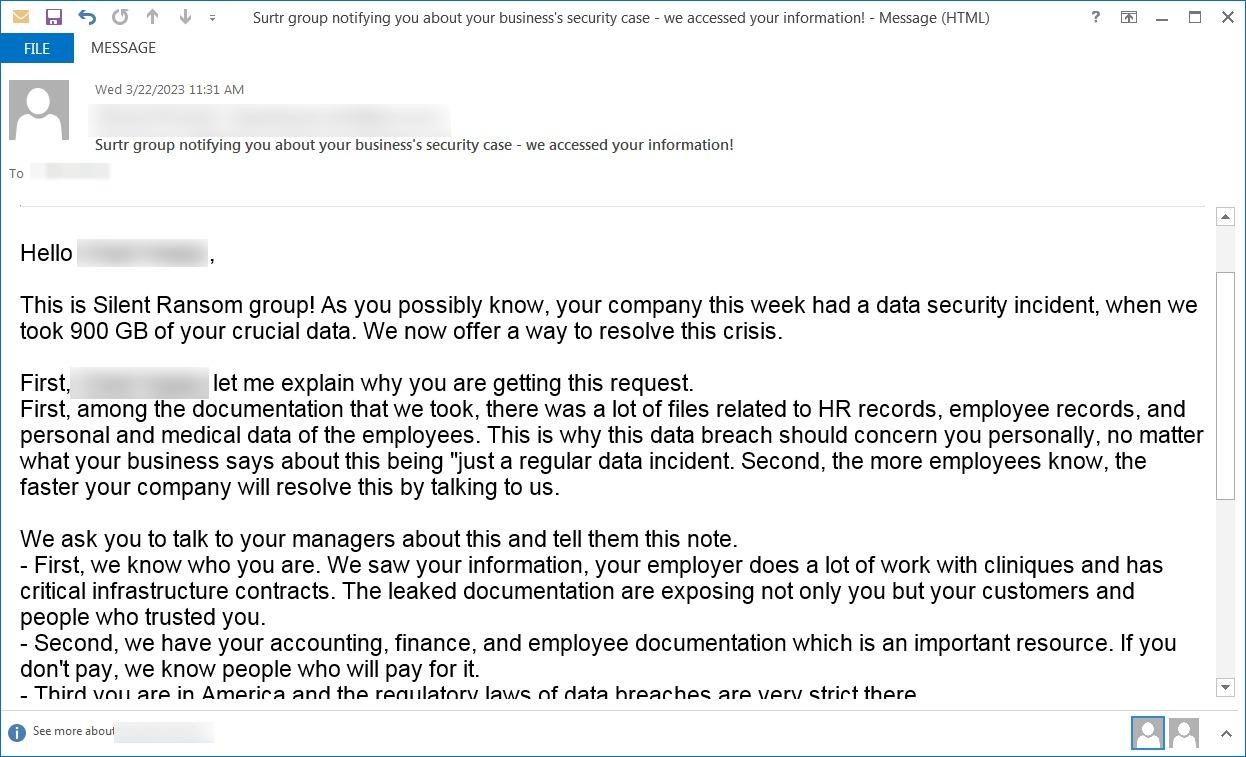
For example, in some letters, hackers claimed to be representatives of the Silent Ransom Group (aka Luna Moth), which had previously broken away from the Conti syndicate. At the same time, the name of another hack group, Surtr, was used in the subject of the letter.
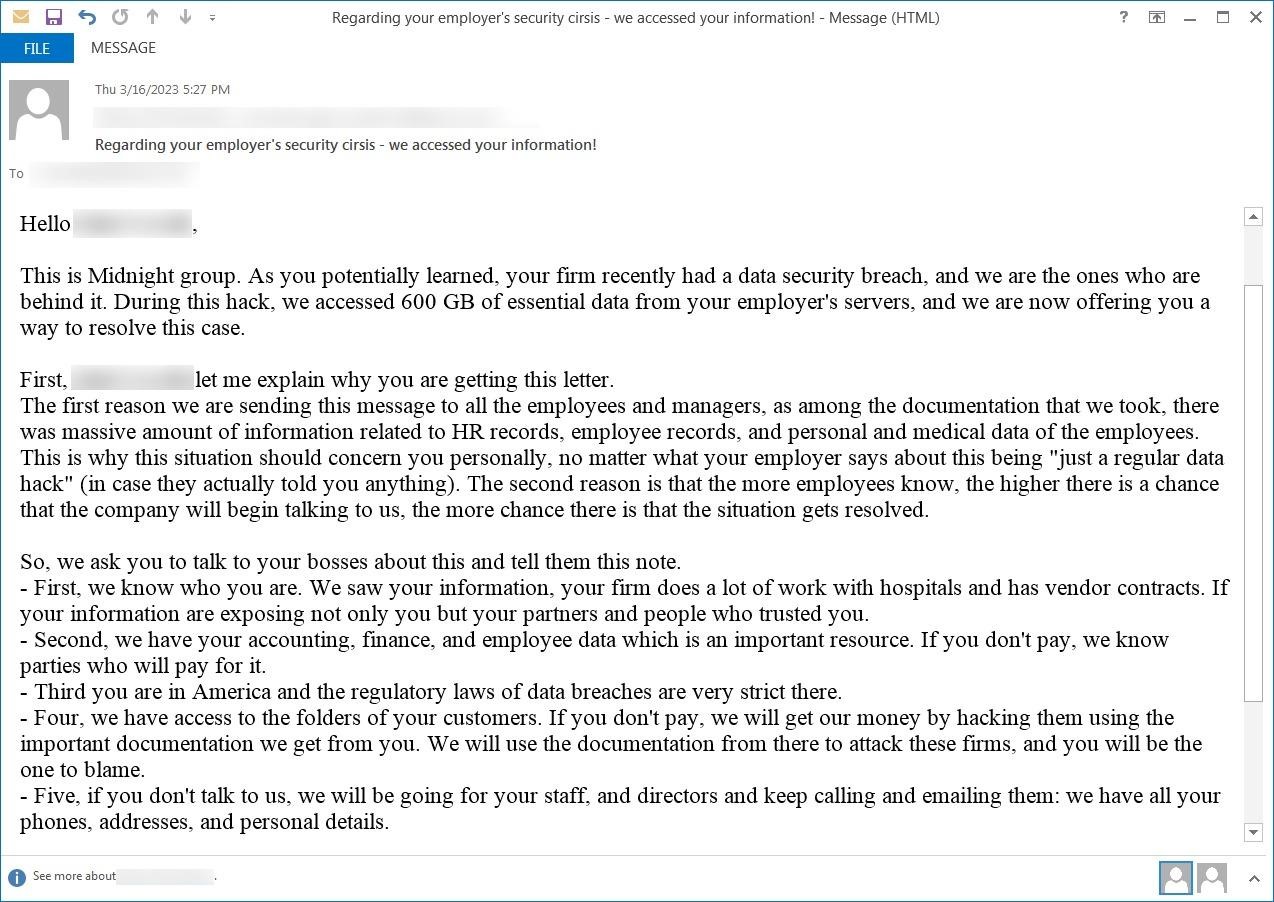
Bleeping Computer reports that another letter, written on behalf of Midnight herself, claimed that hackers had stolen 600GB of “critical data” from the victim company’s servers, and the message was addressed to a senior financial planner who had left the company six months earlier.
At the end of March 2023, analysts from the cybersecurity company Kroll spoke about such attacks. They noted that in some emails sent on behalf of the Silent Ransom Group, the hackers threatened their targets with DDoS attacks if they did not pay the ransom.
The researchers are calling this activity a “new wave of fake extortion attempts,” explaining that it’s not uncommon for attackers to use the names of better-known hacker groups to make their threats look more serious.
A report from another company, Arete, confirms Kroll’s observations about Midnight and also warns of more threatening emails that were sent out over the weeks leading up to March 24, 2023. Experts note that the Midnight group mainly targets organizations that have previously become victims of ransomware, including the QuantumLocker (renamed DagonLocker), Black Basta and Luna Moth groups.
According to the researchers, at least 15 of their current and previous clients received false threats from Midnight, where the scammers claimed data was stolen, accompanying their threats with vague details.
It’s not yet clear exactly how Midnight’s members select victims, but one option is to collect data from publicly available sources, including “leak sites” owned by other hack groups, social media, news reports, and incident reports.
At the same time, Arete notes that in some cases, fake hackers somehow learned about ransomware victims in advance, even when the information about the hacks was not yet publicly available. This probably indicates that Midnight is collaborating with other attackers. In addition, it is not uncommon for ransomware groups to sell data stolen from victims if they have been paid a ransom.
It is possible that the Midnight group has access to darknet marketplaces and forums where such data is traded, and this is how the scammers learn about the victims of other hackers who have not yet publicly reported cyberattacks.
Let me also remind you that the media wrote that Oakland Authorities Declared a State of Emergency Due to a Ransomware Attack.

Mujhe free fire hak sikhana hai