The popular OptinMonster WordPress plugin, installed over a million times, had a serious code injection vulnerability. The problem allowed an unauthorized party to gain access to the API, which ultimately led to the disclosure of sensitive information.
Vulnerability CVE-2021-39341 was discovered by Wordfence researcher Chloe Chamberland back in September this year. The fix was released on October 7, 2021, so users of the OptinMonster plugin are advised to update to version 2.6.5 or newer as soon as possible.The OptinMonster marketing plugin is used to integrate marketing tools and mailing systems into WordPress sites. Basically, it is a monetization and lead generation tool that has been deployed to a million sites due to its ease of use and many features.
The point is that OptinMonster’s capabilities depend on API endpoints, which provide seamless integration and simplify the workflow. However, the implementation of these endpoints is not always safe, and this is especially true for / wp-json / omapp / v1 / support.
This endpoint can expose data such as the full path to the site on the server, API keys used for requests, and more. An attacker who has obtained API keys is able to modify OptinMonster accounts, place malicious JavaScript on the site, and so on. Moreover, the vulnerable site will execute such code every time a visitor activates the OptinMonster element (pop-up window). Worse, the attacker would not even have to authenticate to the target site to access the API endpoint, since the HTTP request bypassed security checks under certain, easily met conditions.
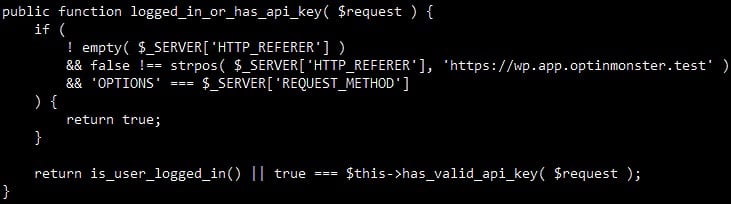
In his report, Chamberland summarizes that, in essence, the entire plugin API needs to be revised. Fortunately, the OptinMonster developers themselves agree with this, and have promised to fix other API issues in the next few weeks.
In the meantime, users are advised not only to update the plugin to a secure version, but also to generate new API keys, since all keys that could be stolen are revoked by the developers.
Let me remind you that we wrote that Zerodium offers up to $ 300,000 for WordPress vulnerabilities.

