Specialists from the Israeli Ben-Gurion University have developed a new method for extracting data from computers that are physically isolated from any networks and potentially dangerous peripherals. This time, the experts suggested using Serial Advanced Technology Attachment (SATA) cables, turning them into wireless antennas.
Machines isolated from any external influences are often found in government, military and corporate networks, and, as a rule, they store secret documents, as well as sensitive and confidential information. For many years, researchers have been coming up with various methods for extracting data from such secure devices, where everything is used, from LEDs to cooler revolutions (a list of studies can be found at the end of the text).Let me remind you that we also wrote that IPP port allows access to more than 80000 printers, and also that Windows 11 Security Approach: Zero-Trust Juggernaut Launched.
The new attack is called SATAn because it uses Serial ATA (SATA) cables. As is often the case, for a SATA attack to succeed, the attacker will first have to somehow infect the target machine with malware that will collect and prepare the necessary data for transmission. Although this is not an easy task, researchers leave its solution aside, focusing entirely on extracting information.
SATAn builds on the fact that SATA cables can transmit electromagnetic signals ranging from 5.9995 to 5.9996 GHz, which can match certain characters. The SATA interface is capable of generating radio signals during certain read and write operations. That is, a malware created by specialists intercepts legitimate software processes to perform read / write in a certain sequence in order to transfer stolen data.
During the study, the researchers successfully transmitted the word “SECRET” from an isolated machine to a nearby computer using electromagnetic signals. It is noted that the receiver in this case can be either a process on a neighboring computer or some hardware solution.
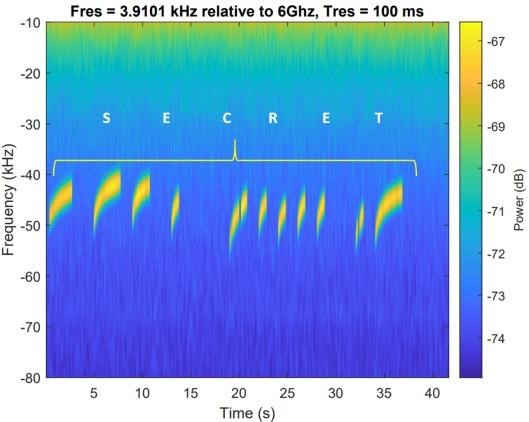
A demonstration of a successful attack can be seen in the video below.
The researchers write that experiments with various systems and settings have shown that the maximum distance from an isolated computer to the receiver cannot exceed 120 centimeters, otherwise the number of errors increases too much to guarantee data integrity (more than 15%).
The distance between transmitter and receiver affects the time it takes to send data. Depending on the distance, it took from 0.2 to 1.2 seconds to transmit a sequence of three bits. On average, data was transmitted at a rate of 1 bit/sec.
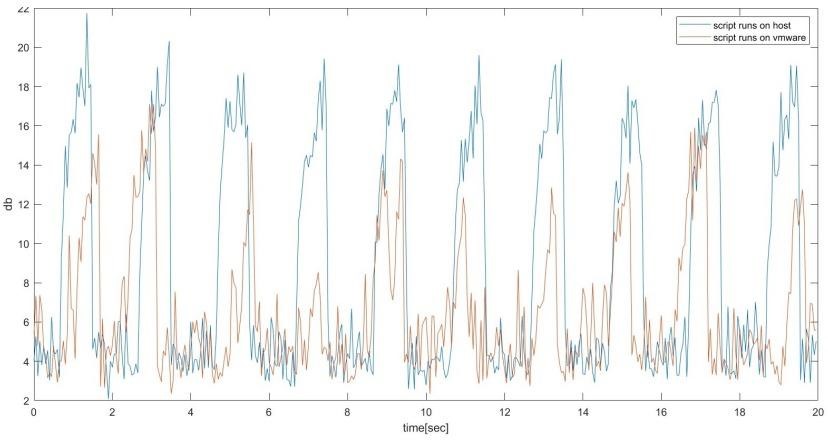
In addition, it has been observed that the signal quality on the SATA cable is significantly reduced if virtual machines are used for read/write operations.
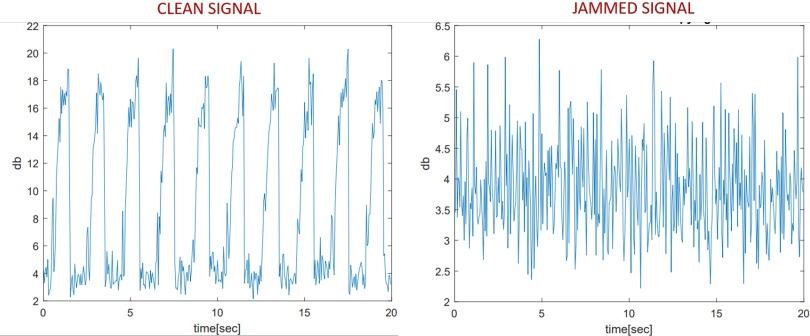
As a protection against such attacks, the study suggests using a SATA jammer that could monitor suspicious read / write operations and deliberately add noise to the received signal. However, experts admit that in reality it can be difficult to distinguish between legitimate and malicious transactions.
Among other developments of scientists from Ben-Gurion University, the following can be mentioned:
- USBee: turns almost any USB device into an RF transmitter for transmitting data from a secure PC;
- DiskFiltration: intercepts information by recording the sounds that the computer’s hard drive makes while the computer is running;
- AirHopper: uses the FM receiver in a mobile phone to analyze electromagnetic radiation emitted from a computer’s video card and turn it into data;
- Fansmitter: controls the speed of the cooler on the infected machine, as a result of which the tone of the cooler changes, it can be listened to and recorded, extracting data;
- GSMem: will transfer data from an infected PC to any, even the oldest push-button phone, using GSM frequencies;
- BitWhisper: uses thermal sensors and fluctuations in thermal energy;
- An unnamed attack that uses flatbed scanners and smart light bulbs to transmit information;
- HVACKer and aIR-Jumper: stealing data using CCTV cameras that are equipped with IR LEDs (infrared light-emitting diodes), as well as using them as a “bridge” to isolated networks of heating, ventilation and air conditioning systems;
- MOSQUITO: data extraction is proposed to be carried out using conventional headphones or speakers;
- PowerHammer: It is suggested to use normal power cables for data extraction;
- CTRL-ALT-LED: Caps Lock, Num Lock and Scroll Lock diodes are used to extract information;
- BRIGHTNESS: extracting data by changing the brightness of the monitor screen;
- AIR-FI: RAM is used as an improvised wireless emitter for data transmission.
A more complete list of research papers by experts on the compromise of isolated machines can be found here.