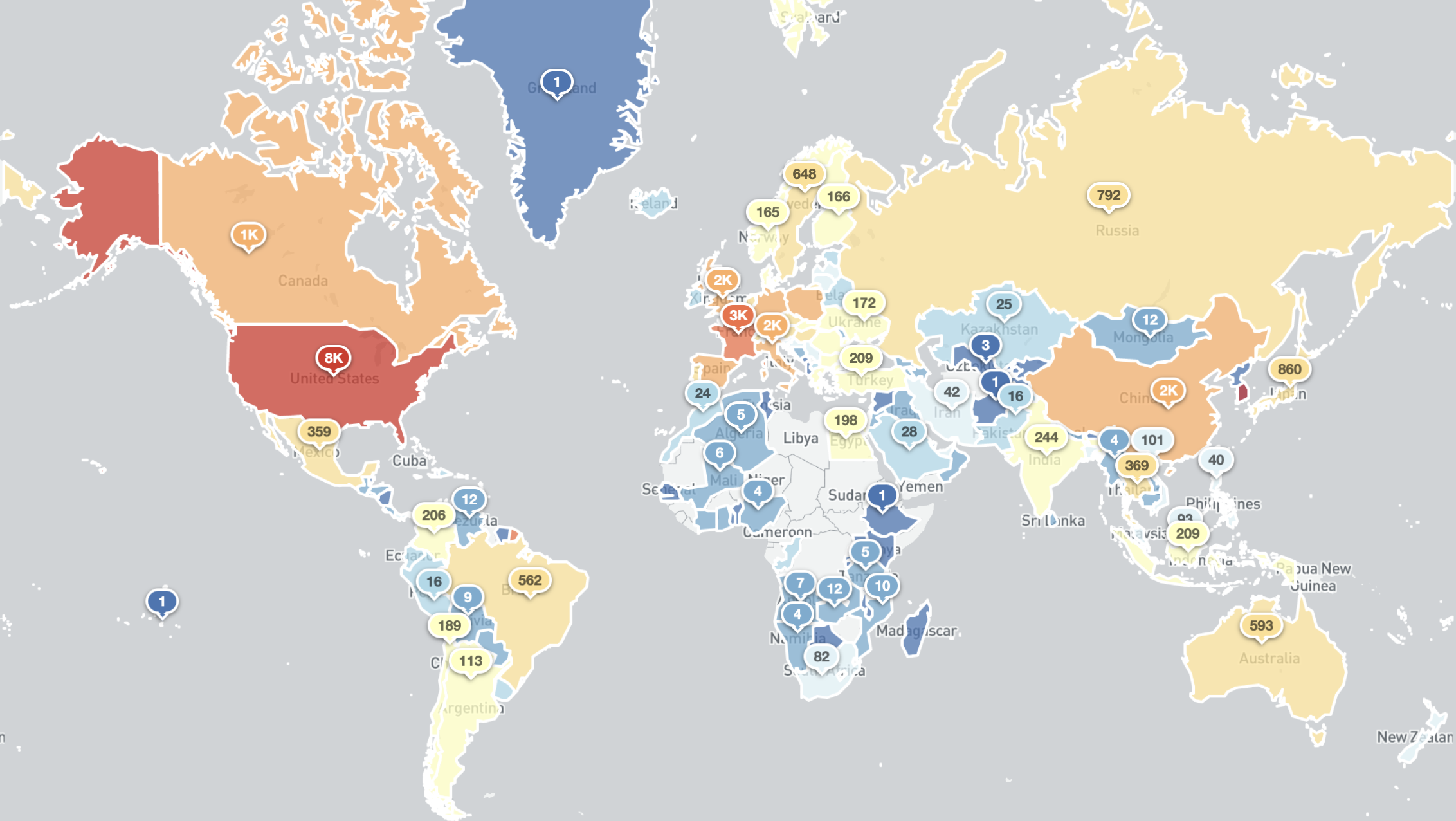
Experts from the non-profit organization Shadowserver Foundation issued a warning, in which again recommend companies do not leave printers in public access via Internet. According to them, IPP port allows access to more than 80,000 printers.
For their research, experts scanned four billion IPv4 addresses looking for printers with an open IPP (Internet Printing Protocol) port. As the name implies, this protocol allows users to manage printers connected to the Internet and remotely send them printing tasks.The difference between IPP and many other printer management protocols is that IPP is a secure protocol that supports access control lists, authentication, and encrypted connections. Unfortunately, this does not guarantee that device owners will actually use any of these features”, – say the researchers.
According to the Shadowserver Foundation, they specifically searched the Internet for IPP-enabled printers, but without firewall protection that would allow attackers to request local data using the Get-Printer-Attributes function.
According to experts, as a rule, every day they find about 80,000 printers available online through the IPP port. This number is approximately one-eighth of the total number of IPP-enabled printers connected to the Internet. In conventional scanning using the BinaryEdge search engine, between 650,000 and 700,000 devices with an available IPP port (TCP/631) are detected daily on the network.
Open IPP ports (without a firewall and authentication) result in several problems. So, this port can be used to collect information. Many IPP-enabled printers are willing to provide additional information about themselves, including the device’s name, location, model, firmware version, organization name, and even Wi-Fi SSID.
Attackers can collect this information and then use it to find corporate networks for future attacks”, – warn the researchers.
In addition, about a quarter of the total number of IPP printers (about 21,000) also provide information on their brand and model. The disclosure of such information can greatly facilitate the process of discovering groups of specific devices that are vulnerable to certain problems.
Tools for hacking printers through IPP are not at all difficult to find on the network. Solutions such as the open source PRET (Printer Exploitation Toolkit) were already used in the past to mass-hack printers, after which they were ordered to print arbitrary messages. Moreover, in theory, the toolkit can be used for more serious attacks, for example, to completely seize control of vulnerable devices.
Specialists of the Shadowserver Foundation plan to publish daily reports on devices available through IPP on their website. They hope this helps to draw attention to the problem and, ultimately, leads to a reduction in the number of public IPP-enabled printers.
Let me remind you that recently specialists from the Israeli company JSOF discovered 19 vulnerabilities, united by the name Ripple20. Millions of printers and IoT devices are vulnerable to these vulnerabilities.