Recent research of SecurityDiscovery uncovers a data breach of a yet-unseen scale. An unnamed database, that primarily consists of data from other leaks, contains more than 26 billion records. For unprecedented scale and the inclusion of dozens of different sources, it got the nickname of Mother of All Breaches (MOAB).
Mother of All Breaches: The Biggest Data Leak
A research of SecurityDiscovery’s analyst Bob Diachenko uncovers a collective database that contains over 26 million entries – more than triple the population of the Earth. The creator/owner of the database is to be discovered, though researchers do not think there is a chance to find one. Obviously, anyone who paid so much attention to leaked data has a clue on how to protect their own privacy.
Further investigation showed that Mother of All Breaches consists of not only publically leaked databases, but also records that appeared only in private databases that are not for sale. This can mean two things – either this collector has powerful connections in the cybercrime world or it was able to hack into hackers’ computers. Either way, every single row of the data from this mega-leak was obtained in an illegal way.
This sounds even worse after having a peek on the exact contents of the database. Most of it is login credentials to different online services, but some of those records are accompanied by more sensitive data. However, SecurityDiscovery does not uncover the exact contents of the database, possibly to avoid increased attention from cybercriminals. Like if the number of records was not enough🤷♂️.
26 Billion Records Data Leak Gathers Data From Hundreds of Companies
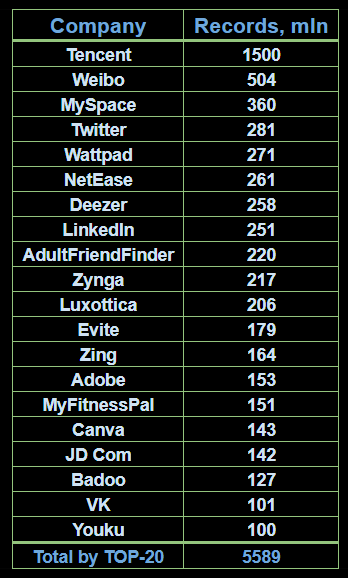
Obviously, that’s no way to get the database this big with only a few sources. Researchers report about dozens of companies included to the list, with TOP-20 companies forming a pool of almost 5.6 billion records. Still, the counter decreases in a rather slow manner, so the potential TOP-30 will likely exceed the population of our planet.
The metrics of the world’s population is useful in one more place – it clearly shows that the database contains a lot of duplicate data. By simple math we can assume 3 records for each of 8.1 billion people on the globe. Though, not each and every person was hacked, and not everyone uses the Internet, so this number may be all the way up to 7..10 duplicates per record. Those are just my own eye-balling suppositions though, the only way to know the truth is to take a look at the Mother of All Breaches itself.
Cybernews, who took their part in the investigation, promised to add the MOAB to their data leak check service. Their system works for quite some time now, but has “only” 15.5 billion records at the moment. Increasing this amount twinfold will definitely make their results more accurate, even considering the number of spare records.
How to protect data from leaking?
There are two courses of action to consider when you are trying to avoid data leaks – proactive and reactive. The important thing about both tho is that all the measures are most effective when applied simultaneously. By taking one here, one there you will possibly secure some stuff, but will not be even remotely close to the full efficiency.
For proactive (a.k.a. preventive) protection:
Avoid oversharing. It is possible to collect quite a selection of facts about a person by simply scrapping it from social media. If you care about your privacy, try to share less sensitive information in publicly accessible posts. Disabling automated geo-tagging or face recognition goes there, too.
Change passwords regularly & employ 2FA. This advice is more about common sense, but it anyways protects you from data breaches even before you acknowledge they happened. As there are plenty of password storage solutions available, it’s not a big deal to generate new passwords once a quarter and remember them all. Twin-factor authentication will give you an additional layer of security, for the situations when someone will haste to use your leaked password to hijack the account.
Do not use your regular email and real data on questionable websites. Once you are not sure about the webpage, that will be less than ideal to trust it with all kinds of your personal data. It is not advisable to share date of birth, current location, hobbies etc. when the site security is not awesome.
Track the security news to know about the latest breaches. This will help you to understand the current state of things and see the latest changes on the cybersecurity landscape.
To react to the breaches you uncover:
Change your password immediately. A thing all data breaches leak at the first place is login credentials. As I’ve mentioned above, it is a good practice to change them once in a while, but the data leak is a reason for the urgent change.
Check if other data is leaked on a dedicated service. When it rains, it pours; after hacking one service adversaries can try attacking another using the credentials obtained from the previous attack. There are plenty of services that offer you to see whether your info was exposed in a data breach. This will give you an awesome clue about other places to improve the security on.