In a concerning development, cybersecurity experts have detected active exploits (RCE) flaws in Atlassian Confluence. The vulnerability poses a severe threat due to the possibility of remote code execution. Atlassian has acknowledged the vulnerability affecting versions released before December 5, 2023.
Confluence RCE Vulnerability Under Active Exploitation
Atlassian Confluence is a web-based enterprise wiki that usually acts as a source of internal information about the products and technologies. The vulnerability tracked as CVE-2023-22527 was disclosed by Atlassian back in August 2023. It impacts outdated Confluence Data Center and Server versions. This flaw, marked with the highest CVSS score of 10 due to the potential it gives to attackers. Using it, they can achieve remote code execution (RCE) without authentication, and the exact exploit for the flaw is pretty easy to create.
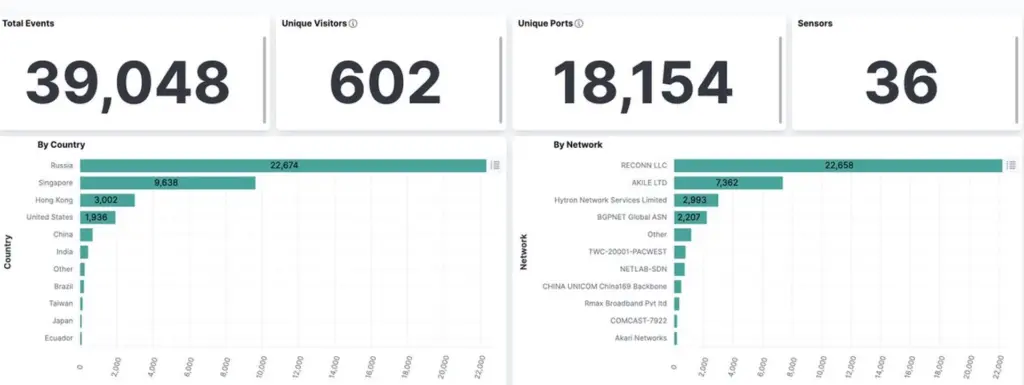
Report of Shadowserver
Shadowserver, a threat monitoring service, reported observing over 39,000 attempts to exploit this vulnerability, originating from more than 600 unique IP addresses. The vast majority of these attempts were detected in a short span.
The vulnerability affects out-of-date Confluence Data Center and Server versions released before December 5, 2023. Versions 8.0.x to 8.5.3 are particularly impacted.
Historically, this is not the first vulnerability in Confluence, and in general Atlassian software is often exploited. We have already written about Trojans that mined crypto through vulnerabilities in Confluence.
Attack Mechanism in Details
CVE-2023-22527 is classified as a template injection vulnerability. Template injection occurs when user input is insecurely included in a template, allowing an attacker to inject malicious code.
Exploitation Process:
- The aggressor sends a specially crafted request to the vulnerable Confluence server. Request typically includes malicious code or commands.
- The malicious input is inserted into a template, which is processed by the server. Since the input is not properly sanitized or validated, it allows the attacker to manipulate the template processing.
- The injected code is executed by the server. This can result in remote code execution (RCE), where the attacker gains the ability to execute arbitrary commands on the server.
- Atlassian Confluence servers, often used to store sensitive information like code and architectural diagrams, have become a lucrative target for cybercriminals. This vulnerability opens the door for a range of malicious activities, including data theft, ransomware attacks, and more.
Atlassian Offers CVE-2023-Patch
To address this vulnerability in Atlassian Confluence, a critical patch has been released. That update is crucial for mitigating the risk posed by the template injection flaw that enables unauthenticated remote code execution.
The specific fixed versions for Confluence Data Center and Server are 8.5.4 (LTS), 8.5.5 (LTS), 8.6.0 (Data Center Only), 8.7.1 (Data Center Only), and 8.7.2 (Data Center Only). It’s important to note that versions starting from 8.6 support only Data Center licenses.
Confluence LTS Version 7.19.x is not affected by the CVE-2023-22527 vulnerability. However, Atlassian advises upgrading to the latest release (version 7.19.18) to safeguard against other vulnerabilities.
Safety Tips
Security experts are urging those with vulnerable Confluence instances to treat them as compromised until proven secure. Organizations are advised to immediately upgrade their Confluence servers to the latest patched versions. In addition to patches, you should increase your vigilance by looking for new threats, reading cyber news, checking logs, and continuously monitoring your systems.
It is important to note that Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR) systems can be highly effective in managing vulnerabilities like CVE-2023-22527. These systems aid in early detection of malicious activities, provide tools for quick response to threats, and offer comprehensive coverage across various data sources.

