The researchers have uncovered a new-old tactic used by cybercriminals. Frauds are distributing XMRig CoinMiner malware under the guise of cheats for popular games. As using cheats and hacks requires mandatory disabling protection systems, the effectiveness of this approach is rather high.
XMRig CoinMiner Spreading Via Game Hacks
Specialists from AhnLab SEcurity Intelligence Center (ASEC) have discovered a new campaign that spreads XMRig coin miner. According to their research, the malware is distributed in the form of hacks for popular games via special-themed websites. Such a mass spreading is not typical for this malware type, as they usually opt for the deployment through active dropper botnets.
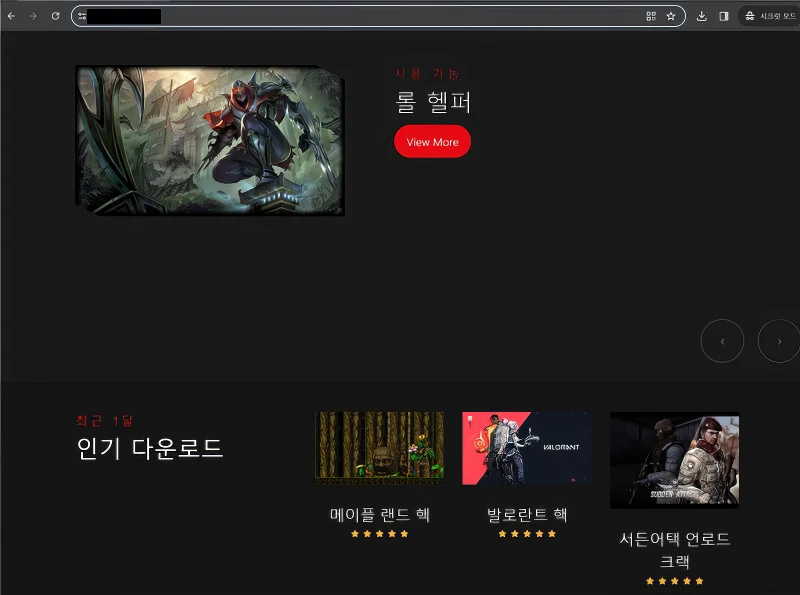
The website with hacks for games (source: ASEC)
Such a strategy pick is excellent for attackers, as using cheats and hacks requires the mandatory disabling of security tools. Aside from antivirus software, frauds also instruct users on how to circumnavigate browser built-in protection measures. Although this tactic is as old as the world, it still works just fine. On the other hand, isn’t it a fair punishment for those who want to gain an advantage by unfair means?
XMRig in Cheats – How Does That Work?
The scheme starts with attackers placing a malicious file in an archive and positioning it as a hack for the game. Since using cheats and similar tools is illegal, antiviruses and web browsers try to prevent such files from being downloaded. To avoid this, the authors of the malware attach a special guide. It describes in detail how to disable blocking the malicious file download and how to disable malware protection. In addition to the main file, the archive contains a particular application, dControl.exe, which, as the name implies, disables the Windows Defender.
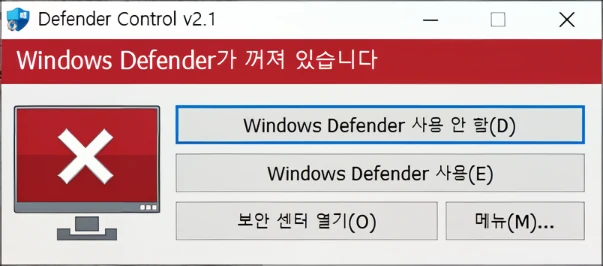
dControl tool that disabled Windows Defender. Source: AhnLab
The next step is to load CoinMiner via loader.exe, a program created with AutoHotkey. This program installs the malware in the temporary system folder “%temp%\“. CoinMiner then modifies critical system files by adding to Windows Defender exceptions. It uses PowerShell to disable scanning of executable *.exe files in the ProgramData folder. It also removes the Windows Malicious Software Removal Tool (MSRT) update and changes the hosts file.
The malware then copies itself to the %ProgramData%\Google\Chrome folder and signs itself as updater.exe. It also registers under the legitimate GoogleUpdateFile service, thereby gaining a foothold in the system. Now, nothing prevents the malware from using the machine’s resources to mine cryptocurrency. By the way, this slows down the device and can destroy the PC hardware in the long run.
Recommendations
In most cases, to avoid infecting your system with a miner, you should not download executable files from questionable sources. In this case, it is enough to play fair. The main rule here is don’t disable security software, regardless of who and why asks for this. 99% of cases, following such instructions will lead to malware installation. Another advice is to play honestly – cheats, hacks and similar software are among the most popular choices for hackers to spread malicious software.
The best way to stop any malware from infiltrating your system is to use proper anti-malware software. GridinSoft Anti-Malware is the program you can rely on: with its powerful proactive protection and network security module, it will intercept any malicious elements at their very beginning.