Last week, attacks on Western Digital NAS removed all files from WD My Book Live devices, while users could not log in through a browser or app, receiving an “Invalid Password” error.
Then the developers asked the NAS owners to temporarily disconnect their devices from the Internet.Western Digital engineers reported that, in their opinion, the devices could be compromised using a certain vulnerability, since they were connected to the Internet directly. At the same time, the last firmware update for WD My Book Live was released in 2015, and after that a critical bug CVE-2018-18472 was discovered, for which an exploit immediately appeared. As a result, many decided that this particular vulnerability was used in the attacks, but everything turned out to be not so simple.
Censys experts now report that the latest firmware for My Book Live contained a zero-day vulnerability, identified as CVE-2021-35941, which allows a remote attacker to perform a factory reset.
Whereas a typical procedure like this through the remote administration console requires an administrator to be authenticated, the system_factory_restore script commented out the authentication checks, allowing anyone with access to the device to perform a reset. This problem was exploited by unknown users last week.
One of the payloads of this campaign was uploaded to VirusTotal, and Doctor Web is tracking it as Linux.Ngioweb.27. It is a well-known Linux botnet targeting IoT devices.
Another payload was also spotted in the attacks, but it is not yet clear which malware family it belongs to. As a result, My Book Live devices can be used to carry out DDoS attacks, execute commands, or steal files.
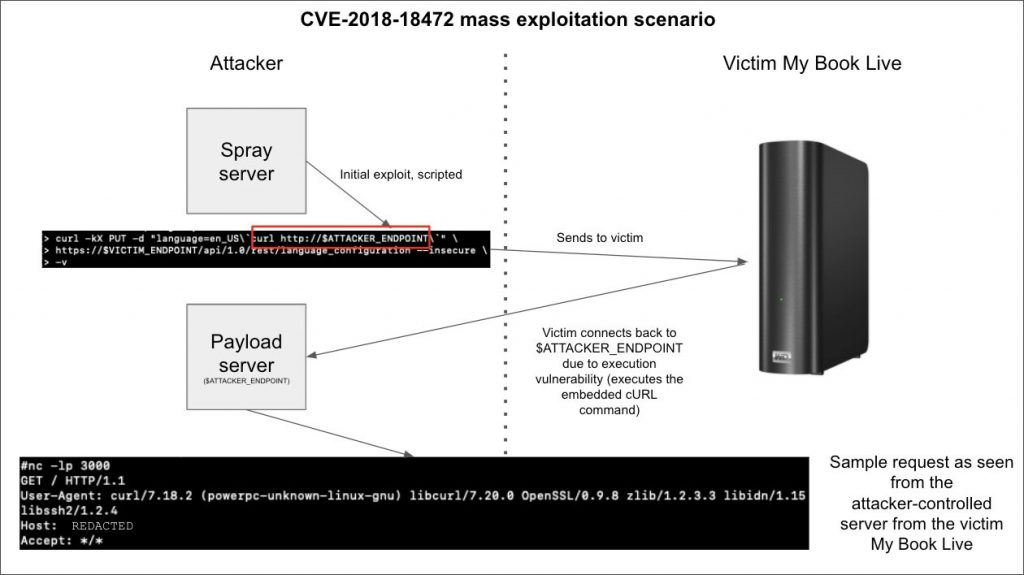
Interestingly, in this case, the botnet operators protect their scripts with passwords to prevent rival botnets and other hackers from taking over the NAS. Because of this, cybersecurity specialists have a theory that recent attacks with a factory reset may be associated with the activity of this botnet.
The point is that erasing data could be the work of rival botnet operators, who sought to reboot devices in order to take control of it, or simply annoy rivals, rendering the NAS useless.
It is worth noting that representatives of Western Digital have already announced that the company will provide data recovery services to all victims.

