Colombian police in the country’s capital, Bogota, have arrested Romanian citizen Mihai Ionut Paunescu, supposedly one of the developers of Gozi malware.
In December 2012, Paunescu was already arrested in Romania, and in January 2013 the US authorities charged him with playing a decisive role in the spread of Gozi malware, which stole bank credentials and allowed its operators to steal funds from other people’s accounts.The US prosecutor’s office argued that Paunescu, known online as Virus, ran PowerHost[.]ro, provided bulletproof hosting services to malware developers, intentionally did not cooperate with the authorities and helped criminals protect their C&C infrastructure.
Although Paunescu hosted several hack groups at the time, including the creators of Zeus and SpyEye, authorities said he worked very closely with the authors of the banking Trojan Gozi. According to them, Paunescu was one of the three main members of the group and was responsible for the explosive growth of the Gozi botnet, which infected more than 500,000 computers between 2007 and 2013. Allegedly, after Paunescu joined the group in 2010, Gozi 2.0 was released.
Now, after Paunescu has been detained in Colombia, US officials have said they plan to try again. If extradited and convicted in the United States, Paunescu could face up to 65 years in prison.
It should be noted that other Gozi authors have already been punished. In 2016, Russian citizen Nikita Kuzmin was sentenced to 37 months in prison in the United States, but at the time of sentencing, Kuzmin had already spent that time behind bars awaiting a hearing. As a result, he was released from custody right in the courtroom, and remained obliged to pay a fine of 6,900,000 dollars to cover the losses caused by the Trojan.
Also in January 2016, Latvian citizen Denis Chalovsky, who created web injections for Gozi, was released. The court sentenced him to 21 months in prison, but while awaiting the hearing, Chalovsky also served his sentence.
Interestingly, the Latvian authorities refused to extradite him to the United States because of the too harsh punishment, which could be up to 67 years in prison.
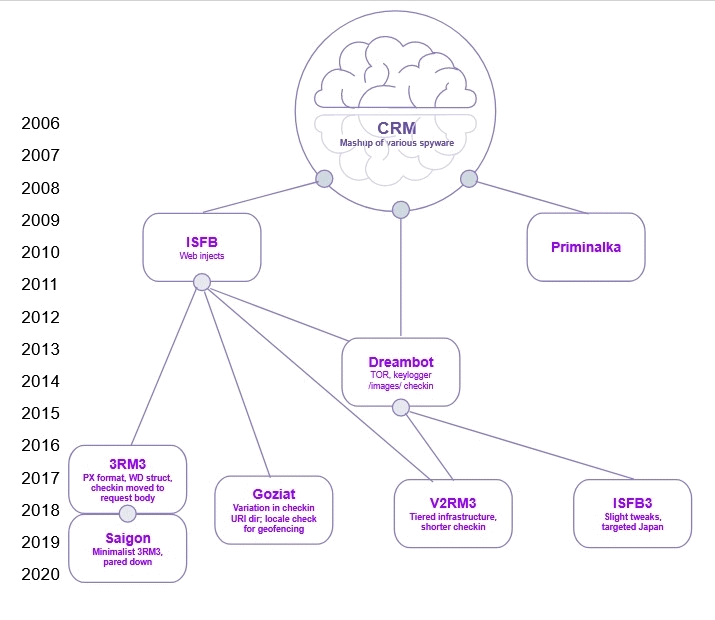
Let me remind you that in January 2013 the malware’s source code was leaked and now underlies many banking Trojans, including Gozi Prinimalka, Gozi ISFB, Gozi CRM, Schnitzel Gozi, Goziv3, Neverquest, Rovnix, Vawtrack, Tepfer, Dapato, Ursnif, etc.
Let me remind you that we also wrote that Law enforcement officers arrested GandCrab ransomware operator in Belarus.