Experts from Amnpardaz and SentinelOne concluded that in early July, the Iranian railway system was attacked not by an encryptor, as previously assumed, but by a wiper, deliberately destroying data.
The attack took place on July 9, 2021. According to local media reports (1, 2, 3), the system used to manage train timetables and ticket services is out of order. Because of this, many trains were cancelled and others were delayed.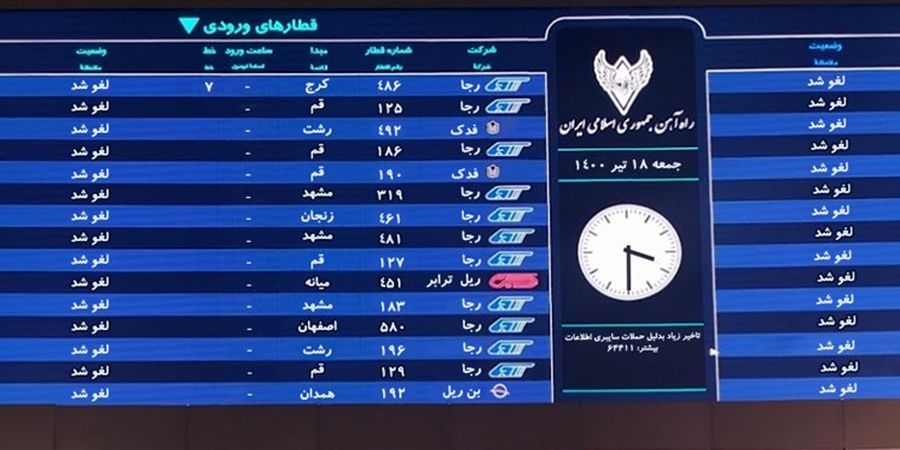
Officials initially described the incident as a technical problem, denying the cyberattack. They stated that passenger and freight trains ran as usual with some delays, and staff manually managed the timetable. However, later the Iranian authorities confirmed the fact of the attack, as photos of blocked computers belonging to the Ministry of Roads and Urban Development of the country got on the network.
The malware used for this attack was dubbed Meteor, and SentinelOne experts emphasize that this malware was not previously detected.
According to the company’s analysis, Meteor was one of three components of this attack, which consisted of the following parts:
- Meteor – a wiper that erases the file system of an infected computer;
- the mssetup.exe file, which played the role of a good old screen lock and blocked the user’s access to the computer;
- file nti.exe, which rewrote the MBR of the victim’s computer.
It is not known exactly how the attack began, or what served as an entry point for the hackers. However, it has already become clear that, having penetrated the network, the attackers used group policies to deploy malware, delete shadow copies, and disconnect infected hosts from local domain controllers so that system administrators could not quickly cope with the consequences of the attack.
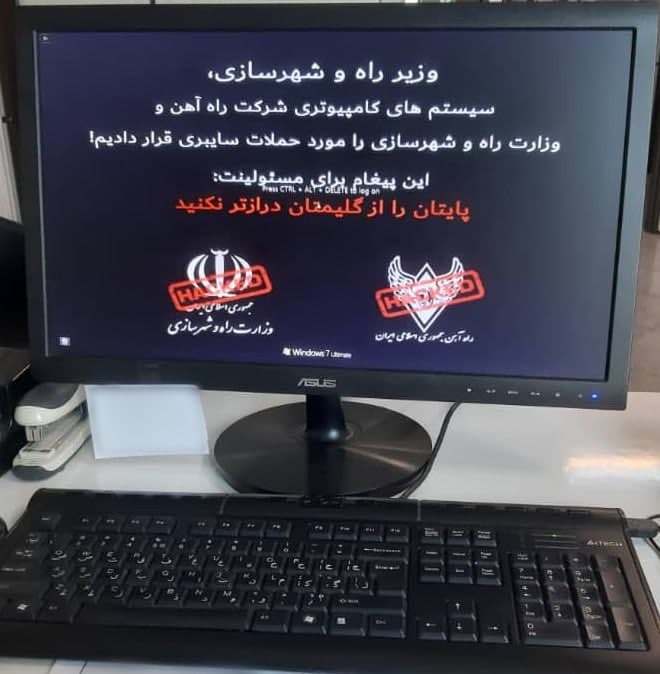
After the completion of the above actions, the file system was destroyed on the infected computers, and a message was displayed on their screens, in which the victims were asked to call the phone number belonging to the office of the Supreme Leader of Iran, Ayatollah Ali Khamenei .
Meteor’s technical analysis reveals that the malware contained a “fancy mix of code”, where open source components coexisted with old software and specially written custom parts that “were replete with health checks, bugs, and demonstrated redundancy in achieving their goals.”
According to the researchers, some parts of the malware were written by an experienced and professional developer, and the very chaotic nature of the attack indicates that the operation could have been organized in a hurry, and several teams were working on it.
SentinelOne writes that it is not yet clear whether Meteor was created only for this operation or in the future this malware will also be used in other cyberattacks.
Let me remind you that we wrote that Iranian hackers attack VPN-servers to install backdoors, as well as that Iranian low-skilled hackers are quite successful in “playing” with Dharma ransomware.

