Government sponsored Iranian hackers allegedly attack VPN-servers and exploit vulnerabilities in them to create backdoors in companies around the world during their malicious campaigns.
According to Israeli company ClearSky specialists report, Iranian hackers are attacking enterprises in the field of information technology, telecommunications, the oil and gas industry, aviation, and state-owned companies.We estimate this campaign to be among Iran’s most continuous and comprehensive campaigns revealed until now. Aside from malware, the campaign enfolds an entire infrastructure dedicated to ensuring the long-lasting capability to control and fully access the targets chosen by the Iranians. The revealed campaign was used as a reconnaissance infrastructure; however, it can also be used as a platform for spreading and activating destructive malware such as ZeroCleare and Dustman, tied to APT34”, — write ClearSky researchers.
According to experts, “Iranian APT groups have good technical capabilities to carry out attacks and are able to use the so-called 1-day vulnerabilities in relatively short periods of time after they are discovered.” In some cases, criminals exploited vulnerabilities in VPN services for several hours after the publication of information about them.
In 2019, Iranian criminals exploited vulnerabilities discovered in Pulse Secure “Connect” VPN (CVE-2019-11510), Fortinet FortiOS VPN (CVE-2018-13379) and Palo Alto Networks “Global Protect” VPN (CVE-2019-1579) servers. Attacks on these systems began last summer and continue in 2020. The main objectives of the attackers were penetration of corporate networks, moving through internal systems and installing backdoors for future use.
The most successful and significant attack vector used by the Iranian APT groups in the last year has been the exploitation of known vulnerabilities in systems with unpatched VPN and RDP services, in order to infiltrate and take control over critical corporate information storages”, — report ClearSky specialists.
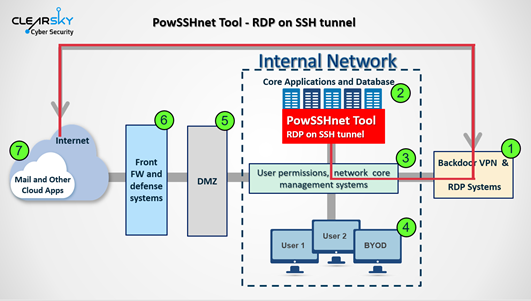
Attackers abuse Sticky Keys to gain administrative privileges on Windows-based systems, use the tools JuicyPotato and Invoke the Hash, as well as legitimate system administration software like Putty, Plink, Ngrok, Serveo or FRP.
As part of the attacks, criminals use the following tools: STSRCheck (to detect open ports), POWSSHNET (for tunneling via RDP via SSH), custom VBScripts scripts to download TXT files from a C&C server and merge them into an executable file and Port.exe (tool for scanning IP addresses of predefined ports).
Researchers suggest that at least three Iranian groups stand behind attacks on VPN servers around the world, namely APT33 (Elfin, Shamoon), APT34 (Oilrig) and APT39 (Chafer). We already talked about the methods of some of these groups – for example, APT33 distributed Quasar RAT through fake resumes.