Cyble researchers recently discovered a malware called “Invicta Stealer” on the Internet and published their report on it.
This malicious software is capable of collecting various data from infected computers, including information about the system, hardware, wallets, browsers, and applications.Let me remind you that we also talked about the fact that Sources of Rust-Written Luca Stealer Malware Published on Hacker Forums, and also about Vidar Stealer. What is Vidar Malware?.
Security specialists also talked about: Top 3 Stealer Malware to Be Aware Of in 2023
The creator of the infostealer offers to buy it for everyone, in connection with which he actively advertises his creation in Telegram and YouTube, boasting of its ability to steal information.
The main method of distribution of Invicta Stealer is spam mailing, which imitates letters from GoDaddy with an offer to return money for services rendered earlier. The email contains a phishing HTML page that contains a link that redirects the victim to the Discord URL.
There, the download of the “Invoice.zip” file is instantly initiated. Everything happens so fast that an inexperienced user does not even notice that the download of the archive has taken place from an unofficial site.
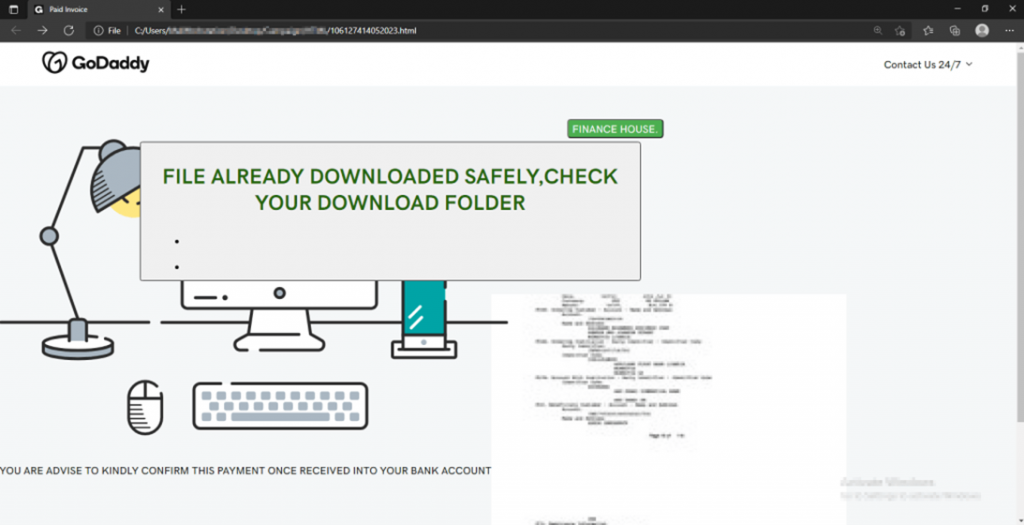
Phishing HTML page imitating the GoDaddy website
Inside the archive there is a shortcut file “INVOICE_MT103.lnk”, the icon of which looks like a PDF file. The shortcut runs a PowerShell command to download and execute an HTA file with VBScript code. This code, in turn, runs another PowerShell script that downloads and runs Invicta Stealer.
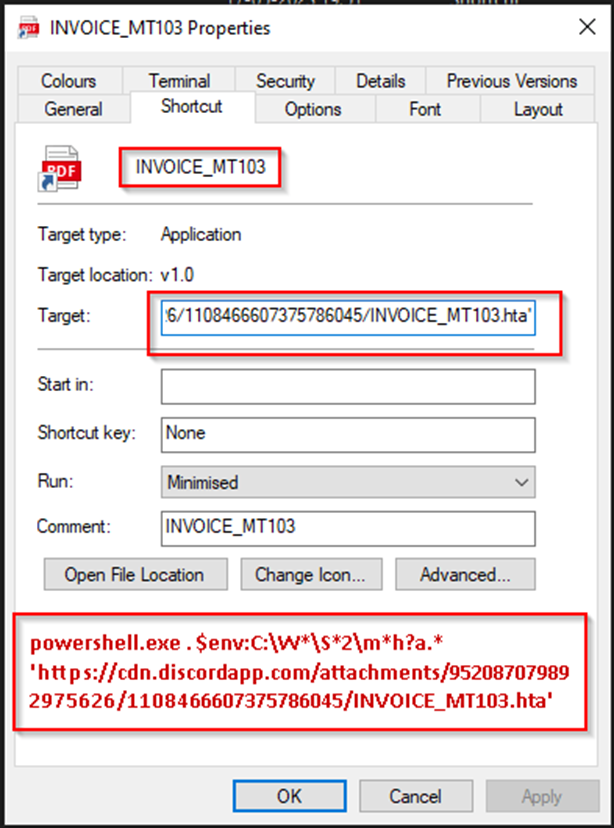
Label with malicious code
Once launched, Invicta Stealer collects a lot of data about the system and equipment of the victim: computer name, username, time zone, system language, OS version, list of running processes, list of installed programs, amount of RAM, number of processor cores, screen resolution, device ID, IP address and geolocation.
In addition, the cyberthief steals data from a long list of browsers (31 web browsers) and then targets cryptocurrency wallet extensions (26 extensions), including: ARK Desktop Wallet, Armory, Atomic, Binance, Bitcoin, CloakCoin, Coinomi, Daedalus Mainnet, Dogecoin, Electrum, Electrum-LTC, Electrum-Smart, ElectrumG, Exodus, Exodus Eden, Guarda, Jaxx Liberty, Litecoin, MultiBitHD, Nano Wallet Desktop, Neblio, Neon, Scatter, VERGE, WalletWasabi, Zcash.
Next, the thief collects data from several specific applications. Among them:
- Steam – retrieves active game sessions, usernames, list of installed games;
- Discord – extracts local databases;
- KeyPass – Retrieves the local database of encrypted passwords.
After stealing data from applications, the thief proceeds to steal files from the desktop and Documents folder of all users registered on the computer. When all the necessary data is collected, the program packs them into a ZIP archive and sends them back to the operator’s server.
Invicta Stealer stands out from other infostealers due to its ability to attack several categories of highly sensitive information at once in various applications and browsers.
Stolen data can be used by attackers both for financial gain and for launching attacks on specific individuals or entire organizations.
In order not to become another victim of scammers, you should follow the following recommendations from Cyble experts:
- set up backup
- use proven anti-virus packages;
- set up automatic software updates on all devices;
- avoid downloading pirated software from suspicious websites;
- do not open suspicious links and e-mail attachments without checking;
- use strong passwords and multi-factor authentication;
- closely monitor network activity;
- block potentially dangerous URLs;
- Train the organization’s employees on how to protect themselves from threats such as phishing.
It is necessary to clearly understand the seriousness of this threat and take the necessary measures in advance to protect against malicious actions of intruders.

