Vidar stealer is specific type of malicious software that aims at stealing certain data types. It may be distributed as a stand-alone malware, and along with different other viruses. For instance, it often arrives together with Djvu ransomware, allowing the crooks to additionally collect personal data. Let’s perform Vidar stealer analysis, and figure out how dangerous it is.
What is a Vidar Stealer?
Vidar Stealer is a malicious application that forked from its predecessor, Arkei Stealer, around 2018. The key feature of any stealer is their ability to stealthily slip into the system and grab the data of pre-defined types. That differs stealers from spyware – the latter usually takes everything it can reach, even if there is no real value in this information. Stealers became an often guest in cyberattacks, where they act as auxiliary malware, which complements the main payload.
Vidar aims at stealing banking and crypto wallets information, as well as other login credentials, IP addresses and browsing history. It can efficiently dig into Chrome, Opera, Chromium-based browsers and Firefox. That makes it pretty versatile, as even if there is no banking data or crypto wallets used in the system, it is possible to grab all other things, and vice versa. Vidar is distinctive by aiming at the FTP/WinSCP connection credentials – they’re often used by webmasters and remote workers, Additionally, it can grab different data from mailing clients, of course, if the ones are used in the attacked system. Still, such properties are not unique – different other examples of this malware type can act flexibly as well.
Vidar Malware technical analysis
After being injected and launched into the targeted system, Vidar stealer tries to connect to the channel in Mastodon social network. This network pretends to be the place for anonymous communications, and it is at least less moderated than others. The stealer tries to reach the hxxps://mas.to/@oleg98 channel to retrieve the IP address of a command and control server (C&C). Additionally, it assigns a unique ID for each infected machine and announces it to the command center.
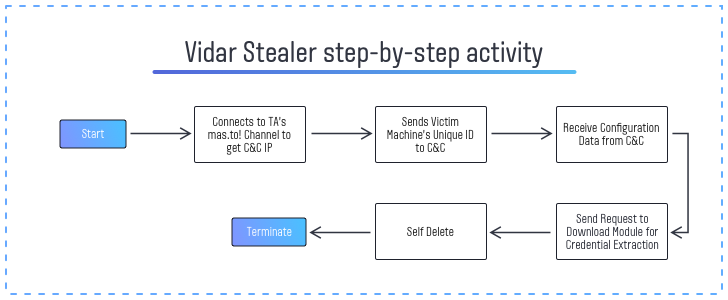
When the connection to C&C is established, malware receives the configuration data. This info serves to create the chain of processes that help the initial malware to run. Those are Devil.exe (exactly, the Vidar’s executive file), taskkill.exe and timeout.exe. It also calls for conhost.exe – the default Windows console utility. Taskkill.exe process is likely responsible for disabling the processes that can potentially disrupt the malware functionality. Timeout.exe process stops the malware execution and wipes it from the device after the time threshold. All the mechanisms and the Vidar itself are written on C++.
Vidar stealer carries most of the functions in the initial supply, however, its password stealing functionality goes as a separate module. It requests the C&C to send it once the configuration data is received and the processes are rolled out. Possibly, the purpose of such manipulation is to make malware more stealthy unless the security mechanisms are not disabled. Password stealing modules are quite easy to detect through heuristic mechanisms, thus it is better to delay its arrival. The libraries used for credentials extraction are the following:
- freebl3.dll
- mozglue.dll
- msvcp140.dll
- nss3.dll
- softokn3.dll
- cnruntime140.dll
During its activity, it creates the dumps of stolen files that are waiting for the extraction process. They are stored in temporary folders in the C:\ProgramData directory. These dumps are stored as text files or, rarely, zip archives. When the process is over, these files are compressed into a single large zipped file with a random name, and in such a form sent to a command and control server. Still, there is no encryption or password applied to control the access to that archive. Hence, once you’ve intercepted it or found an unsent one on your PC, you can check out what Vidar stealer got about your PC.
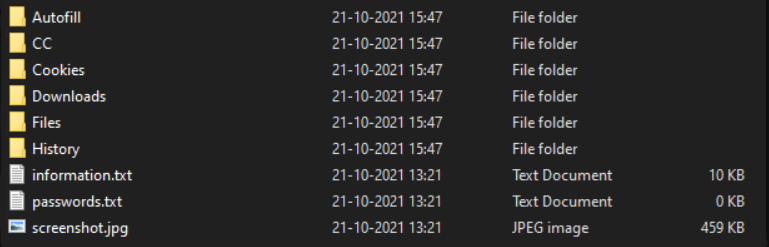
Archive of data collected by Vidar stealer
Aside from the mentioned categories of data, Vidar also collects certain system information. In particular, malware records the path where it is installed, date and time of the operation, hardware information and the list of installed software. The latter is likely needed to understand if the computer was a real one or a virtual machine used to analyse the virus. VMs always leave specific trails in the logs, and the output data from them is likely useless for crooks.
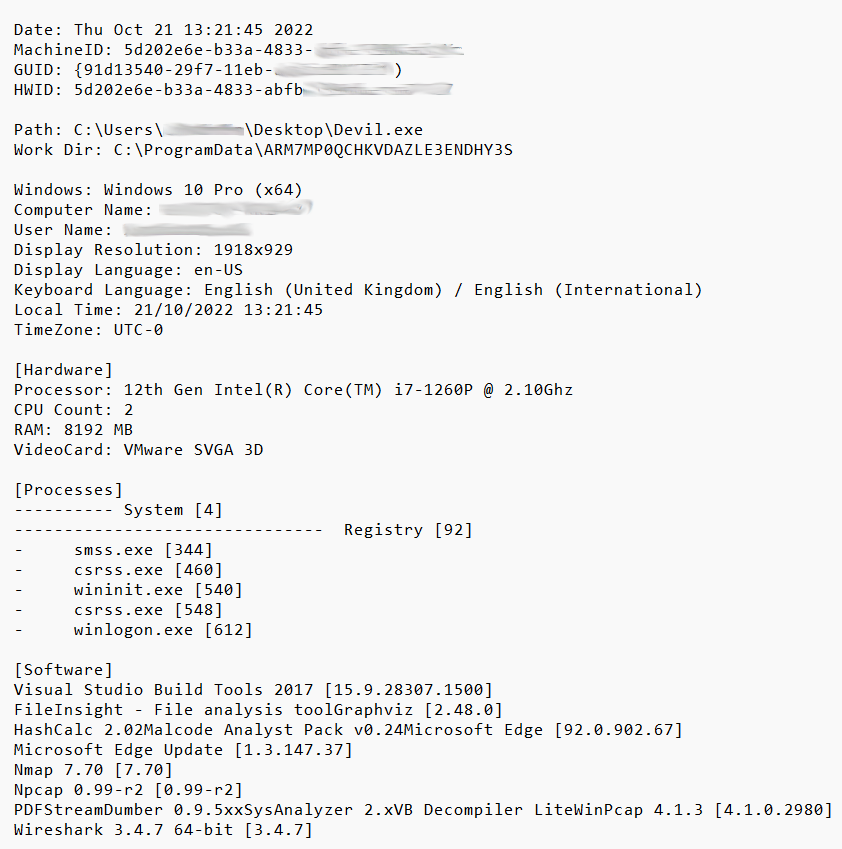
System information grabbed by Vidar
Vidar stealer IoC
| Indicator | Value | Note |
| Hash | c40c62b978908e0f5112eee4ae7370fb9c4cc1ed7c90a171be89f6fd8c10b376 | Vidar Stealer files |
| Connection | @oleg98@mas.to | Bot in Mastodon social network that sends back the C&C IP |
| C&C address | hxxp[:]//65.100.80[.]190 | IP-address received from the aforementioned bot |
Vidar variants widespread in the wild
- Trojan:Win32/Vidar.PC!MTB
- Trojan:Win32/Vidar.NX!MTB
- PWS:Win32/VidarStealer.MR!MTB
- Trojan:Win32/Vidar.AA!MTB
Vidar stealer spreading
Before getting to the ways it goes to the victims’ computers, it is worth checking the channels Vidar is sold through. Aside from the usual Darknet markets and hacker forums, Vidar developers offer their software through Telegram. This messenger became a point of interest for different crooks through the last year, as it promises more anonymity than its counterparts do. Still, no one can guarantee that you will receive anything after purchasing from this Telegram channel.
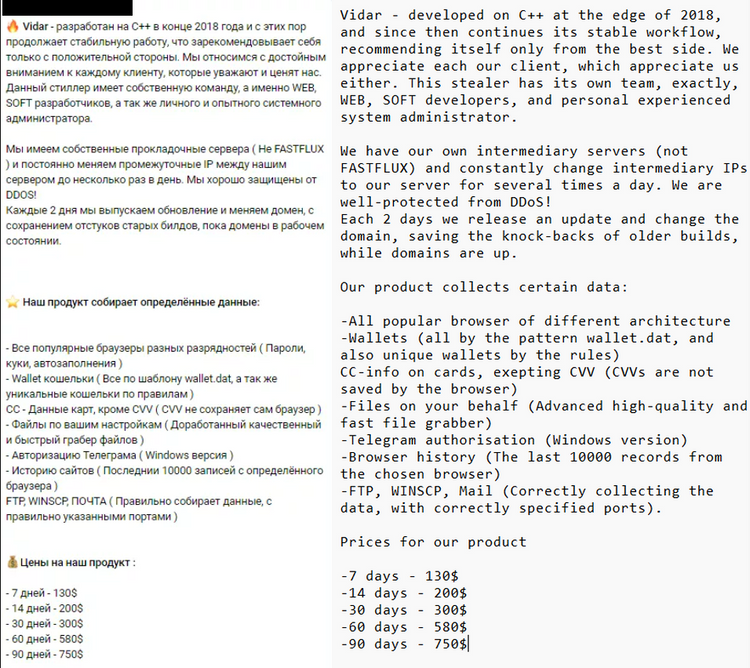
An offer to purchase Vidar stealer in the Telegram group
When Vidar is distributed as a stand-alone malware, its spreading channels are pretty similar to other stealer malware. The most common way is email spamming – messages that mimic a genuine company, but contain malicious elements. In the case of Vidar stealer, those messages have a MS Office file attached to the letter. Once the attachment is opened, the user will see the offer to enable macros execution – and this action triggers the malware delivery.
Rarely, Vidar is spread through messages on different communication platforms, like Facebook, Discord or WhatsApp. This approach requires gaining trust of the receiver, otherwise the efficiency will be same as with email spam. In combination with low volume of messages and more complicated protection against scams, that make these methods way less effective.
Aside from the stand-alone spreading of Vidar stealer, there are a lot of cases when this malware was spread as a part of a malware bundle, together with STOP/Djvu ransomware. Through the last several months, it comes together with this ransomware, and supplies the crooks with additional sources of income. As they do not apply double extortion, that data is likely for sale – there are enough buyers in the Darknet who’d be happy to buy it. In that case, Vidar stealer became a substitution for Azorult spyware – another tool used by rascals to grab some personal data. The conjunction with Djvu ransomware takes a great share in the overall number of Vidar infections.
What is STOP/Djvu ransomware?
STOP/Djvu ransomware is a product of an eponymous cybercriminal group. It is offered as ransomware-as-a-service, and attacks exclusively individuals. Appeared around 2019, it became a leader pretty soon, taking over 75% of all ransomware attacks upon individual users in 2020. Such success is a result of skilled affiliates, widely-targeted spreading campaigns, and well-done software. It is famous for having a unique repacking mechanism that changes the file sections so much that it is impossible to detect it with a signature-based mechanism. These days, it has trouble finding a new way of distributing, especially the ones that can potentially provide as high infection rates as earlier.
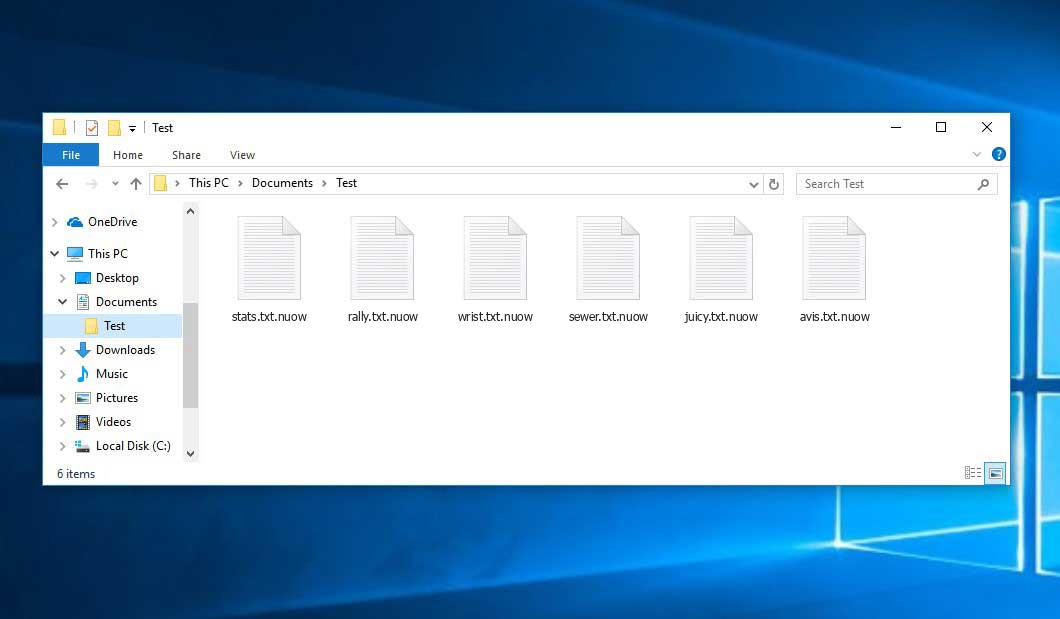
Files encrypted by Djvu ransomware (NUOW variant)
How to protect yourself from stealer malware?
Stealers, same as spyware, rely upon their stealthiness inside of the infected system. They never change much of things, and rarely disrupt your system workflow when acting solitary. Hence, it is better to give it minimal chances of getting in. Let’s concentrate on this and see what will help you to avoid this malware.
Never trust email attachments. As I’ve described above, the vast majority of Vidar stealer injections as sole malware are related to email spam. Interacting with its content, whether it is a link to a third-party website or an attached file, is a bad idea. Fortunately, they are quite easy to detect – by the sender’s address and strange text with unexpected contents. Checking up on these two signs will help you to weed out the vast majority of scam emails.
The typical example of a bait email. The attached file contains malware
Avoid pirated content. This is more related to Djvu ransomware, which is often accompanied by Vidar stealer. Most of the sites that offer you pirated games or films will assure you that they are malware-free. Only rare cases are clean though, although not all of them contain ransomware. Still, there is nothing pleasant about getting malware on your computer, as well as facing lawsuits for breaking the copyright law.
Use decent anti-malware software. As a last resort, you should have a well-done security solution that will effectively catch and delete any malware on your computer. GridinSoft Anti-Malware will fit best for this purpose, as it features a perfect detection mechanism that consists of 3 elements. Additionally, it is very lightweight – you will not feel any load on your system when it runs in the background. Within a 6-day free trial, you will be able to test all of the features it offers.
User Review
( votes) ![]() German
German ![]() Japanese
Japanese ![]() Spanish
Spanish ![]() Portuguese (Brazil)
Portuguese (Brazil) ![]() French
French ![]() Turkish
Turkish ![]() Chinese (Traditional)
Chinese (Traditional) ![]() Korean
Korean ![]() Indonesian
Indonesian ![]() Hindi
Hindi ![]() Italian
Italian

