“Darknet”, “Dark Web”, “Onion”, “Tor” – you may hear these words in different parts of the Internet. Because the background talks where these words are usually related to something outlaw, people often think that the only contents of the Darknet are drugs, slaves, illegal weapons and stolen banking cards. Let me bust this myth and show you the real essence of the Darknet.
What is Darknet?
Darknet is a part of the global Internet, which has its own internal organization and specific structure. Search engines cannot index any information from there. Users cannot reach anything from Darknet without the use of specific software. Such peculiarity is conditioned by the basic rule of this network – full anonymity. Of course, you still can do something wrong and get your personal information exposed. But still – there is no way to reach it through the regular browsers.
Darknet is generally used by people who need 100% anonymity. Besides the most known demanders – various cybercriminals – there are also a lot of people who do not want to reveal their location, real name, email and other stuff. Opposition journalists, people persecuted by the government or bandits – they are paranoiacs in their privacy. Because influential groups can easily establish the reconnaissance on aforementioned groups, last ones will do everything to avoid detection. Some people make use of the Darknet just because they don’t want to allow the corporations to collect information about them.
| Surface web | Sites that can be reached through Google search or by typing its URL in the search bar |
| Deep web | Corporations’ networks, non-indexed files, pages that you can access only after logging in. Search engines cannot show it to you immediately, but you still can access them in a certain way. |
| Darknet | Part of the Internet which is inaccessible without the specific software. The network is much more decentralized than the other webs. There is no regulating authorities there – just local ones, like moderators on forums. |
Short historical reference
Its development started shortly after the ARPANET – the predecessor of the modern Internet. Being demanded by the military, Darknet was originally the network of computers which were able to receive messages, but couldn’t respond to them. By the original plan, you were not even able to ping those devices. Such functionality was extremely demanded for transferring the top secret materials. The spies could not access it, since they cannot even find the computer in that network. Later, the global model of this network was used for establishing the peer-to-peer networks.
How to access darknet?
It may look like a joke, but to access the network which is inaccessible from web browsers, you need… a web browser. Of course, a special one – Tor. A browser with an onion on its logo, it is used by the vast majority of people to access Darknet. It has special configurations which allow it to prevent any kind of telemetrics, and provide anonymity on the highest level. Besides giving your access to the Darknet pages, it also allows you to open regular sites. But it is a bad idea to use it on a continual basis as your main web browser.
Tor interface
There is also an alternative way to access the Darknet – Tor2web plugin for Chrome. However, I will not recommend you to use it. Yes, it can open some of the Darknet pages, but it does not provide you even a bit of anonymity that is provided by Tor. Hence, if you need to be unrevealed, you must avoid such crescents.
Is Darknet legal?
Sure. It is as legal as the so-called surface web. The only thing which goes out of law is strong encryption used in Tor browser – it is forbidden for the Internet connections in certain countries. Such a step is likely done to allow the law enforcements to control the users’ activities. However, even seeing a heavily-encrypted traffic, they can do nothing – your personal data remains secret. The only way to punish the Tor users is to catch them red-handed.
Pay attention to this guide: How to Resolve the Most Annoying Issues in Windows 10
Some people say that the Darknet must be strictly prohibited, because a huge amount of criminals conduct their activity there. Yes, almost all modern criminals use Tor for communication or dealing. However, not each user in the Darknet is a burglar – exactly, that’s why it is allowed. Having the remedy for untrackable connections is vital for different categories of people.
Safety measures to access Darknet
Darknet is a zero-control zone. You could think that the cybercriminals will set their nets in the places where they cooperate, and you are right. Since Tor does not take care of what happens in that network, you may easily be tricked. Phishing pages, exploit landings, direct links to malware downloading – all of these things are everywhere in Darknet. Hence, you must always be aware and follow the basic cybersecurity rules. Moreover, it is better to have several advanced tricks.
The example of a phishing page
Have the basic knowledge of what you are going to do
If you are looking for something on the Darknet – for example, for the fresh news on different forums – don’t stick your nose out of your way. Clicking the link on the Darknet forum may easily lead to malware downloading, or to the phishing page. And because of the specific addresses used in the Darknet, you will not be able to distinguish it from the original site. No one will give you mercy because you are a newbie here. Sure, moderators usually delete the messages with malicious links inside. But who knows how much time will pass, and how much “fish” will be lured until the link is removed?
Of course, you can meet the situation when the information you need is published by the link. In that case, check the messages below – possibly, someone has already opened the link and see if it contains something malicious (or legit). If no messages are published then – just wait. Haste will not kill you, but can cause you a lot of problems, especially if you use Tor for privacy reasons.
Check your security mechanisms
A good antivirus is essential nowadays. It is demanded even more if you use Darknet – because of the reasons described just above. When you make a mistake, and malware installs on your PC, the anti-malware software is your last option. Well-designed program with a proactive protection mechanism onboard can stop malware before it starts acting. GridinSoft Anti-Malware shows great results in stopping the malware on run.

Beware of hazards
They were touched two paragraphs ago. Phishing, malware distribution through dubious links, injection via social engineering, links to the exploit servers – all these stuff is present in the Darknet. Of course, there is no problem for the experienced user, who knows what to expect. But not each user who enters the Darknet knows how to understand if the link is legit, or if someone tries to scam him.
First rule to remember is don’t trust anyone. This network is anonymous not just only to prevent tracking. People there seek ways of making profit on trusty people, and they are ready to do anything to make money. They don’t even need to search the specific software – they have it just under their right hand. Tor is able to protect you from location tracking, telemetrics or “traffic reading”, but it can’t disable your keyboard when you type your credentials on the scam website.
Safety for paranoiacs
The security measures in Tor do not satisfy you? Ok, there are a ton of different ways to enhance your security even more. But again – it will not protect you from your own naivety. You don’t need to set up any other programs – the general functionality is available exactly in the browser, or as plugins.
Adjust the safety settings
Check the Safety settings of your Tor (shield-shaped icon at the top right corner). Set up this setting to the “Safest” option. This option disables the JavaScript execution on all pages, and also changes the encryption algorithm to a tougher one. That results in much slower page loading, problems with displaying the embedded contents, inability to play the embedded videos – but you may be sure that no one can see your personal information.
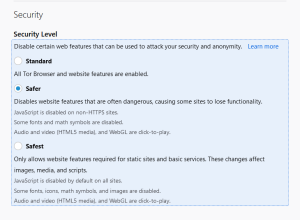
Disable the scripts manually
If you don’t want to have your Tor slow as a snail, but still worry about the scripts, your choice is to disable JS manually. For this, you need to dig a bit into the browser configurations. Type “about:config” in your address bar and agree with all cautions. Then, in the search bar on the appeared page, type “xpinstall.signatures.required”. Double-click the bar to set this function to “disable”.
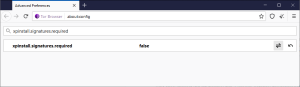
Now, you have the script loading disabled for all pages.
Myths about the Darknet
Only illegal things can be done through the Darknet
If chatting on forums and in messengers is illegal in your country – sure, there is nothing legal there. But such a situation is surrealistic. Only the most totalitarian country in the world – North Korea – does not allow it. But they don’t have Internet access either. The facilities offered by Darknet in general and Tor in particular are pretty suitable for people who conduct outlaw activities. But that does not mean that each user you see in the Darknet is a criminal.
Only criminals use Darknet
Darknet messengers are widely used by people who are persecuted by criminals, government or other influential groups. When it comes to hiding your location, IP-address or reserve emails, Darknet is likely the best. Cybersecurity journalists use Darknet to have a look at hacker forums located there. On such pages, they look for interesting facts and the latest news from cybercriminals. This way, they receive the information from the original source and likely one of the first.
Darknet is much bigger than a Surface web
Lies that are not even based on partial information, like two previous myths. Reportedly Darknet currently consists of ~450-500k pages. Meanwhile, the Surface web has more than 5 billion pages – and even more if we remember about the Deep web.
Some tips for Darknet browsing
Search engines
The most used search engine in Darknet is DuckDuckGo. It is almost the only search engine that can work correctly in Darknet. Its developers assure that they don’t collect any information about your queries, which is likely essential in Darknet. In addition, it can also index the true darknet pages – with the URL ending on .onion.

Luckily, DuckDuckGo is a default search engine in Tor. It is not recommended to change it, since it may affect your privacy and search efficiency.
Anonymous file uploading and sharing
Regular file sharing services, like Dropbox or FEX, do not provide high security. With the use of special software, you can easily get the IP-address of the user who shared the file, or even his email. OnionShare1 – an open-source file sharing program – offers the same functionality, but with the guarantee of your privacy. Open-source form of distribution allows you to ensure that the program does not have any leak hazards.
VoIP calling
VoIP calls are especially dangerous while conducted through the browser apps. WebRTC protocol, which is widely used for providing online calls, has several design flaws that allow you to get the information about your collocutor. Refusing to use the browser VoIP programs is rarely a choice, so the only way is to find a workable solution.
Consider reading: How to check your disk for issues?
I can offer you to use the Linphone2 app. It is absolutely free and open-source, and can boast of absence of any logs and usage of end-to-end encryption. In my opinion, when it comes to privacy, open-source software is much better than “classic”, with a closed codebase. If you are experienced enough, you may easily check the source code for possible flaws or exploits.
Anonymous messengers
Same as VoIP calls, messengers also use vulnerable protocols for transferring the messages. It is OK when you are not so paranoid about your privacy, but not when you use Darknet to avoid any kind of surveillance. Classic Viber or WhatsApp are widely known as a source of data for governmental agencies. And even if you are not a cybercriminal, the law enforcement of your country may be interested in the information about you just because of your activity.
Signal3 is considered as one of the most private messengers. The only source of information that can be exposed to the government is one which is kept on the messenger’s server. Signal keeps literally nothing – and proves it in the latest incident with the FBI. The Federal Bureau of Investigations asked Signal to give them the data about two users, but the only thing about them found on the servers was the time of the last visit and account registration date – both in Unix time.
Darknet Wiki
Darknet is pretty hard to explore if you don’t know where to get the information you need. A wikipedia-shaped site, called the HiddenWiki, can help you in finding useful information and websites. It has the following address in the Darknet:
http://zqktlwiuavvvqqt4ybvgvi7tyo4hjl5xgfuvpdf6otjiycgwqbym2qad.onion/wiki/index.php/Main_Page
The Darknet Wiki is organized just like any other wiki-like website. Search bar, list of the most popular articles, editors’ choices – it is present on the main screen. For more information, just search for the topic you need.
User Review
( votes)References
- Privacy + Productivity: https://onionshare.org/
- Linphone: https://www.linphone.org/
- Signal: https://signal.org/#signal

