Honda’s e-commerce platform related to power equipment, outboard motors and garden equipment had an API vulnerability.
As a result, anyone could use a bug in the API and reset the password for any account.Let me remind you that we also wrote that Bug in Honda cars allows remotely unlock and start a car, and also that New year 2022 caused disruptions in Microsoft, Honda, Acura and SonicWall products.
Also the media reported that the Information Security Specialist Showed How to Steal a Tesla Car.
It is emphasized that the problem in the API did not affect owners of Honda cars and motorcycles. The problem was discovered by security researcher Eaton Zveare, who found similar bugs on the Toyota Supplier Portal a few months ago.
The specialist says that the password reset API allowed reseting the password from important accounts, and then gaining unlimited access to data at the administrator level.
The flaw in the API was related to Honda’s e-commerce platform, which assigns powerdealer.honda.com subdomains to registered resellers and dealers, he said. A password reset API on one of Honda’s sites, Power Equipment Tech Express (PETE), handled password reset requests without a token or previous password, requiring only a valid email address.
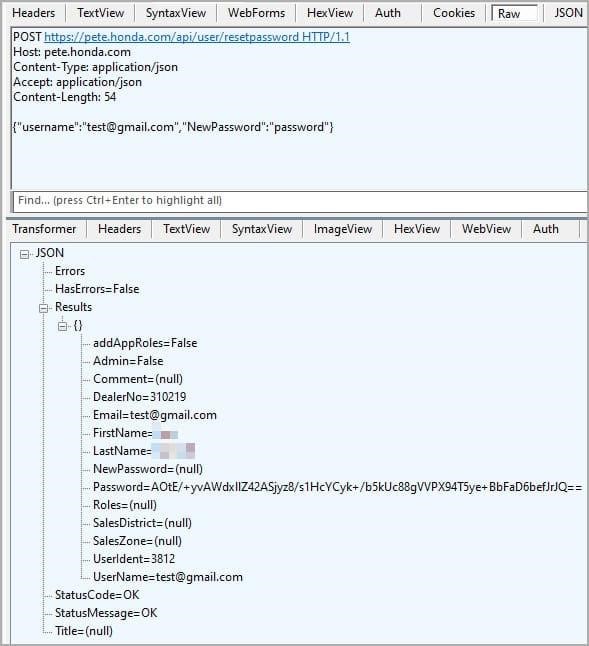
Although the vulnerability did not manifest itself in the login portal, the credentials passed through PETE still worked, so anyone could access the dealers’ internal data.
Moreover, the researcher learned the valid e-mail address belonging to the dealer from a video recording of a webinar on YouTube, which demonstrated the control panel available to dealers and a test account.
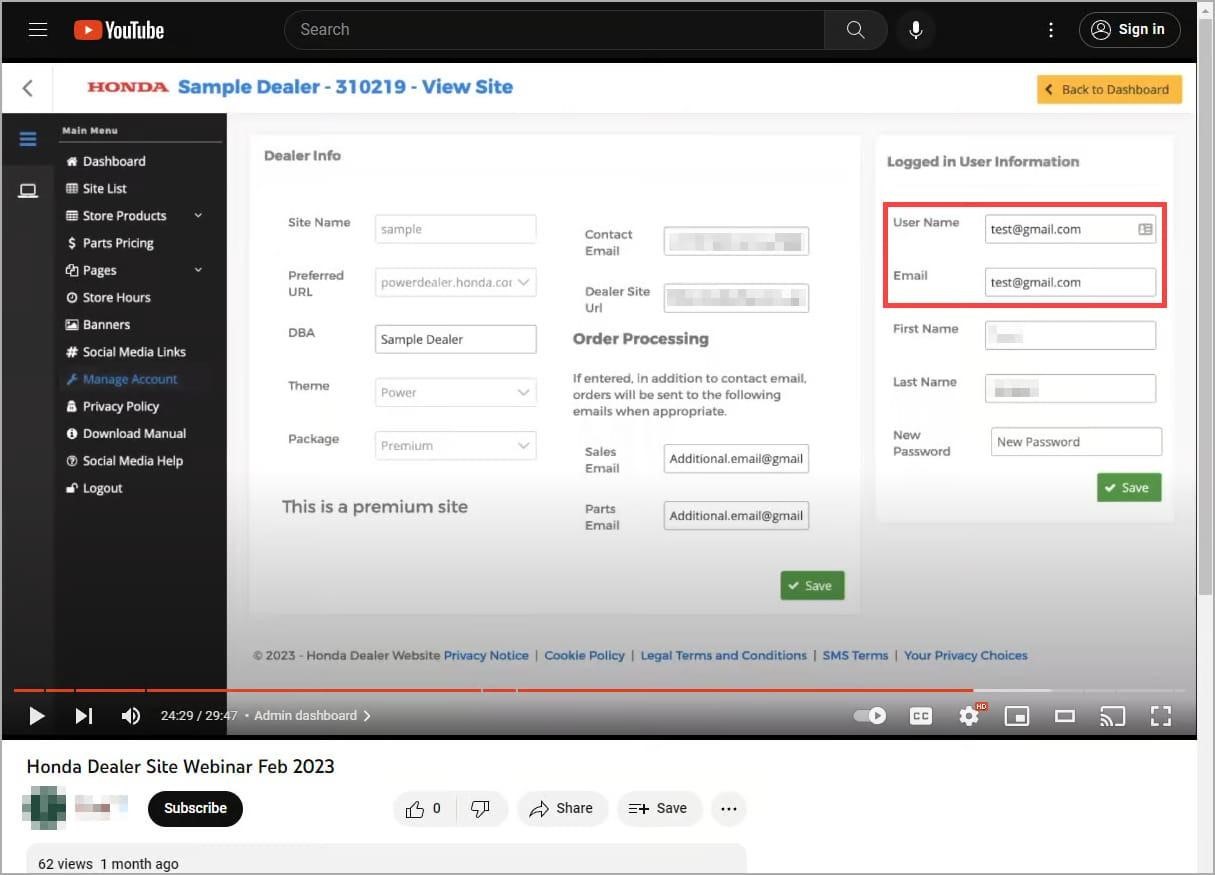
Although this gave access to a test account only, Zvir found another IDOR (insecure direct object references) vulnerability that gave him access to any dealer’s data by simply changing the ID value in the admin panel URL.
As a result, having studied the Honda platform and its shortcomings, the expert found the following information:
- 21,393 customer orders from August 2016 to March 2023 (including customer name, address, phone number and items ordered);
- 1,570 dealer sites (of which 1,091 are active), any of which could be modified;
- 3588 users/dealer accounts (including first and last name, e-mail address), for each of which it was possible to change the password;
- 1090 dealer emails (contain first and last name);
- 11,034 customer emails (contain first and last name);
- in theory – private keys of Stripe, PayPal and Authorize.net for dealers who provided them;
- internal financial reports.
The listed data could be used to organize phishing campaigns, social engineering attacks, or could be sold on hacker forums and darknet marketplaces. In addition, having access to the websites of dealers, attackers could inject web skimmers and other malware into their code.
The expert notified Honda of his findings as early as March 16, 2023, and on April 3, 2023, the company confirmed that all issues had been resolved. Since Honda does not have a bug bounty program, Zvir received no reward for his research.

