The PyPI administration has warned that hackers are attacking developers as part of a phishing campaign aimed at maintainers of packages published in the repository. The attackers have already compromised hundreds of maintainer accounts and infected numerous packages with malware, including the popular exotel and spam.
Let me remind you that we also talked about Malicious Packages from PyPi Arrange DDoS Attacks on Counter-Strike Servers, and also that 10 Malicious PyPI Packages Steal Credentials.PyPI reported that a real “hunt” was announced for developers, after even Django board member Adam Johnson reported receiving a suspicious letter. The email he received urged developers whose packages were published on PyPI to go through a mandatory review process, saying that they risked having the packages removed from PyPI if they didn’t.
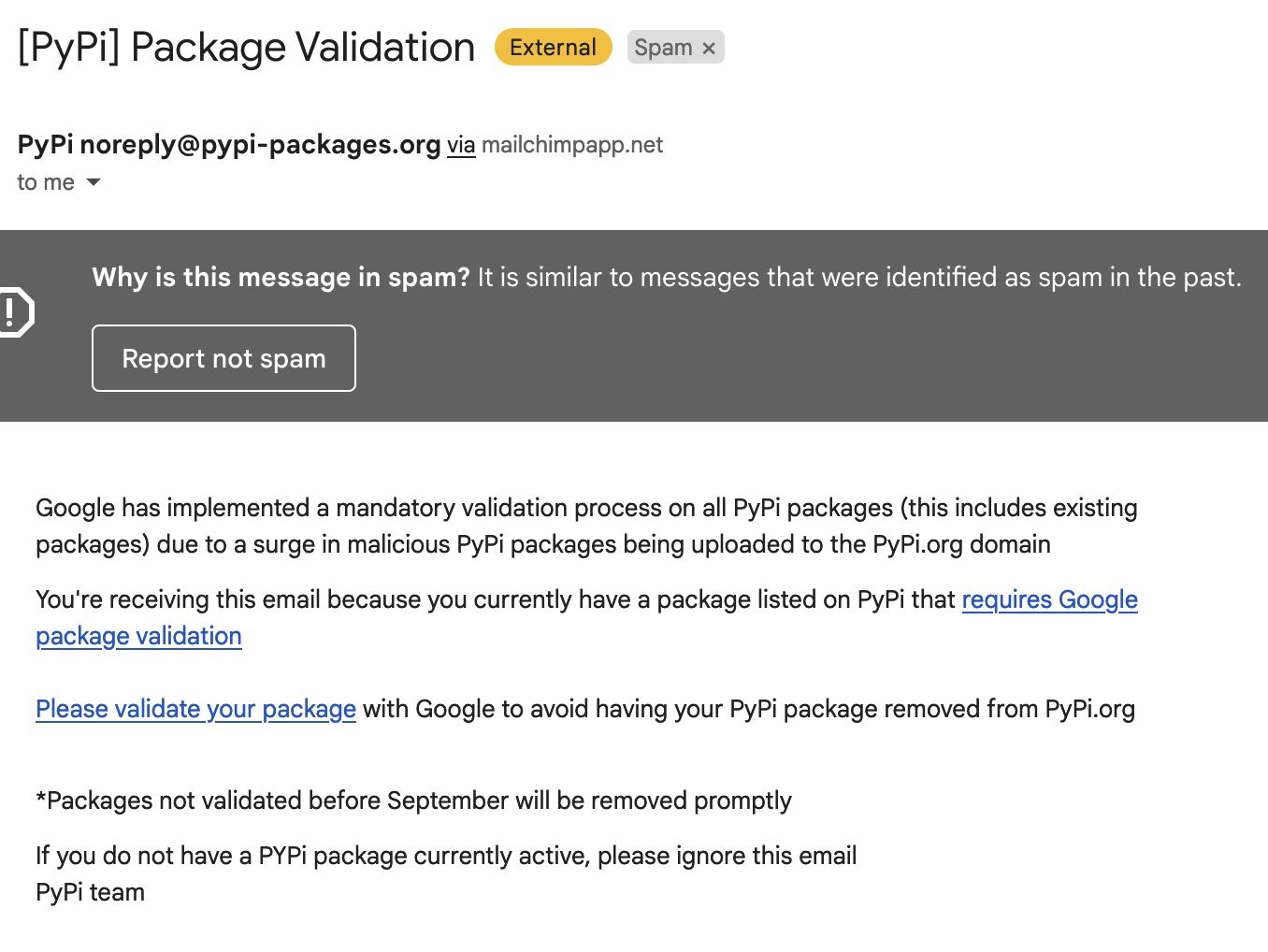

Adam Johnson
Johnson said that the phishing site he clicked on from the email looked pretty convincing, but it was hosted on Google Sites, which resulted in an Info button in the bottom left corner.
Unfortunately, not everyone was as attentive as Johnson. Some developers fell for the phishers’ bait and entered their credentials on a hacker site, which led to their accounts being taken over and packages infected with malware. PyPI reported that the infected packages included spam (versions 2.0.2 and 4.0.2) and exotel (version 0.1.6). Currently, the malware has already been removed from the repository.
According to the PyPI administration, after reports of attacks, a check was carried out, as a result of which “several hundred typesquats” that matched one pattern were identified and removed.
Malicious code embedded in compromised packages has been known to pass the user’s computer name to the linkedopports[.]com domain and then download and run a Trojan that makes requests to the same domain.
In light of this phishing attack, developers were once again reminded of the importance of two-factor authentication, which has recently become mandatory for maintainers of mission-critical projects. Also, PyPI administrators shared a number of tips to protect against such phishing, including recommending to carefully check page URLs before providing credentials from your account.

