The scammers are trying to capitalize on a massive ransomware attack and are distributing fake patches for the Kaseya VSA.
Attackers are sending spam disguised as updates for Kaseya, but in reality they are Cobalt Strike payloads.Cobalt Strike is a legitimate commercial tool created for pentesters and red teams and is focused on exploitation and post-exploitation. It has long been loved by hackers, from government APT groups to ransomware operators.
Although it is not available to ordinary users and the full version is priced at about $3,500 per install, attackers still find ways to use it (for example, relying on old, pirated, jailbroken and unregistered versions).
For example, we talked about the fact that ransomware operators also use Cobalt Strike in about 66% of cases.
Typically, the ultimate goal of such attacks is the collection and theft of confidential data, as well as the delivery of second-level malware.
The malicious spam associated with the recent attack on Kaseya was spotted by analysts at Malwarebytes. They warn that such messages contain a link that looks like a Microsoft patch to fix a vulnerability in the Kaseya VSA.
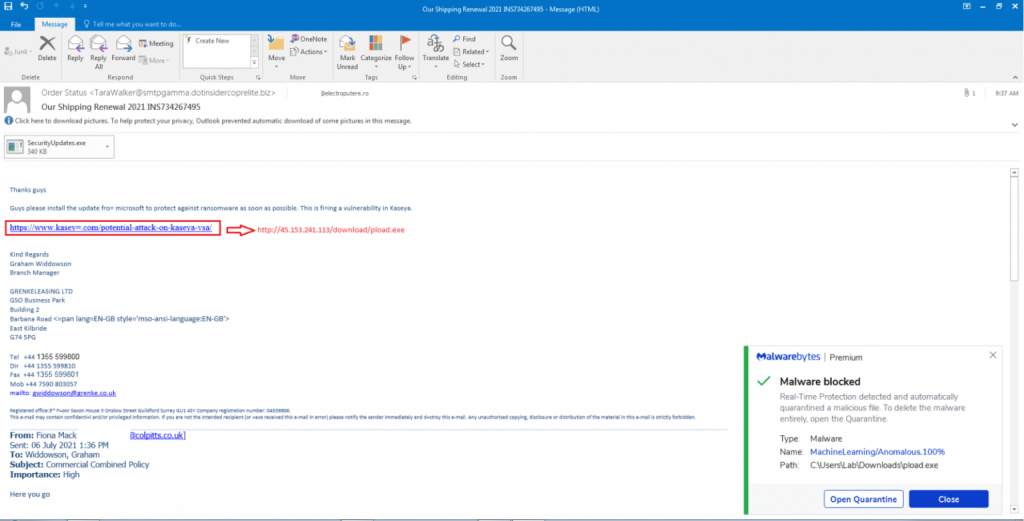
If a user falls for a scammer and installs an “update”, after launching a malicious attachment or downloading and running a fake patch, the attackers gain permanent remote access to the victim’s systems.
Let me remind you that about 1,500 businesses really suffered from the REvil ransomware attack, and hackers exploited the CVE-2021-30116 vulnerability for this.
However, there is no patch for this problem yet, and the Kaseya developers are asking all customers to temporarily keep VSA off.

