Late on the last Friday evening, on the eve of July 4th, the REvil (Sodinokibi) ransomware attacked and gained access to the infrastructure of the MSP provider Kaseya, and implemented a malicious update into the VSA program, as a result of which many Kaseya customers were affected.
It looks like this incident could be the largest ransomware attack in history. The fact is that unlike the attacks of WannaCry, NotPetya and Bad Rabbit, which were more widespread, those incidents were associated with “government” hackers, and not with financially oriented groups, such as REvil.The incident was first reported through the Reddit section on Managed services providers (MSPs). These companies provide remote IT services to small businesses that do not have their own IT departments, and these companies make up Kaseya’s customer base.
Soon, Sophos experts reported that the attack was widespread, as the attackers introduced a malicious update to VSA, one of Kaseya’s products. As a result, the REvil ransomware was deployed to client systems, and the affected companies received ransom notes in the amount of $50,000 (if the infected machines were not joined to the domain) or $5,000,000 (if the computer was in a large corporate network).
Kaseya representatives promptly asked their customers to turn off VSA as soon as possible until further notice, and also shut down their own cloud infrastructure in an attempt to drive hackers out of their systems. Now the company claims that it has already found a vulnerability used by hackers and is working to eliminate it.
The company is also known to have hired FireEye experts and a number of other cybercriminals to assist in the investigation of the incident and released the Compromise Detection Tool to its customers to help them determine if they were affected by the attack.
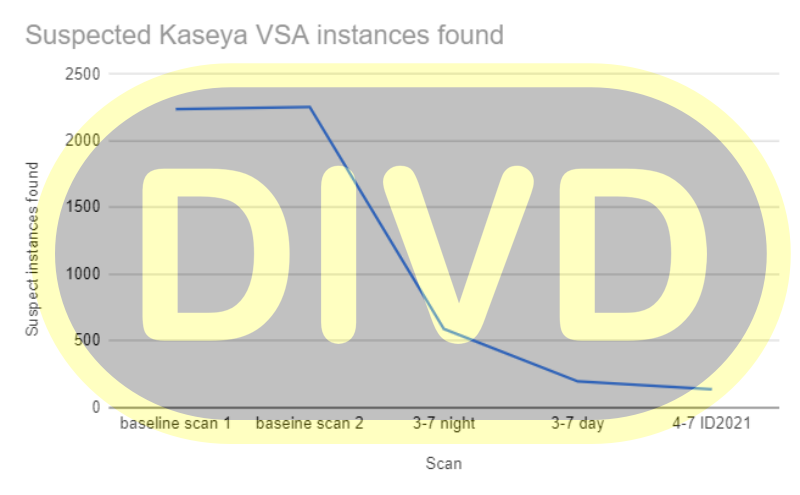
Interestingly, according to the Dutch Vulnerability Disclosure Institute (DIVD), the attackers exploited a vulnerability in the Kaseya VSA servers, which one of the researchers had discovered a few weeks earlier.
Gevers claims that Kaseya engineers were already working on fixing the problem when the attack took place, but does not provide any details about the bug itself or how the attackers might have found out about the problem at all.
In turn, the information security company Huntress Labs, which was one of the first to record the attacks, claims that all signs indicate that the vulnerability is associated with bypassing authentication in the VSA web interface. It looks like the bug was being used to bypass authentication and then to run SQL commands and deploy the ransomware to all connected clients. On client networks, a “VSA agent hotfix” was deployed through VSA, which bypassed anti-virus products using old and vulnerable versions of Microsoft Defender, and then encrypted the victims’ machines.
Huntress Labs also writes that the incident affected at least 20 MSP providers.
DIVD says it has scanned the Internet for VSA servers, and there are currently less than 140 of the 2,200 active servers online before the attacks. Apparently, the consequences of the attack could have been much worse if Kaseya employees had not rushed to shut down their infrastructure and urged VSA owners to shut down their servers.
Although Kaseya’s products are used by tens of thousands of customers, shortly after the attack, CEO Fred Voccola rushed to assure the media that fewer than 40 of them were affected by the attack.
However, the problem is that most of the VSA servers were used by MSP providers, that is, companies that manage the infrastructure of other clients. This means that the attackers deployed the ransomware in thousands of corporate networks, even if only 40 VSA servers were affected by the compromise of Kaseya.
So, among the MSP-providers who have already admitted that they suffered in the course of this incident are Visma EssCom, Synnex and Avtex.
It is also known that Coop, one of Sweden’s largest supermarket chains, has closed nearly 800 stores across the country after being hit by a REvil ransomware attack. Although Coop blamed one of its suppliers for the incident, the incident happened at the same time that hackers infiltrated Kaseya’s network. That is, the mentioned supplier was obviously a client of the company.

ESET analysts report that they are fixing a spike in REvil infections, which they associate with compromises with Kaseya. According to the company’s telemetry, the majority of infected systems are located in the UK, South Africa, Germany and the United States.
Kaseya says it intends to alternately bring SaaS data centers online, starting with the EU, UK and Asia-Pacific, followed by data centers in North America.
At the moment, the full scale of the incident is still unclear, but the incident caused a violent reaction from law enforcement agencies. US President Joe Biden has already drawn attention to the incident and ordered the special services to investigate the hacking that affected hundreds of American enterprises. FBI officials said they are working on an investigation with the Department of Homeland Security (DHS CISA) Cybersecurity and Infrastructure Protection Agency.
REvil operators, in turn, are demanding a ransom in the amount of 70 million US dollars, and then they promise to publish a universal decryptor that can unlock all computers damaged after the Kaseya hack.
Let me remind you that we wrote that FBI says ransomware REvil was behind attack on JBS.

