Experts from the Fox-IT NCC Group warn that thousands of installations of Citrix Application Delivery Controller (NetScaler ADC) and Citrix Gateway (NetScaler Gateway) servers are still vulnerable due to two serious bugs that developers have fixed in recent months.
You might also be interested in reading: Criterias that ransomware gangs use to choose their target, as well as US Authorities List Vulnerabilities That Chinese Hackers Attack.The first vulnerability, CVE-2022-27510, was patched on November 8, 2022. This bug is an authentication bypass affecting both of the above Citrix products. Attackers can use it to gain unauthorized access to a device, completely take over a remote desktop, or bypass protection against bruforce attacks.
The second vulnerability, CVE-2022-27518 (CVSS 9.8), was patched on December 13, 2022. It allows unauthenticated attackers to remotely execute commands on vulnerable devices and gain full control over them. At the same time, Citrix developers and NSA specialists have already warned that hackers are actively using the problem, including those from the Chinese “government” group APT5.
The media also wrote that the FBI and NSA discovered Drovorub malware, created by Russian Intelligence services.
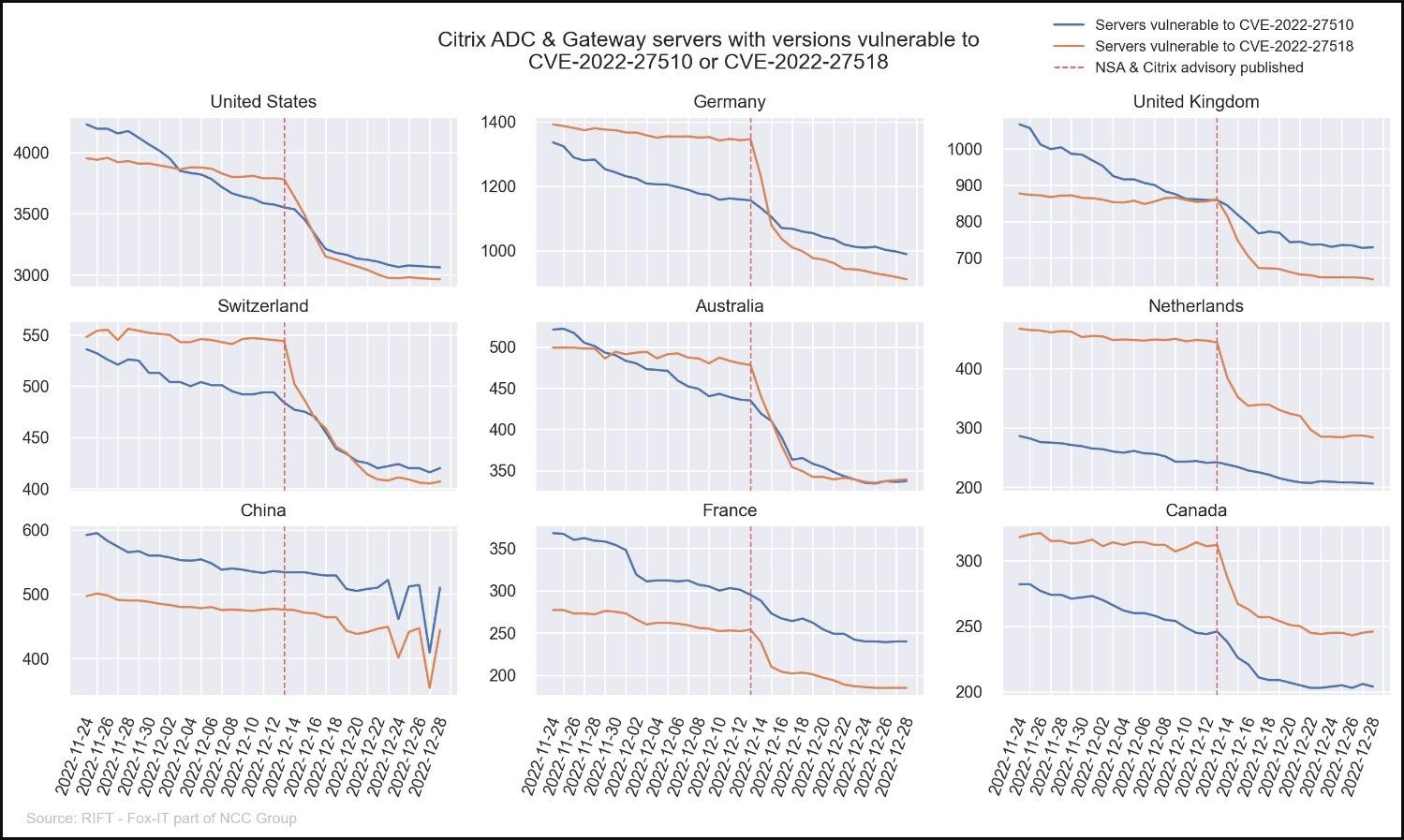
Fox-IT NCC Group analysts scanned the web for Citrix servers and concluded that as of December 28, 2022, thousands of them still have not received patches, making them an attractive target for hacker groups.
As you can see in the illustration below, most machines are running version 13.0-88.14, which is not affected by the above vulnerabilities. However, the second most popular version is 12.1-65.21, which is vulnerable to CVE-2022-27518. It is used by 3500 endpoints. In addition, more than 500 servers with versions 12.1-63.22 were found to be vulnerable to both of these vulnerabilities.
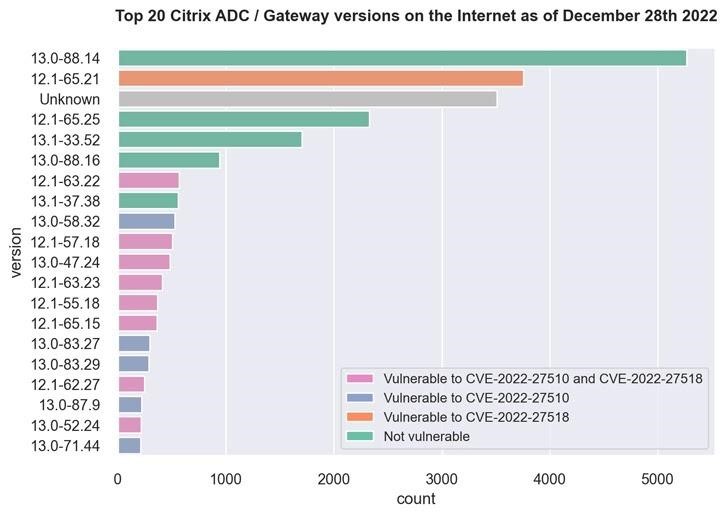
Fortunately, analysts note that a number of conditions must be met in order for CVE-2022-27518 to operate. So, servers should use SAML SP or IdP. And this means that not all of the 3500 detected systems will be vulnerable to attacks by intruders.
The researchers say that more than 40% of servers located in Denmark, the Netherlands, Austria, Germany, France, Singapore, Australia, the UK and the US have been upgraded. The worst situation with patches is in China, where only 20% of almost 550 servers received patches.