Ransomware is an extremely dangerous type of malware, which can break through your security mechanisms and cipher your files. It is hard to be sure that your company is safe, until the action happens. But ransomware developers make a huge mistake by publishing the blacklist of their targets – companies that are forbidden to attack, based on the principles of their “code of honor”.
Do ransomware groups have honor?
It sounds comical, but those fraudsters have it. At least the majority of crooks agreed to avoid attacking the companies which belong to the group of vital organizations. However, the other side of this coin is that they secure themselves from being seriously wanted by security organizations, such as the FBI, for example. In fact, the Federal Bureau of Investigations or others have a dossier for each ransomware group which is in their range. But the extremal attention is paid only to ones that did a cybercrime which have seriously affected national security.
Such a case took place in May 2021, when a DarkSide ransomware group attacked Colonial Pipeline company. Last one is the largest supplier of refined oil products on the east coast of the U.S. The shutdown of its operations caused significant fuel shortages in the East Coast states – almost 20% of fueling stations were out of fuel and so shut down. This occasion caused not only discomfort because of inability to refuel your car, but also because of the gasoline price surge. So wide effects could not be ignored by the executive authorities, so they have started a very active campaign against the DarkSide group.
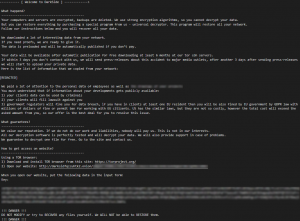
Ransom note for Colonial Pipeline
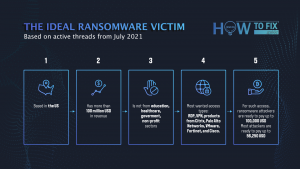
Exactly, that case pushed the ransomware1 groups to create a “common-for-all” list of companies that must not be attacked. The sectors that are safe from ransomware are the healthcare industry (47%), educational and governmental institutions (37%). Much less “safety” is provided for non-profit organizations: only 26% of gangs claimed that they will not attack such targets. Some of the gangs also claimed that they will avoid attacking the important infrastructural companies, like the aforementioned Colonial Pipeline.
Hitting the bullseye: how ransomware gangs choose their targets?
The majority of modern ransomware gangs aim at corporations. This fact is confirmed by two statistical facts: the overall amount of ransoms paid by corporations compared to ones paid by individuals, and the amount of new ransomware groups that aim at companies and individuals. In fact, we can see that there is a single serious ransomware gang that aims at individuals – STOP/Djvu family2. Cybersecurity reports say about more than 70% of attacks on individuals conducted by that group. Meanwhile, there is a huge amount of cybercriminals who aim at corporations, and each week their amount gets bigger.
Money turnover of corporations-oriented gangs is also hard to challenge. A single ransom paid by a company can easily beat the ransoms from 1000 individual victims. Some ransoms from corporations can overbeat the monthly amount of ransoms paid to STOP/Djvu family: in March 2021, Acer paid $50 millions – currently, the highest ransom that was ever paid.
English! Do you speak it?
Analyzing the posts on the Darknet forums, the researchers saw an interesting tendention. Cybercriminals generally aim at companies from Canada (37%), Europe (31%), USA (47%) and Australia. That likely happens because of the fact that companies in those countries are more successful: the better the company goes – the more the chance that the ransom will be paid.
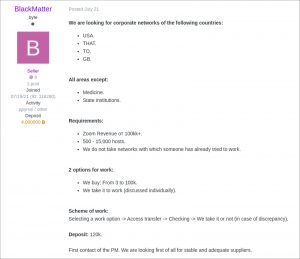
Post from BlackMatter ransomware gang, who looks for the offer of access to the corporate network.
Some doubts appear when the fact that they almost always ban the countries of the Commonwealth of Independent States (CIS) – a lot of factors point at the fact that most of ransomware is originated there. But the fact that the company has its headquarters in one of the mentioned countries is not the only condition to be matched.
Dangerous technologies
A lot of ransomware groups who were looking for access to corporate networks wanted to get the network with VPN or RDP usage. Both of these technologies are vulnerable to malware penetration if set up wrong. Besides those networking technologies, hackers are also glad to see the products of Palo Alto Networks, Cisco, VMware, Citrix and other application software producers. Such demand is likely caused by the large number of available vulnerabilities in the products of these companies. Crooks will try to use all their exploits arsenal to get access to your network.
Common pricing for accessing the network with such characteristics is about $56,000, but sometimes ransomware gangs can increase the bid up to $100,000. The peculiar thing hides in the fact that almost 45% of groups that are bidding so high for that access were created after July 2021. Where do they get so much money? This question provokes a lot of discussions and versions, but the correct answer is still absent. And does it exist at all?
Special conditions
Some groups have an increased accent on attacking the sectors or countries which have political or military unrest. For example, during the political changes in Afghanistan, the last one became a leading country in new ransomware attack cases. During the period of August 5 – September 4, 2021, cybersecurity organizations reported that 1.7% of all cyber attacks were aimed at Afghanistan. That share outpaces South Korea, Pakistan, Papua New Guinea and many other companies. Those numbers became even more contrasting after checking the previous stats for this country: it had a share of less than 0.1%.
Consider reading: Obsolete ransomware is a threat.
User Review
( votes)References
- Ransomware: https://gridinsoft.com/ransomware
- STOP/Djvu ransomware: https://gridinsoft.com/ransomware/djvu