Researchers have discovered a number of serious problems in the software implementation of the Border Gateway Protocol (BGP) that can be used to induce a denial of service (DoS) on vulnerable BGP peers.
Let me remind you that we also wrote that Vulnerabilities in MiCODUS GPS Trackers Allow Remote Car Hacking, and also that GPS devices may behave unpredictably in the coming days due to a bug in the GPS Daemon.Vulnerabilities were found in FRRouting version 8.4, a popular open source Internet routing protocol suite for Linux and Unix platforms. It is currently used by many vendors, including NVIDIA Cumulus, DENT and SONiC, posing risks to the supply chain.
You might also be interested to know that NVIDIA fixed two serious bugs in GeForce Experience.
The issues were identified in a Forescout Vedere Labs analysis of seven different BGP implementations: FRRouting, BIRD, OpenBGPd, Mikrotik RouterOS, Juniper JunOS, Cisco IOS, and Arista EOS.
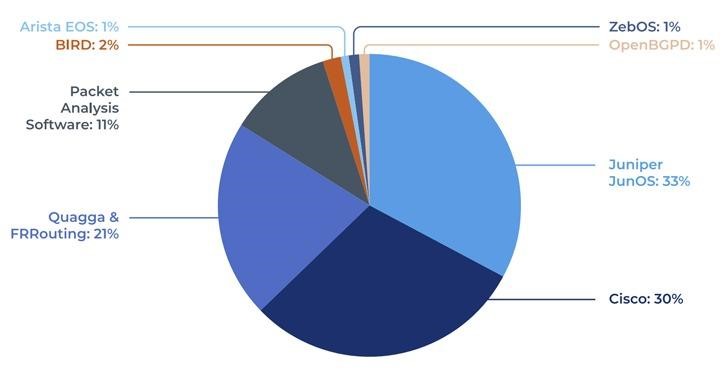
The list of deficiencies found is the following:
- CVE-2022-40302 (CVSS score 6.5) – out-of-bounds read when processing a malformed BGP OPEN message with the Extended Optional Parameters Length option;
- CVE-2022-40318 (CVSS score 6.5) – out-of-bounds read when processing a malformed BGP OPEN message with the Extended Optional Parameters Length option;
- CVE-2022-43681 (CVSS score 6.5) – Out-of-bounds read while processing a malformed BGP OPEN message.
The experts write that these issues “can be exploited by attackers to induce a DoS condition on vulnerable BGP peers, which will cause all BGP sessions and routing tables to be dropped and the peer to become unresponsive.”
Analysts attached to their report a link to a Python-based BGP Fuzzer open source tool that will help organizations test BGP security and find new flaws in its implementations.