In January 2022, a lot of cybercrime forums on the Darknet witnessed the appearance of a newbie on a stealer malware market – BlackGuard. Cybersecurity specialists from Zscaler analysed this malware and shared their opinion of this malware.
BlackGuard stealer sees a huge popularity
After its appearance at the beginning of 2022, this malware experienced a rapid surge of popularity. Almost simultaneously with its appearance, the old player of the stealer malware market – Raccoon – decided to voluntarily cease its activity. That likely gave a push to the popularity of a newbie – the king is dead, long live the king! This industry is a very competitive place, and any weakness (or moreover the stepdown) will surely be used by other actors.
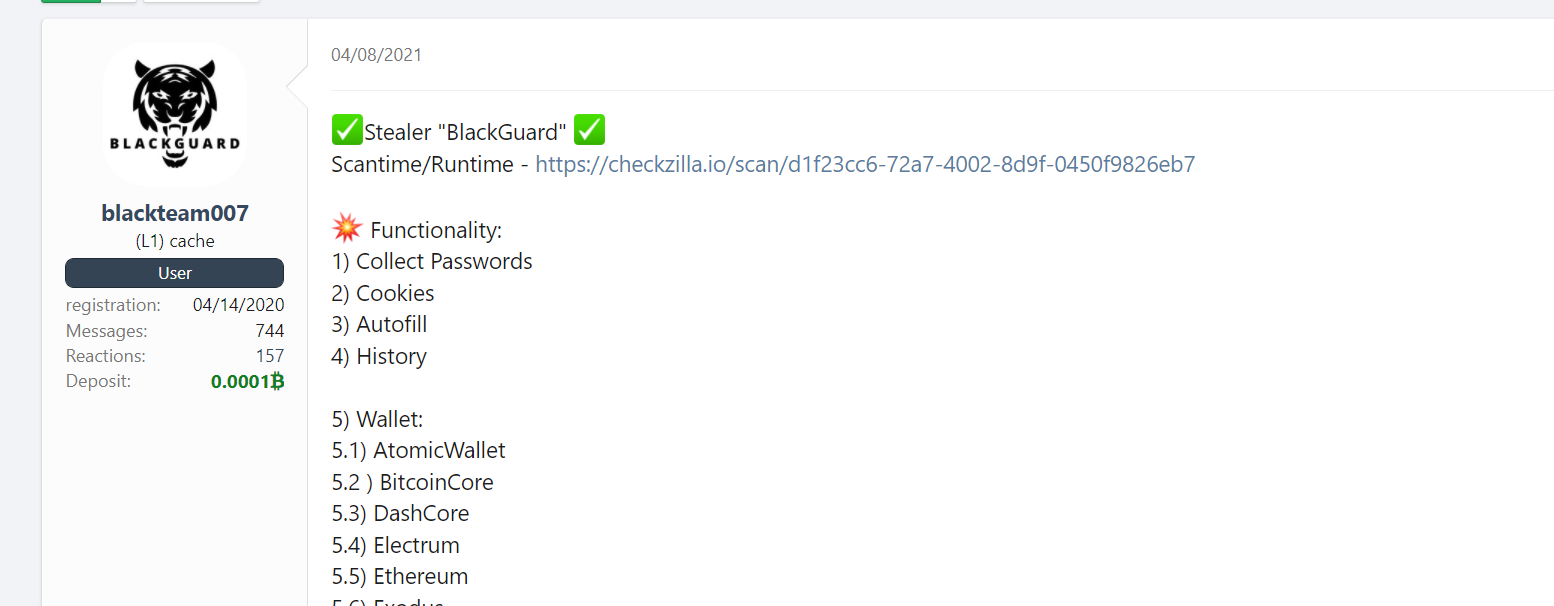
The offer to purchase a subscription for a BlackGuard stealer
BlackGuard stealer developers offer their malware in a form of malware-as-a-service, the same as Raccoon did. You may pay $200 for one month or $700 for a lifetime subscription. For subscribed “customers”, the developers offer full-time support and feedback sharing. Seems that malware developers and threat actors managed to bring a full-fledged service to the dark side of the cybersecurity world.
Several words on Raccoon Stealer
Raccoon Stealer was a bright star on the malware firmament. It was active since 2019, and its activity was more than noticeable. A lifespan of three years is pretty typical for modern malware: only sole examples exist for more than 4-5 years. The reasons to cease the activity are simple: they wish to change the field of activity, to change the malware branding, or attempt to destroy the possible evidence.
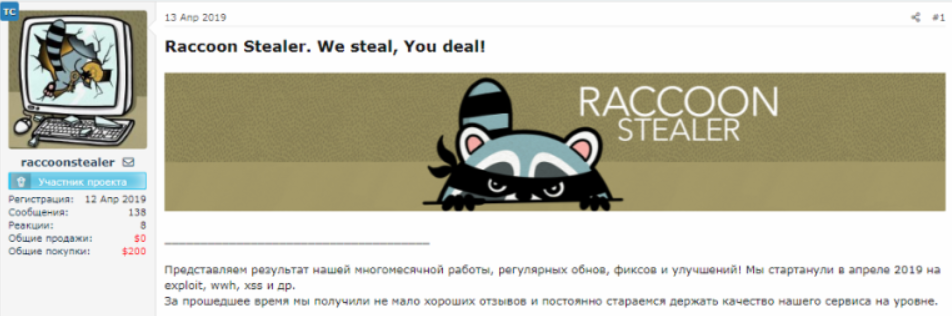
Analysts generally detected Raccoon malware during the attacks on individuals. For sure, crooks could use it for attacks on corporations, but there were no logged cases. And typical data types along with the interface features clearly show that it was not designed for cyberattacks on corporations. However, it was far away from becoming a common noun for stealers – there is no monopoly on the infostealer market.
What is so interesting about the BlackGuard stealer?
The Zscaler team analysed the malware offered on the forum. It has a pretty user-friendly web interface, which allows the cybercriminals to check the results – in numbers of stolen passwords, logs, banking credentials and other things. It also shows you the stats of victims by country – a pretty useful function when you don’t want to commit any cybercrimes in your or nearby country.
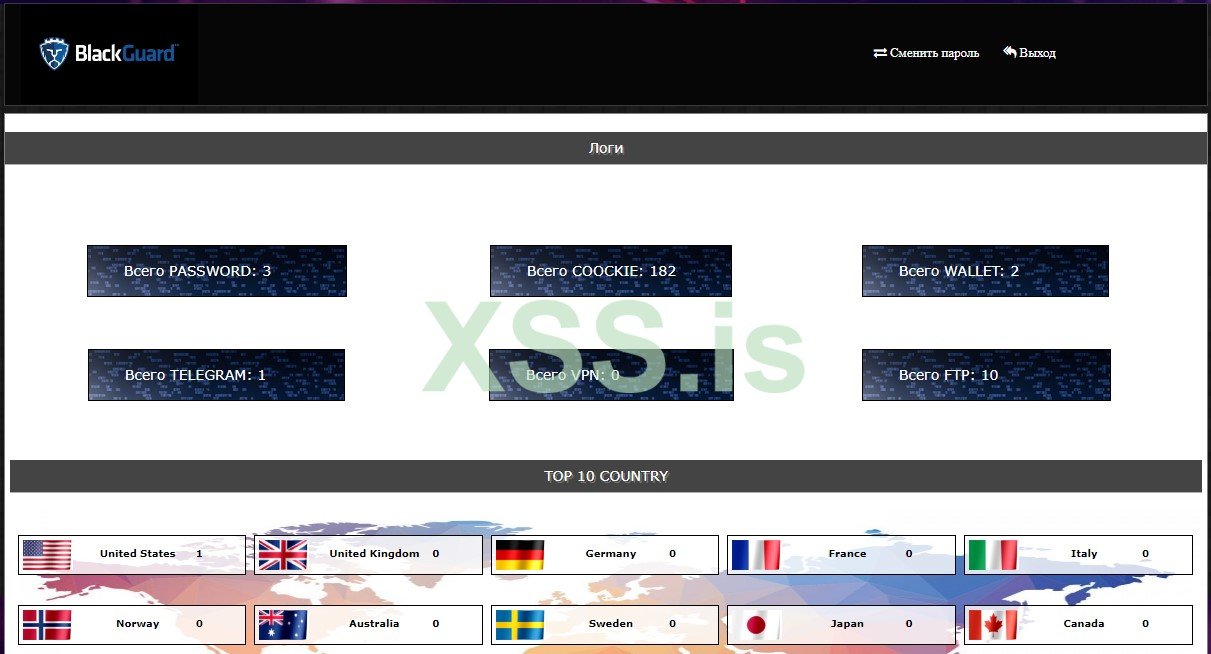
BlackGuard Stealer web interface
On different forums, users generally praise this stealer for taking much more data than the others. On the attached picture with the resulting logs of this stealer, you can see well-grouped data – with (crypto?)wallets credentials, logs of Telegram and Messenger chats, and the information related to cryptocurrency wallets from web browsers. This exact user seems to aim precisely on cryptowallets info.
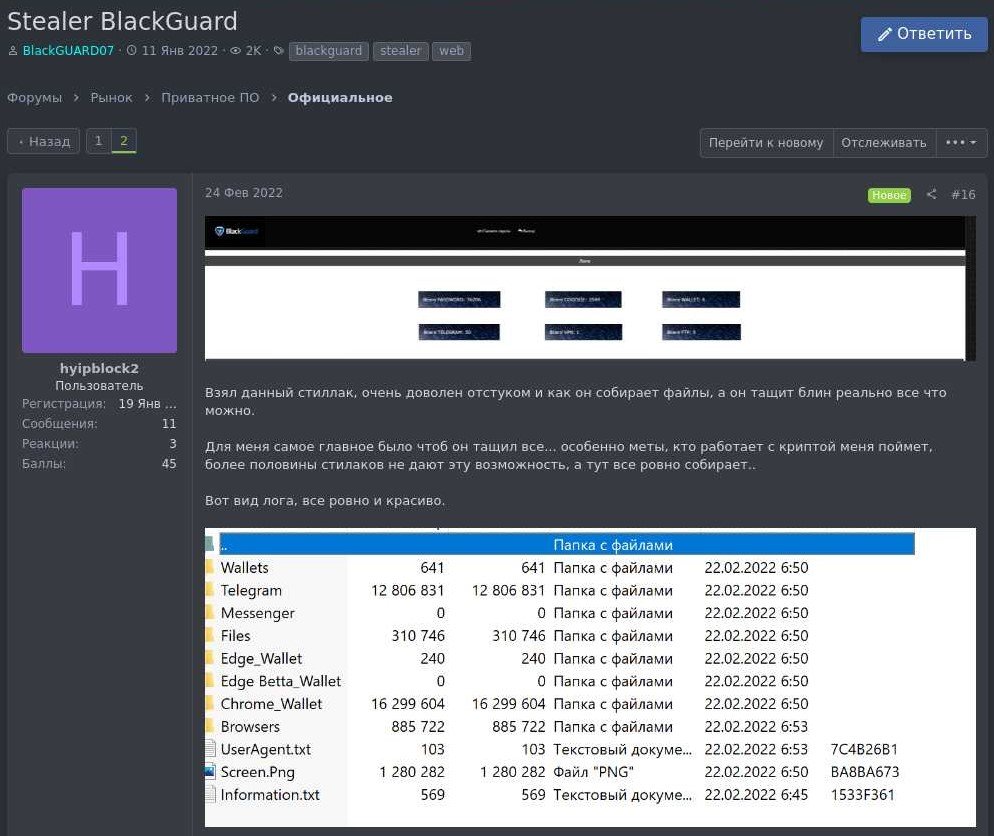
Took that stealerpack, I’m very pleased with the feedback and the way it takes the data, and it takes really everything. It is very important that it takes everything …especially meta files. Who works with crypto understands me. More than half of stealerpacks fail to do that, and this one makes it without any problems.
Cybersecurity analysts from Zscaler also got the list of applications that logs&other data that can be stolen with BlackGuard malware. It is a pretty big list of software – from messengers and mailing clients (Outlook) to VPN apps and browser extensions for cryptocurrency wallets.

List of the apps that BlackGuard Stealer aims at
What is stealer malware?
Stealer is a malware type that aims at grabbing certain types of victims’ data and sending it to the crook who controls it. The exact type of information is usually set before the attack. Sometimes, cybercriminals may aim at a certain file – for example, a valuable report. The common form of distribution for stealer malware is trojan viruses. It may appear on your PC under the guise of a driver updater, a useful self-made tool for performance boosting or so.
People are sometimes confused with stealers and spyware, thinking that these things are the same. Sure, they serve similar purposes – stealing data. However, spyware is rather about spying – taking geolocation and personal info, chats and keystrokes. Meanwhile, stealers aim at more static things – cookies, logs, passwords, browser history et cetera. The only thing that is common for both of them is the way of spreading.
Is BlackGuard worth being afraid of?
Just like all other stealers, it does not have a big spreading potential. In worst cases, such malware may infect a group of users who are interested in the same thing – for example, cryptocurrencies, certain games or traffic arbitrage. But still, the cybersecurity world has not witnessed even a single stealer pandemic. Sure, that does not mean that there is no hazard. But following the basic cybersecurity hygiene rules will likely save you from data leak&money loss.
BlackGuard stealer got its attention 100% deservedly. Pretty good functionality and easy interface make it easy to use even for beginners among cybercriminals. Seems it may requalify into a cryptostealer in future, or receive a fork/spin-off project in this direction. It has a lot of potential in that sector, and the developers will not miss that opportunity. However, it is always worth questioning yourself – if that money is worth a potential decade spent in jail? The question is purely rhetorical.
User Review
( vote)

