Script-based malware sounds like an oxymoron: such a benevolent thing as scripts are too easy to control, and it is not able to launch something really serious. But cybercriminals found their way to use these tiny things for malicious purposes.
Originally, scripts are small programs that consist of <100 code rows and were created as complements to the software you currently have. Launch the pack of programs by double click, set the certain task in Task Scheduler, enable/disable the certain system setting without doing a lot of excessive clicks. That’s not a lot – but gives a bit of comfort in using the operating system. And, as it often happens, someone found the way to exploit the thing that is initially designed as benevolent.
Can a script have a virus?
In fact, scripts were used to inject malware much earlier. Small quasi-programs were pretty popular for injecting the malware into the victim’s system. Moreover, these things were extremely easy to create. Common contents of such “instant malware” were viruses or worms. These malware types generally aim at mischief the user rather than on making money. Therefore, after malware converted into a 100% commercial thing, all simple script-based malware became pretty rare. The final strike on early script malware was the specific detection rule applied by all antiviruses – one that allowed preventively spotting the malicious scripts.
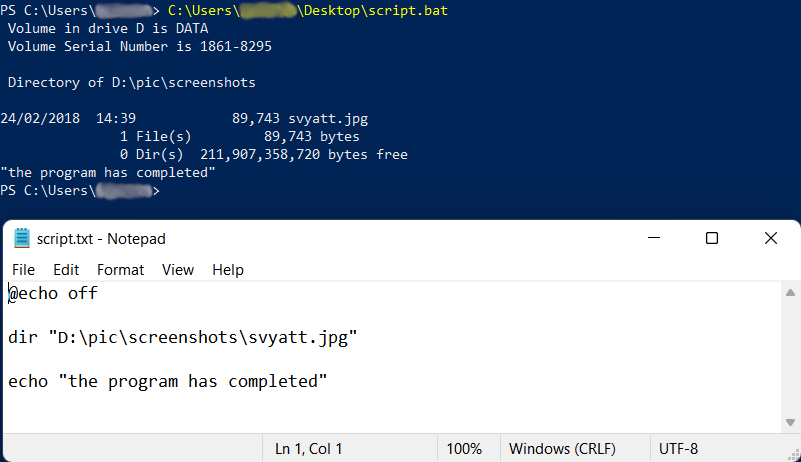
Script and its execution in Power Shell
Nonetheless, fraudsters could not miss such convenient things. Instead of using script-based malware as the carrier for malware, they added them into the malware spreading chain. Exactly, a big share of the downloader malware market is after modern variants of script malware. It is possible because of the security breaches in PowerShell, Command Prompt and other native elements of Windows. These console tools allow the scripts to connect to remote servers and download malware to the computer that executes this script. But let me explain this in more detail.
How can an attacker execute malware through a script?
As I have mentioned before, modern malware is not exactly in scripts. They just deliver these viruses to your system. After being launched, they establish a connection to the command server, download malware and start it1. Since antivirus software is able to stop the malware inside the script, fraudsters decided to keep it without the exact malware. Sure, viruses appear then – but it is too late to react. Usually, hackers do some preliminary actions to prevent the detection of malware by antivirus.
Execution
The exact process of script execution is conducted through the PowerShell – the normal environment for this purpose. Some scripts additionally exploit the vulnerabilities the PowerShell has – in order to give it more privileges and infect the whole network instead of a single PC, for example. Because of the scripts’ initial purpose – seamlessly speeding up the workflow – you will not even see any signs of unusual activity. Terminal windows, messages about new network connections, notifications about changed configurations – none of these things appear.
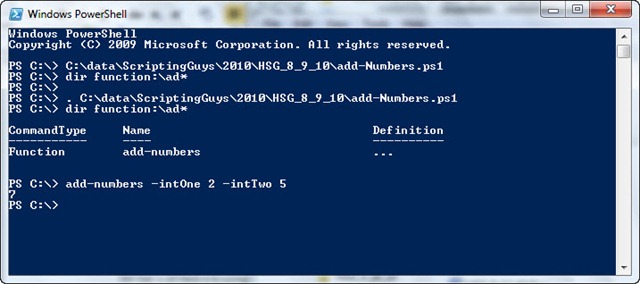
Script execution in Windows PowerShell
Script-based malware usage
Obviously, to inject something through the malicious script, you need to put this script into the computer first. Most of the bait emails contain exactly this thing – inside of the Microsoft Office document, or HTA file, for example. Almost always these scripts run entirely in the RAM, without any interaction with your disk drives. That makes it almost impossible to detect by regular antivirus scans and some of the heuristic rules. However, the other side of the coin is that this malicious script will stop at the system shutdown, and will not be able to launch without your “help”.
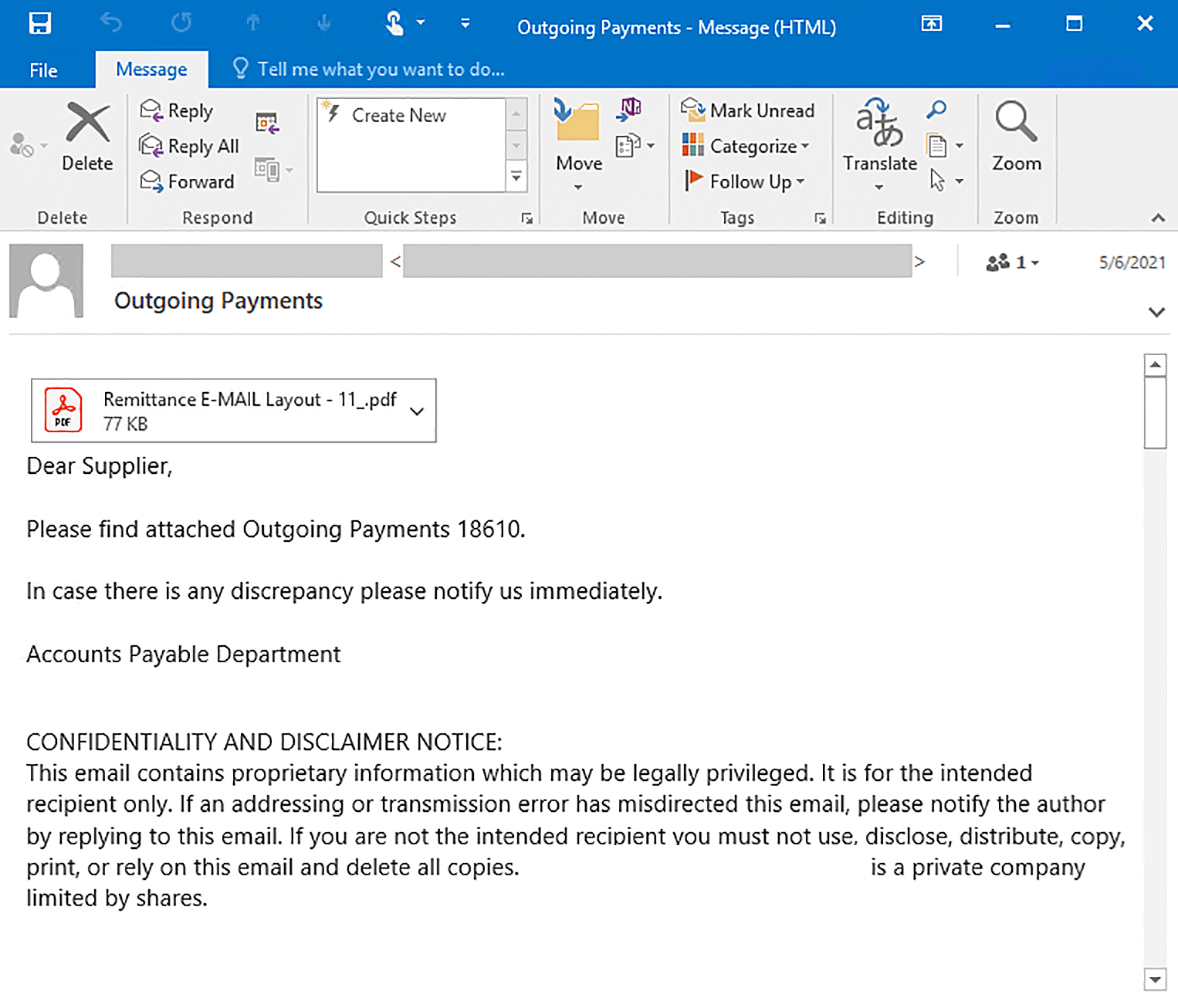
This MS Word file contains the malicious macro – it has a script inside
Besides bait emails, scripts are the often “complement” to the pirated software, as well as to the applications that help to pirate the programs. Keygens, “patches”, cheats and cheat engines – all these things commonly contain some small batch or script files. And you must launch these things manually to run the program. And when you are thinking only about the game, it is pretty easy to miss such a sly thing.
Is the script-based malware dangerous?
Enormously. Since it is capable of injecting everything under the sun, you can expect adware, spyware, ransomware – any of the existing malware types. The ease of use and high modifiability of the scripts allow the crooks to ignore your antivirus. This attack can even perform in an entire fileless form – meaning that scanning with antivirus is useless. If it does not have a proper heuristic engine, you and your PC are done.
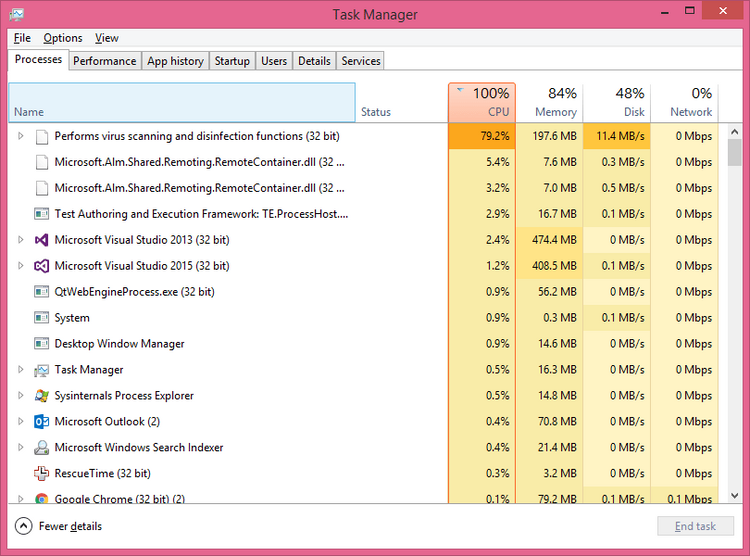
Attacks with script-based malware began spreading in mid-2020. Cybersecurity analysts who keep an eye on this type of attack say about thousands of attacks per month2. And there are even more attacks which victims did not say a word about. It is hard to count how much ransomware, spyware and other nasty pieces of malware were spread in that way. Do you want to have your files ciphered and confidential data stolen? I’m highly doubtful.
Protect you and your network from script-based malware
It is not so hard to make your system secure, even if we talk about such a tricky thing as scripts. These steps are easy, but require not only clicks but also your attention. Do not use untrustworthy and dubious programs like the aforementioned keygens. As I have explained, they have plenty of possibilities to carry a malicious script or two. Also, be very careful when checking your email box. Cybercriminals are mastering at disguising their messages for easier injection, making the email addresses similar to ones used by official senders. Fake FedEx delivery notifications or banking messages became a massive phenomenon in 2021.
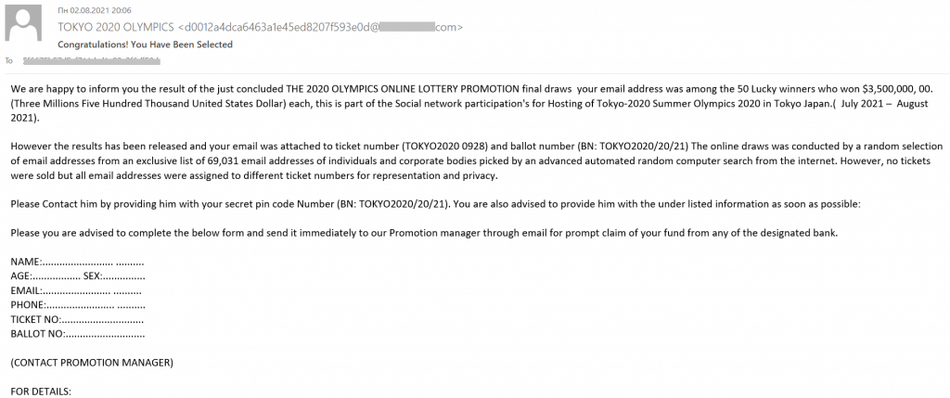
Each part of such messages must be examined carefully. Compare these notifications with the ones you have got earlier. It is also ideal to compare the email address in the message with addresses published on the official website of the supposed sender. And, of course, the ideal case is to remember all your incoming shipments – just to instantly detect the excessive notifications.
But being attentive is often not enough. There are dozens of possible injection ways, and you can never predict which one will be used, and who will be using the PC at the moment. To be sure that nothing bad will happen, use anti-malware software. You need one that is not just an ordinary security tool – you need the one that follows a “zero-trust” policy. Microsoft Defender in Windows 11 uses this rule by default, but it has a lot of other things to worry about.
User Review
( votes)References
- The full-featured report about script-based malware attack, with tracing and deep details.
- Report regarding the statistic of malware attacks, in particular – script-based ones.



