Threat Fabric analysts found five malicious dropper apps in the official Google Play store, downloaded more than 130,000 times in total that distribute SharkBot and Vultur banking trojans.
Let me remind you that we also talked about the fact that Administrators Removed 16 Apps with Clicker Malware from Google Play.The researchers note that Android droppers continue to evolve, offering hackers a convenient and stealthy way to infect devices:
The recently discovered malware targets 231 banking and cryptocurrency applications of financial institutions in Italy, the UK, Germany, Spain, Poland, Austria, the US, Australia, France, and the Netherlands.
In their report, the experts list the following malicious applications:
- Codice Fiscale 2022 (com.iatalytaxcode.app): 10,000+ downloads;
- File Manager Small, Lite (com.paskevicss752.usurf): no downloads;
- My Finances Tracker (com.all.finance.plus): 1000+ downloads;
- Recover Audio, Images & Videos (com.umac.recoverallfilepro): 100,000+ downloads;
- Zetter Authenticator (com.zetter.fastchecking): 10,000+ downloads.
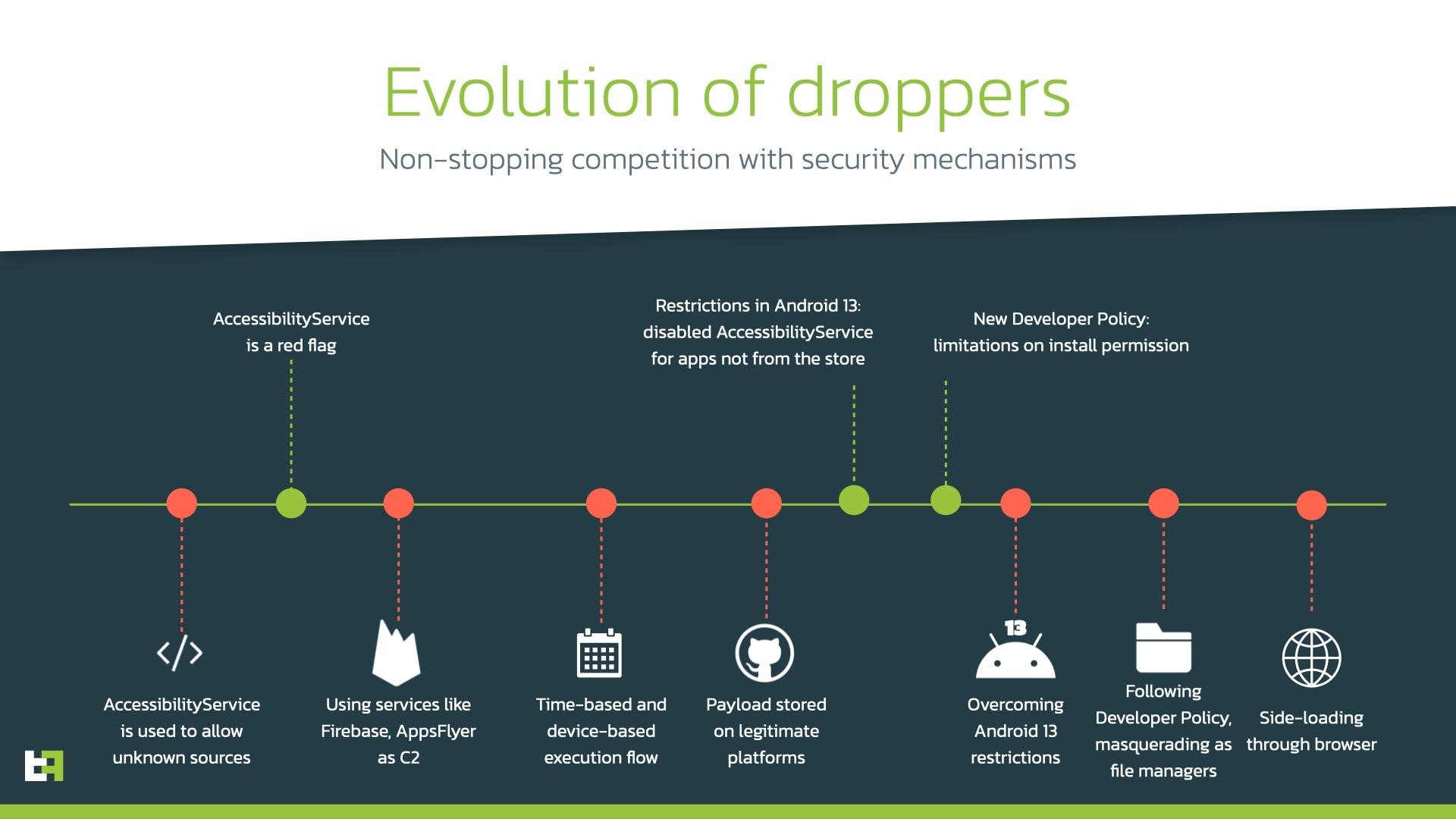
The first campaign detected by Threat Fabric in early October 2022 distributed the SharkBot banker to Italian users. This malware is able to steal credentials using fake login requests superimposed directly on legitimate login forms, perform keylogging, steal and hide SMS messages from the user, and take remote control of the infected device.
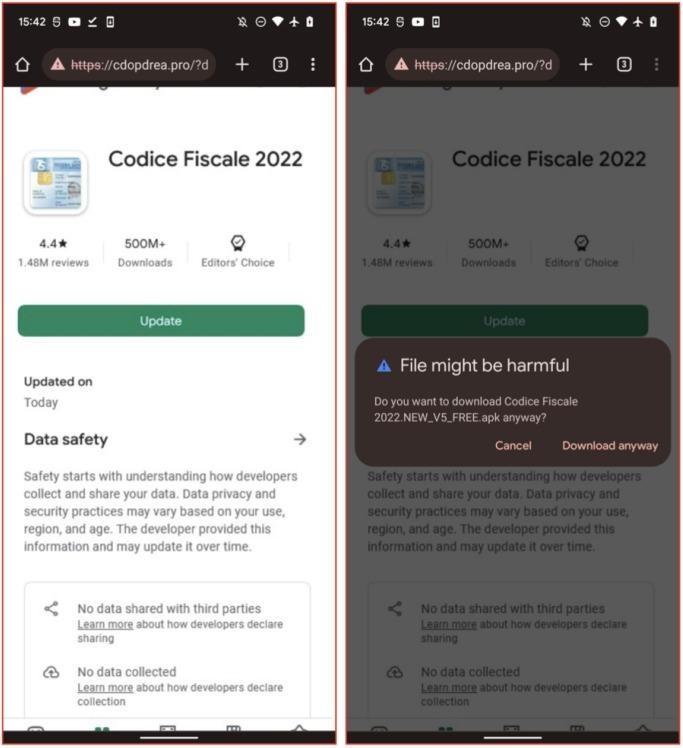
For SharkBot, the researchers found two dropper apps: Codice Fiscale 2022 and File Manager Small, Lite. When the user installed these applications, they soon prompted him to install a fake update that actually installed a Trojan.
Interestingly, when installing additional packages from a remote server, Google usually requires applications to request the REQUEST_INSTALL_PACKAGES permission. But newer versions of Android warn of the dangers of issuing such permission, making it harder for criminals to convince users to install the “upgrade.” Therefore, the dropper found by the researchers simply opens a web page that looks like Google Play, tricking the user into clicking the “Refresh” button in the browser and bypassing the need for this permission.
The second malware campaign was linked to the Vultur banking trojan, which is run by a hacking group known as the Brunhilda Project. Vultur is able to perform a variety of actions on the infected device, including streaming everything that happens on the screen, as well as keylogging for social networks and instant messengers.
The new version of Vultur distributed as part of this campaign also had previously unknown functionality for UI logging, recording clicks, gestures, and any actions performed by the victim on the device. Threat Fabric believes that the malware developers added this functionality to bypass Android security restrictions that prevent the content of certain application windows from being displayed in screenshots and screencasts.
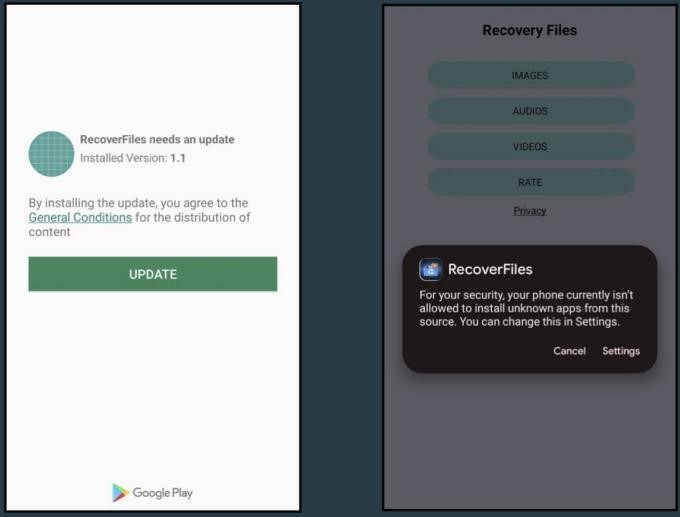
This Trojan was distributed by the Recover Audio, Images & Videos, Zetter Authentication and My Finances Tracker applications. Just like SharkBot droppers, these droppers also show the victim a request to install a fake update, disguised as a notification from Google Play. If the user allows the “update” to be installed, it will download and install the malware.
In order to avoid detection and bypass Google Play Store checks, droppers are not contained in applications immediately, but are loaded dynamically using a dex file that comes from the attackers’ control server. In addition, droppers use AES encryption for obfuscation to hide features from automatic scanners.

