Multiple vulnerabilities have been discovered in Nexx smart garage doors that can be used to control this device, disable home alarms and smart plugs. The manufacturer has not yet recognized and fixed the bugs described by the researcher.
Let me remind you that we also wrote that Vulnerabilities in Google Home Smart Speakers Allowed Eavesdropp Users, and also that Bypassing the Lock Screen on Pixel Smartphones Netted a Researcher $70,000.And there was also such a case that Avast expert taught Smarter Coffee machine to ransom money.
Numerous vulnerabilities were discovered at the end of 2022 by cybersecurity researcher Sam Sabetan. According to him, more than 40,000 smart devices located in both residential and commercial premises are affected by bugs. This week, the expert revealed the details of the vulnerabilities found, as he failed to contact the manufacturer and get the release of patches.
The US Infrastructure and Cybersecurity Agency (CISA) has already issued its own security bulletin, warning individuals and organizations using Nexx products about the vulnerabilities discovered by the researcher. CISA experts emphasize that problematic devices are used in commercial facilities around the world, but even they could not contact the manufacturer.
In total, the researcher found five vulnerabilities, most of which were assigned a “high” or “critical” danger rating. The bugs affect Nexx NXG-100B and NGX-200 garage door controllers running nxg200v-p3-4-1 or older, Nexx Smart Plug NXPG-100W running nxpg100cv4-0-0 and older, and Nexx Smart Alarm NXAL-100 with version nxal100v-p1-9-1 and older.
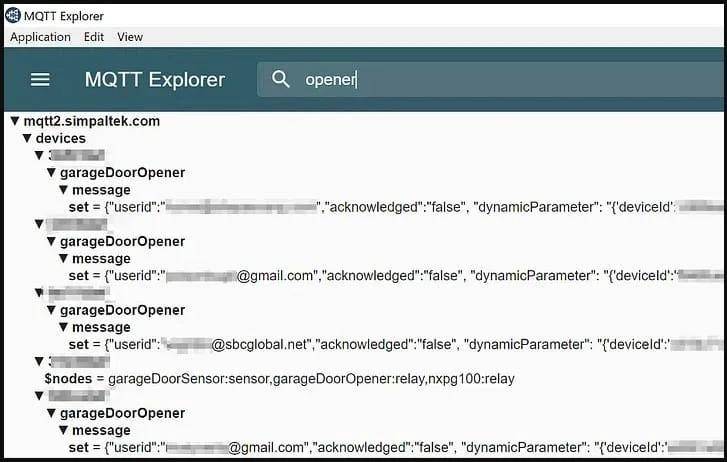
- CVE-2023-1748: Hardcoded credentials on listed devices that allow anyone to access the MQ telemetry server and remotely control any client devices (CVSS score of 9.3);
- CVE-2023-1749: Incorrect access control for API requests sent to valid device IDs (CVSS score of 6.5);
- CVE-2023-1750: Incorrect access control allowing attackers to gain access to the history of the device, information about it, and change settings (7.1 points on the CVSS scale);
- CVE-2023-1751: Invalid input validation that prevents the auth token from being matched to the device ID (CVSS score of 7.5);
- CVE-2023-1752: Incorrect authentication control allowing any user to register an already registered Nexx device using its MAC address (CVSS score of 8.1).
The most serious of these bugs is CVE-2023-1748. The bug is related to the fact that Nexx Cloud sets a universal password for all devices registered through the Nexx Home app for Android or iOS.
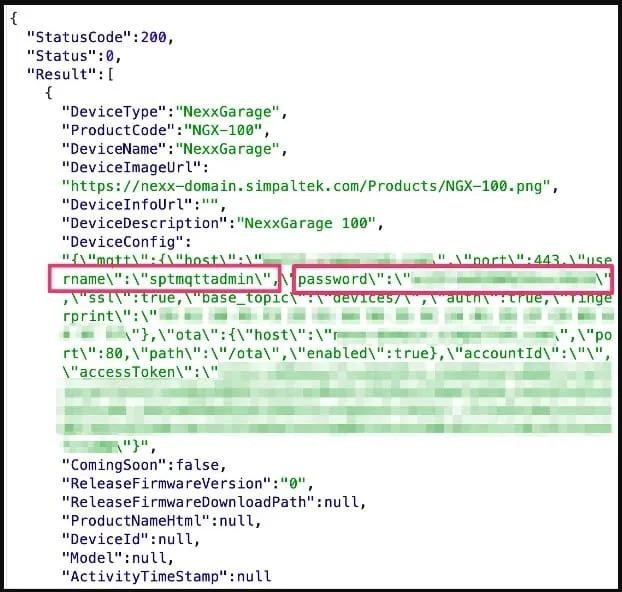
This password is available both in the API communication and in the firmware that comes with the device, so an attacker can easily learn it and send commands to the device via MQTT.