Proofpoint experts discovered that the Emotet malware has a new module designed to steal bank card data stored in the Chrome browser.
According to Proofpoint, the new module appeared on June 6, 2022 and attacks Chrome exclusively, passing the collected information to the control servers (different from those that usually use the map stealing module and the downloader module).Let me remind you that we wrote that Emotet compromised more than 4 million mailboxes.
It’s also worth noting that a week ago, Emotet began using Windows Shortcut (.LNK) files to execute PowerShell commands to infect victim systems, deprecating Microsoft Office macros, which have been disabled by default since early April 2022.
Let me remind you that in January last year, Europol, the FBI and law enforcement agencies in many countries of the world, including Canada, the Netherlands, France, Germany, Lithuania, the UK and Ukraine, conducted a large-scale coordinated operation to eliminate Emotet; preparation for the operation lasted two years. Then law enforcement officers managed to seize control over the botnet infrastructure, disrupting its operation. As a result, criminals lost the ability to use hacked machines, and the malware stopped spreading to new targets.
However, at the end of 2021, ten months after this operation, the researchers again discovered malware activity.
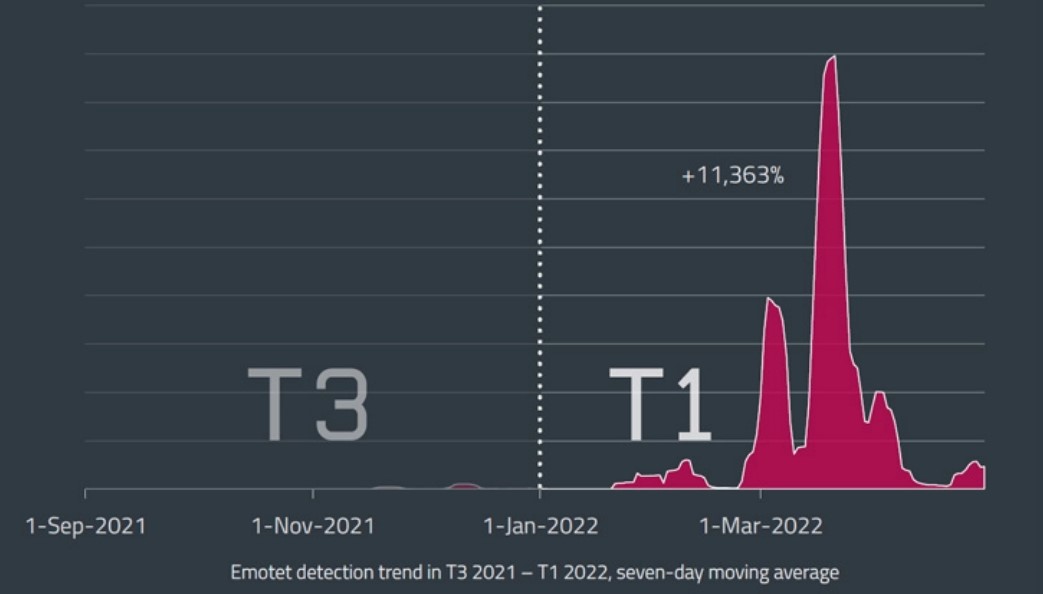
Since then, the malware has gradually gained momentum, and ESET recently reported that in March and April 2022, the number of Emotet detections increased by 100 times. Analysts recorded an increase of more than 11,000% during the first four months of the year (compared to the period from September to December 2021).
History of Emotet
Emotet appeared back in 2014, but only in recent years it has become one of the most active threats among malware.
The malware was distributed mainly through email spam, through malicious Word, Excel documents, and so on. Such emails could be disguised as invoices, waybills, account security warnings, invitations to a party, or as information about the spread of the coronavirus. In a word, hackers closely followed global trends and constantly improved bait emails.
Although Emotet once started out as a classic banking Trojan, the threat has since evolved into a powerful downloader with many modules, and its operators have begun to actively cooperate with other criminal groups.
Having penetrated the victim’s system, Emotet used the infected machine to send spam further, and also installed a variety of additional malware on the device. Often these were bankers such as TrickBot, miners, infostealers, as well as cryptographers like Ryuk, Conti, ProLock.
Europol called Emotet “the most dangerous malware in the world” and also “one of the most prominent botnets of the last decade.”

