The first “Patch Tuesday” this fall brought fixes more than 80 issues in Microsoft solutions, including a MSHTML vulnerability and residual PrintNightmare bugs.
Overall, 66 vulnerabilities were patched in various products, including Azure, Office, SharePoint Server, Windows, Windows DNS and Windows Subsystem for Linux, as well as another 20 Chromium bugs in Microsoft Edge.Only three issues this month have been categorized as critical. One of these vulnerabilities, CVE-2021-40444, is the already known 0-day in Microsoft MHTML (aka Trident), the proprietary Internet Explorer browser engine. Earlier it was reported that the problem was already being used in real attacks on Office 365 and Office 2019 users on Windows 10, and it soon became known that public and easy-to-use exploits were available for it.
Let me remind you that the vulnerability affects Windows Server 2008-2019 and Windows 8.1-10 (8.8 points out of 10 on the CVSS scale). Although MHTML was primarily used for the Internet Explorer browser, it is also used in Office applications to render web-based content within Word, Excel, and PowerPoint documents.
As Microsoft representatives explained, using this bug, an attacker can create a malicious ActiveX component that will be used by a Microsoft Office document and processed by MHTML. In fact, the attacker only has to convince the user to open such a malicious file, after that the attack can be considered a success.
Although patches are now available, some experts write that this protection may not last long. In their opinion, the bug is so deeply rooted in the core of Office that attackers can find new ways to abuse the problem, as is obvious in the case with the PrintNightmare vulnerabilities, which will be discussed below.
This summer, under the name PrintNightmare, a whole class of vulnerabilities (CVE-2021-1675, CVE-2021-34527 and CVE-2021-36958) were merged that affect the Windows Print Spooler service, print drivers and the Windows Point and Print.
Microsoft already released patches for CVE-2021-1675 and CVE-2021-34527 in July and August of this year, but researchers found that the problems are still not completely fixed, and attackers can still gain System-level privileges by simply connecting to remote print server. This issue has been assigned the ID CVE-2021-36958. As a result, this entire set of vulnerabilities was adopted by extortionist groups.
Today Microsoft has finally released a patch for the latest PrintNightmare bug, CVE-2021-36958. Mimikatz developer Benjamin Delpy, who previously discovered and proved the ineffectiveness of patches, this time confirmed that the problem has been fixed.
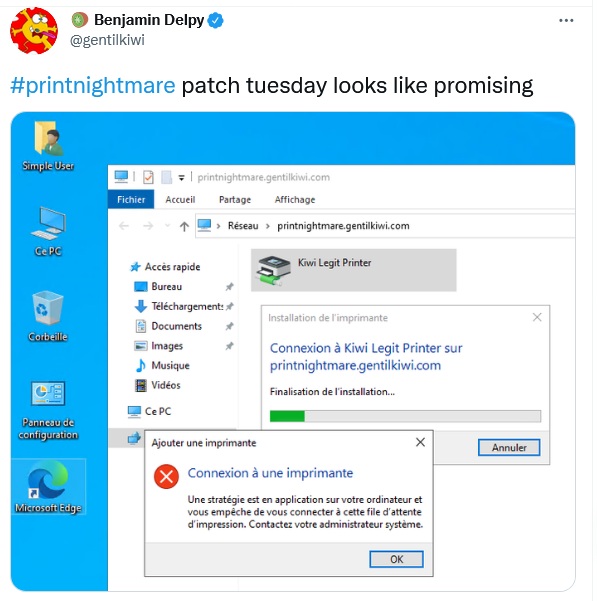
In addition, Delpy told Bleeping Computer that with the September updates, Microsoft disabled CopyFiles by default and added an undocumented Group Policy to the OS that allows administrators to re-enable it. This policy can be found in the Windows registry (HKLM\Software\Policies\Microsoft\Windows NT\Printers) under the name CopyFilesPolicy. If set to 1, CopyFiles will work again.
Journalists note that this change affects the default behavior of Windows, and it is not yet clear what problems this may entail when printing. So far, Microsoft hasn’t released any information about the new Group Policy.

