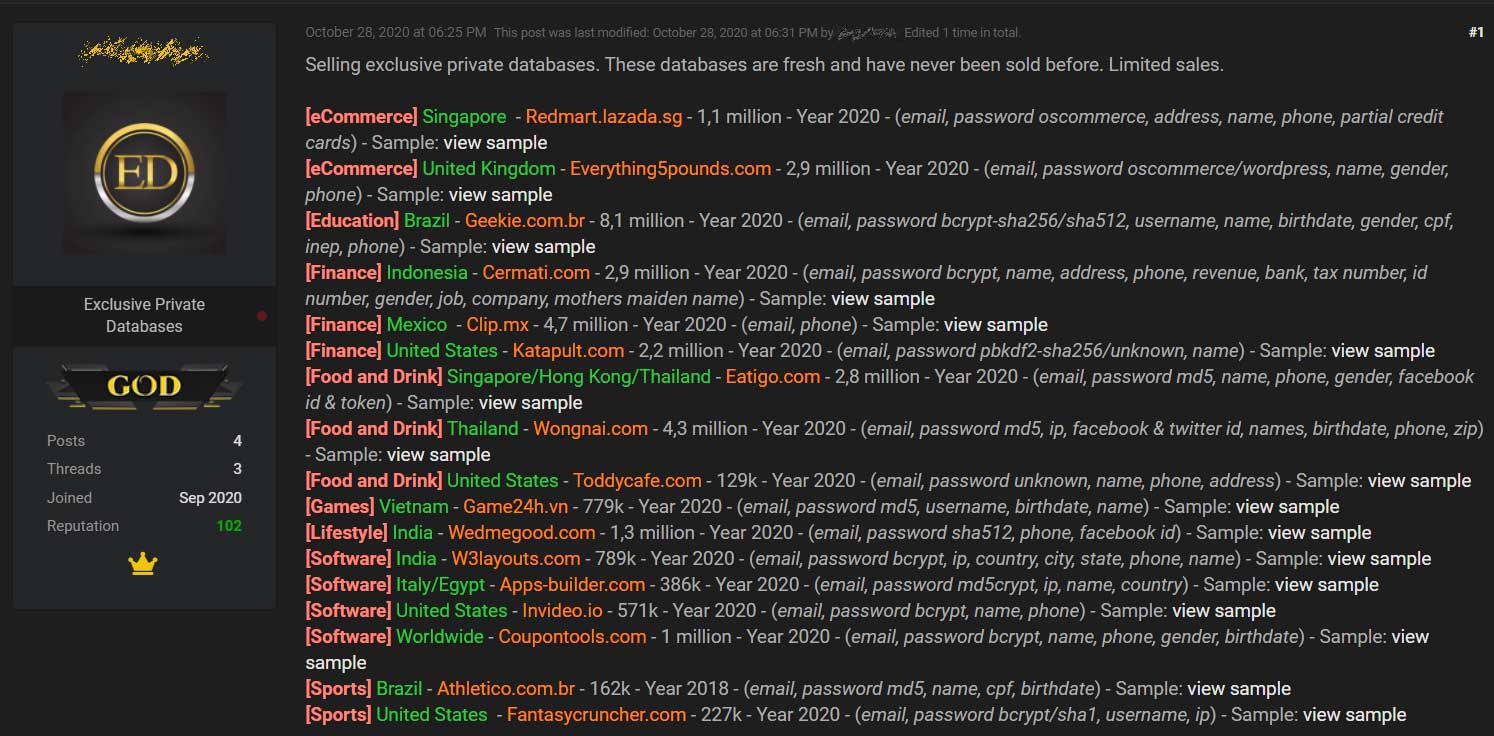
Bleeping Computer reporters found that a database of 34 million users is being sold on the darknet. The seller claims that this information was stolen from 17 different companies.
This lot went on sale on October 28, 2020. When the journalists contacted the seller and asked where this data was taken from, he replied that he was acting exclusively in the role of a broker and had nothing to do with the hacking of companies themselves. Therefore, how exactly and who hacked the affected companies is still unknown.It is reported that attackers obtained all seventeen databases in 2020. The largest leak occurred at Geekie.com.br – 8,100,000 records were stolen. The most famous affected company is Singapore-based RedMart (1,100,000 records), whose database was valued by the seller at $1,500.
Notably, none of the 17 companies have previously reported any security issues or data breaches. Only after Bleeping Computer reporters have contacted all the victims, the RedMart representatives disclosed the data leak, and Wongnai.com representatives said they were investigating the incident.According to the seller, the following information is available about the users of each company:
- Redmart.lazada.sg: email, passwords (SHA1), postal and billing addresses, full usernames, phone numbers, partial credit card numbers and expiration dates;
- Everything5pounds.com: email, hashed passwords, names, gender, phone numbers;
- Geekie.com.br: email, passwords (bcrypt-sha256 / sha512), username, names, DoB, gender, mobile phone number, Brazilian CPF numbers;
- Cermati.com: email, passwords (bcrypt), names, addresses, phone numbers, income information, bank, taxpayer number, ID number, gender, job data, company, mother’s maiden name;
- Clip.mx: email, phone;
- Katapult.com: email, passwords (pbkdf2-sha256/unknown), names;
- Eatigo.com: email, passwords (md5), names, phone numbers, gender, Facebook IDs and tokens;
- Wongnai.com: email, passwords (md5), IP addresses, Facebook and Twitter IDs, names, date of birth, phone numbers, zip codes;
- Toddycafe.com: email, passwords, names, phone numbers, addresses;
- Game24h.vn: email, passwords (md5), username, dates of birth, names;
- Wedmegood.com: email, pairs (sha512), phones, Facebook IDs;
- W3layouts.com: email, passwords (bcrypt), IP addresses, countries, cities, states, phones, names;
- Apps-builder.com: email, passwords (md5crypt), IP addresses, names, countries;
- Invideo.io: email, passwords (bcrypt), names, phone numbers;
- Coupontools.com: email, passwords (bcrypt), names, phone numbers, gender, date of birth;
- Athletico.com.br: email, passwords (md5), names, CPF, dates of birth;
- Fantasycruncher.com: email, password (bcrypt / sha1), username, username, IP addresses.
Bleeping Computer reporters examined the database samples provided by the attackers and confirmed that the email addresses correspond to user accounts of 13 of the 17 compromised service companies. Only Clip.mx, Katapult, CouponTools, or Aps-builder.com accounts could not be verified.
Although there is no official confirmation of the hacks yet, the researchers still recommend that users of the listed companies and services consider the threat and change their passwords immediately.
Let me remind you that researchers discovered leak of personal data of millions of Yves Rocher customers.