Researchers have noticed that already two hacker groups have begun to use a new tactic to force their victims to pay a ransom: hackers have added search functionality to their sites.
You might also be interested to know what More than 25 hacker groups work under the “Ransomware as a Service” model.The Bleeping Computer edition writes that last week the extortionist group ALPHV (aka BlackCat) announced the creation of a database with leaks, which contains the data of “non-payers”.
The hackers say these repositories are indexed and searchable, either by filename or by content available in documents and images.
Journalists note that the accuracy of the results so far is imperfect and leaves much to be desired.
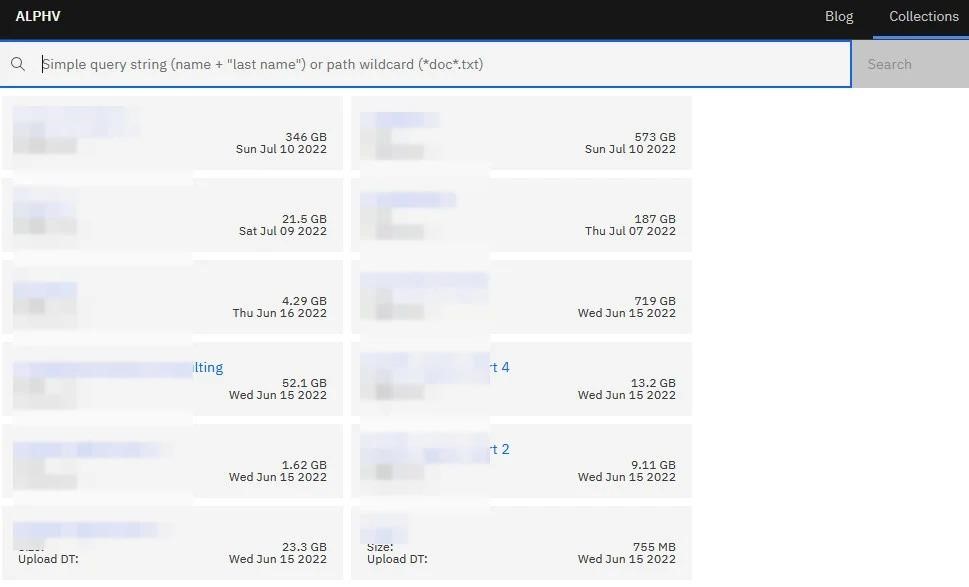
BlackCat operators claim that the innovation will make it easier for other cybercriminals to guess passwords and find confidential information about companies.
Let me remind you that we wrote that In 4 months, the Black Cat group hacked 60 organizations around the world.
Hackers tried a similar trick in mid-June when they created a website with data stolen in an attack on an Oregon hotel and invited guests and employees to check if their personal information was stolen during this incident.
In addition, journalists note that the updated version of the LockBit ransomware website also has a search that allows finding a specific company in a long list of victims of the group. Search has also appeared on the Karakurt ransomware site, but the function is not working properly yet.
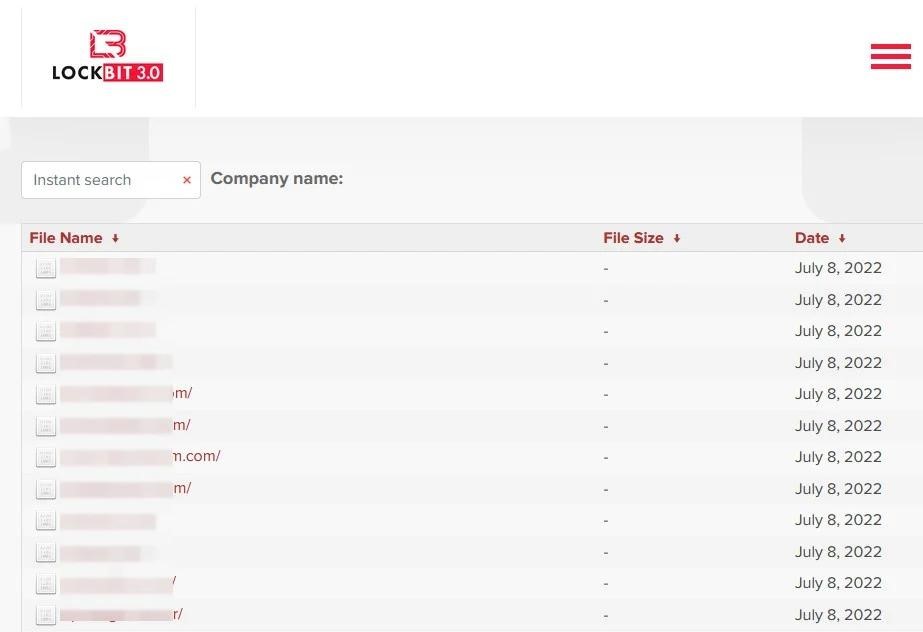
The researchers conclude that search functions seem to be a new form of pressure on the victims, and thus the attackers induce companies to pay a ransom, promising to remove data or mention of hacks from the public domain afterward.

