Experts warn that hackers are moving from using the well-known Cobalt Strike to the less popular red team tool, the Brute Ratel Command and Control Center (Brute Ratel C4 or BRc4).
So, Palo Alto Unit 42 analysts found that the BRc4 had already been adopted by the Russian-speaking hack group APT29 (aka CozyBear and Dukes).It’s worth recalling here that Cobalt Strike is a legitimate commercial tool built for pentesters and the red team and focused on exploitation and post-exploitation. Unfortunately, it has long been loved by hackers ranging from government APT groups to ransomware operators.
Although Cobalt Strike is quite expensive and inaccessible to ordinary users, attackers still find ways to use it (for example, rely on old, pirated and hacked versions).
Let me remind you that we wrote that Ransomware operators use Cobalt Strike in 66% of cases.

Chetan Nayak
In 2020, Chetan Nayak, a former red team member in Mandiant and CrowdStrike, created the BRc4 as an alternative to Cobalt Strike. The instruments turned out to be similar to each other and not at the same time. For example, Cobalt Strike allows to deploy “beacons” on compromised devices to remotely monitor the network or execute commands. In turn, Brute Ratel allows to deploy “badgers” (badgers) to remote hosts, which are very similar to beacons in Cobalt Strike. Such “badgers” connect to the attacker’s control server in order to receive commands or transmit the results of already launched commands to operators.
As Palo Alto Unit 42 experts note, attackers have recently begun to switch from Cobalt Strike to using Brute Ratel, preferring this particular toolkit for post-exploitation. Since BRc4 is largely focused on evading detection by EDR and antivirus solutions, almost all security products do not detect malware in it. Because of this feature, researchers call the Brute Ratel “uniquely dangerous.”
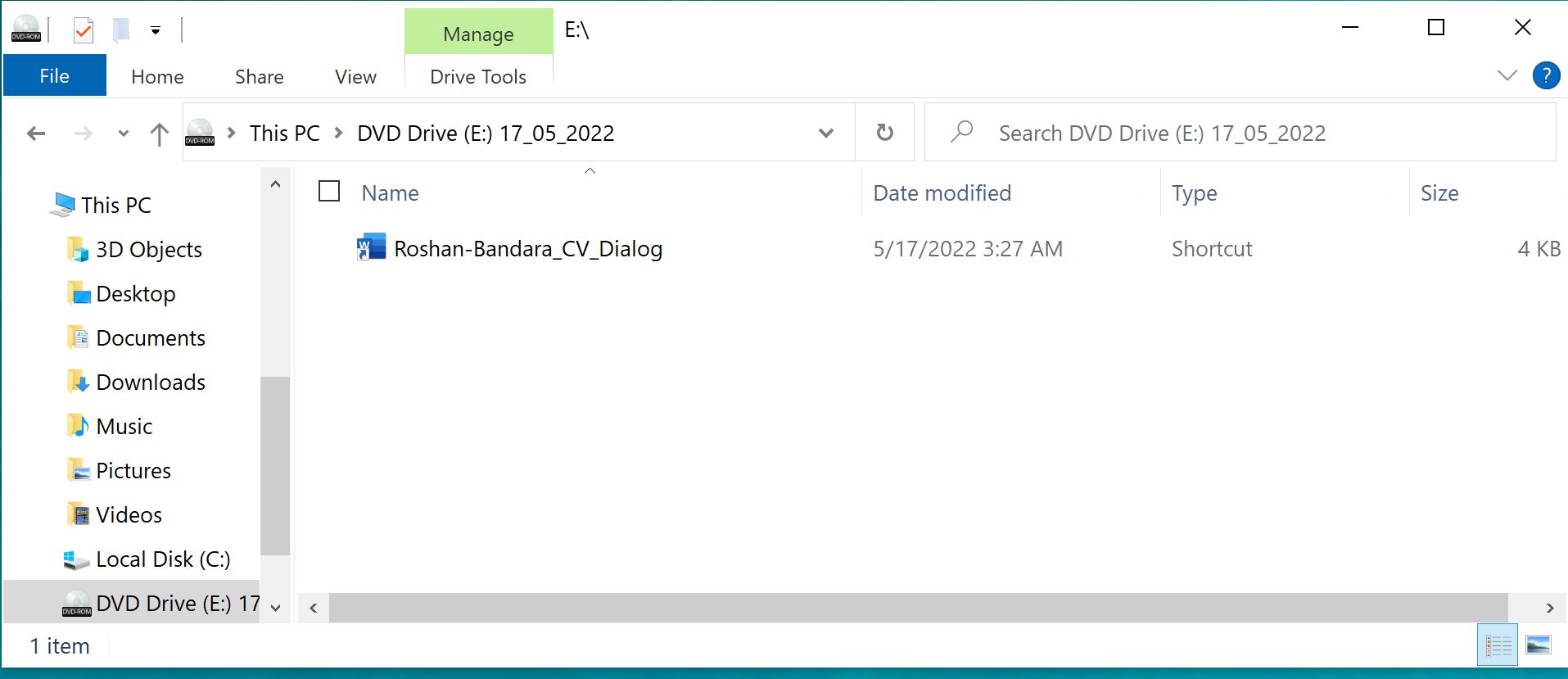
The experts found that BRc4 had already been used during attacks allegedly related to the Russian-language hack group APT29, during which the attackers distributed malicious ISO images purporting to contain a resume (CV). In fact, the resume file (Roshan-Bandara_CV_Dialog) was a Windows shortcut that launched the associated OneDriveUpdater.exe file.
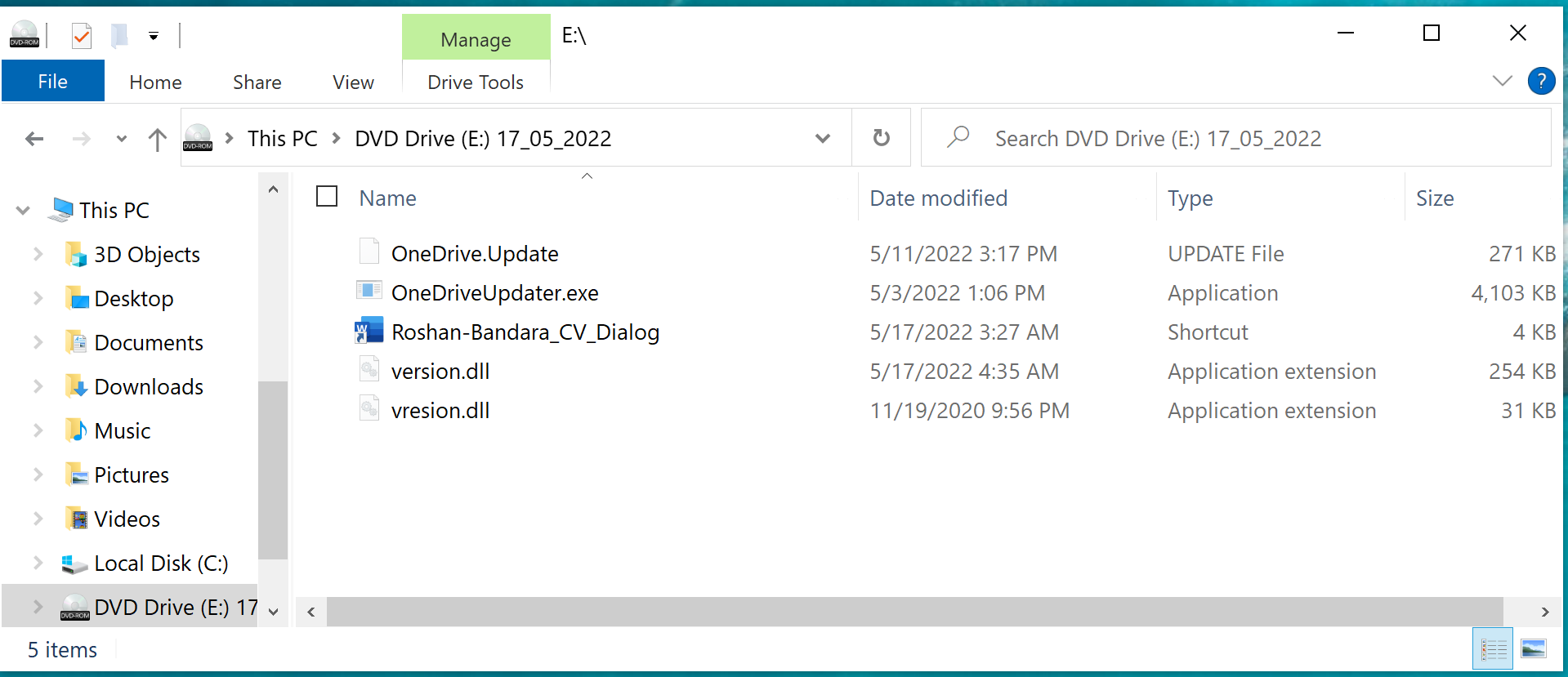
While OneDriveUpdater.exe is a regular Microsoft executable, the included version.dll has been modified to act as a bootloader for the Brute Ratel badger, which is loaded into the RuntimeBroker.exe process. After that, the attackers gained remote access to the compromised device to execute commands and further move through the network.
Brute Ratel currently costs $2,500 per user for an annual license, with customers required to provide a work email address and pass verification before obtaining a license. Since the verification is done manually (although it is not known exactly how), the question arises, how do attackers get licenses? The fact is that the expert report emphasized that the mentioned ISO image was created on the same day when the new version of BRC4 was released.
Chitan Nayak told Bleeping Computer reporters that the license used in the described attacks was leaked to the side by a disgruntled employee of one of his clients. Since the payloads allow Nyack to see who they belong to, he claims to have been able to identify and revoke the license.
However, according to the head of AdvIntel Vitali Kremez, this is not an isolated case. For example, the former operators of the Conti ransomware also acquired Brute Ratel licenses, creating shell American companies for this purpose.

Vitali Kremez
In their report, Palo Alto Unit 42 analysts summarize that the Brute Ratel could pose a serious threat that must be learned to counter:

