Information security company Malwarebytes drew attention to the fact that hackers are attacking Russian organizations, including a large defense contractor, using a recently fixed bug in MHTML.
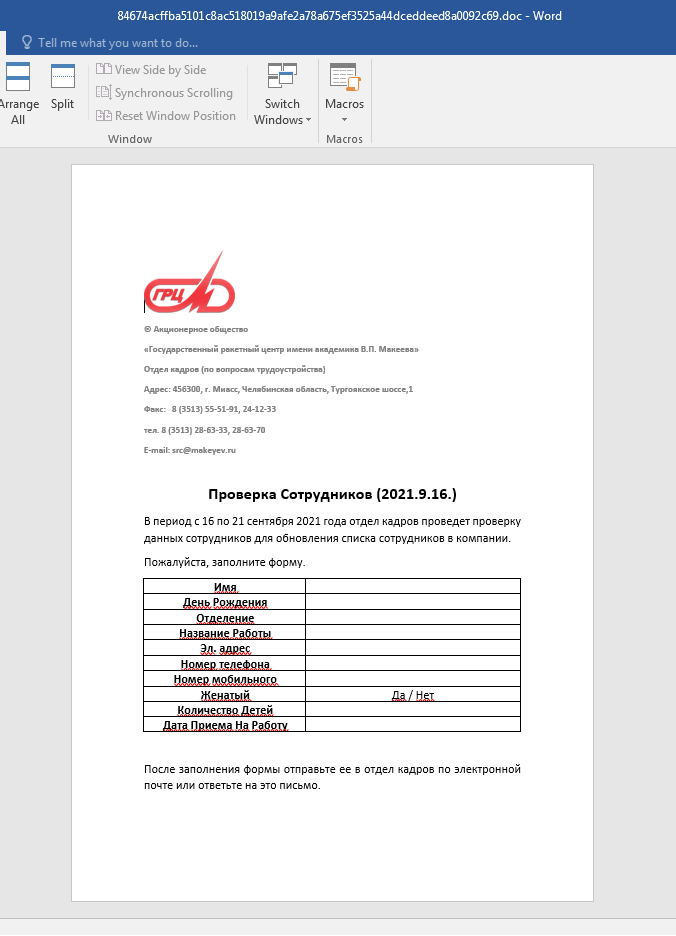
The researchers write that one of the targets of the unknown attackers was the JSC “State Missile Center named after Academician V. P. Makeev” (JSC “GRTs Makeev”) – a Russian developer of ballistic missiles for submarines, one of the largest research space technology.The attacks were classic spear phishing, with employees receiving messages containing malicious Office documents. The decoys looked like Word files supposedly created by the company’s HR department. Employees were asked to fill out a form and send it to Human Resources or by responding to a letter.
The fact is that the attackers exploited the CVE-2021-40444 problem, that is, a 0-day bug in Microsoft MHTML (aka Trident), the proprietary Internet Explorer browser engine.
The vulnerability could be exploited through Office files to run malicious code on unsecured Windows systems.
Let me remind you that earlier it was reported that the problem is already being used in real attacks on users of Office 365 and Office 2019 in Windows 10, and soon it became known that public and easy-to-use exploits were available for it. A patch has already been released for the vulnerability.
The researchers also found other Office documents containing the same exploit, but the decoys were written on behalf of the Interior Ministry and disguised as fines.
Malwarebytes reports that it has failed to link these documents to specific targets. It is assumed that “government” hackers of a certain country are behind these attacks, but it is not known which one.