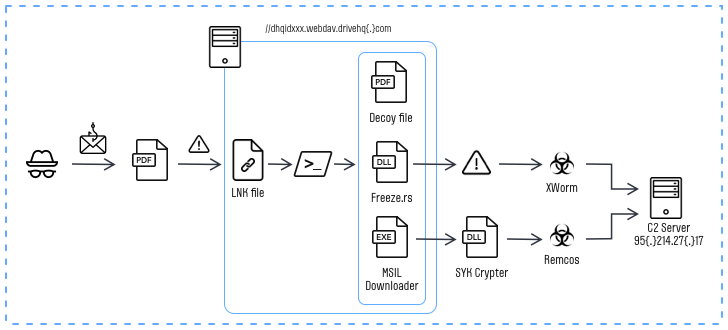
Hackers use multi-stage attacks to inject multiple remote-access trojans (RAT). The scheme involves Freeze.rs – open-source greyware used to circumvent protective mechanisms and execute the shellcode. Through such a campaign, crooks deploy XWorm and Remcos RATs at least since July 13, 2023.
Hackers Deploy Multiple Remote Access Trojans In One Attack
The attack begins with a phishing email containing a malicious PDF file. Upon execution, this file redirects the victim to an HTML file and utilizes the “search-ms” protocol to access a remote server-hosted LNK file (essentially a regular shortcut with embedded launch parameters), as explained by experts. Upon launching the malicious shortcut, a PowerShell script is executed, initiating the Freeze.rs and SYK Crypter injectors for further malicious actions.
At the final stage, the decrypted shell code executes the XWorm remote access trojan and gathers confidential data, such as computer information, screenshots, keystrokes, while also remotely controlling the compromised device. Additionally, alongside XWorm, seemingly to broaden malicious capabilities, another remote access trojan – Remcos RAT – is launched on the victim’s computer.
About Freeze.rs and SYK Crypter
Released in May of this year, Freeze.rs is a legitimate hacking tool designed to bypass security measures and execute shell code discreetly. It’s available for download on GitHub, which supposes it is initially a proof of concept malware, or an educational sample.
SYK Crypter is a downloader malware employed to distribute various malware programs. Among its favorites are AsyncRAT, NanoCore RAT, njRAT, QuasarRAT, RedLine Stealer, and Warzone RAT (also known as Ave Maria). SYK Crypter is loaded through a .NET loader attached to emails disguised as innocuous purchase orders.
Is that campaign dangerous?
The conclusions of FortiGuard researchers are similar: files masquerade as PDFs but are actually malicious shortcuts that execute a PowerShell script to trigger a Rust-based injector, displaying a decoy PDF document to divert suspicion. The primary targets of this malicious campaign are Europe and North America. Such a target pick is typical for hackers from Russia, China and the Middle East.
The fact that the relatively new hacking tool, Freeze.rs, which was released just 3 months ago, is already being used in real-world attacks, signifies the rapid decision-making by threat actors who seize the opportunity to arm themselves with new effective tools to achieve their objectives.
How to protect against cyberattacks?
Understanding the ways malware is getting infiltrated into your system already halves the effort on protection against it. Fortunately, cybersecurity elaborated enough ways to protect and prevent email spam and multi-stage malware injections. Here are some of them:
Use reliable anti-malware software. This advice is both preventive and reactive to malicious software. A well-done anti-malware program, like GridinSoft Anti-Malware, will diligently protect your system from possible attacks from any vector. Whether you run a questionable attachment, a cracked program or open a strange link, the program will instantly block the malicious item.
Be vigilant when dealing with email messages. Over the last 5 years, email spam has become a prevalent way of malware spreading. It is not that hard to convince someone to open the attachment – by pretending it is sent by a genuine company rather than a cunning fraudster. Dealing with consequences of such a trust though is not that easy.
Never run questionable files. Wherever they come from – email attachments, online forums, strangely-looking sites that try to resemble the downloading pages of genuine software – never trust them blindly. Even when you trust the one who sends it, consider scanning the file with anti-malware software or using web sandboxes like VirusTotal.