Check Point experts have again discovered the AlienBot banker and the MRAT Trojan on the Google Play Store. This time, nine applications included the Clast82 dropper, which was distributing this malware.
The malicious activity was reportedly involved in Cake VPN, Pacific VPN, eVPN, BeatPlayer, QR/Barcode Scanner MAX, Music Player, tooltipnatorlibrary and QRecorder applications. All of them copied the functionality of existing open source applications, and were removed from the official catalog in early February. In total, these applications have been installed about 15,000 times.To avoid detection, the malware developer used Firebase as a control platform, and also used GitHub to download payloads. In addition, according to the researchers, the dropper itself made decision, when to activate the malicious functions.
Basically, the parameter was set to “false” until the app passed all Google reviews and was published on the Google Play Store.
At the same time, for each malicious application, the hacker has a separate developer account on Google Play and a repository on GitHub. This allowed the attacker to distribute various payloads between infected devices more conveniently.
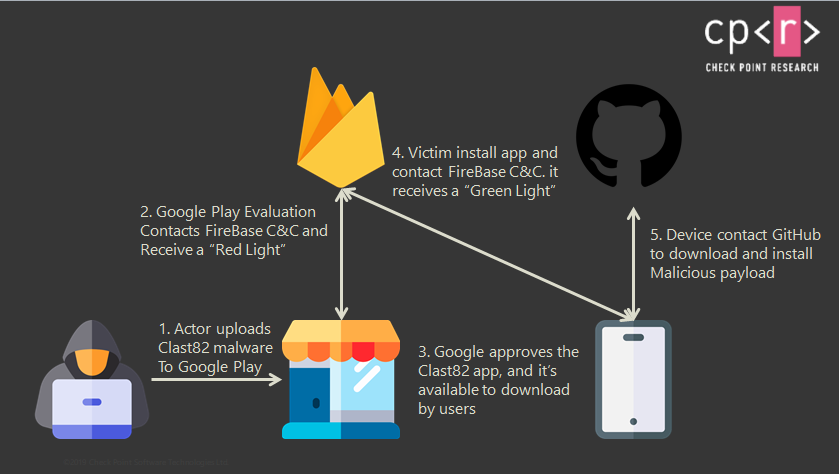
In terms of payloads, MRAT is used to remotely access a compromised device, while AlienBot is a MaaS tool (Malware-as-a-Service) that allows an attacker to inject malicious code into a victim’s legitimate financial applications. As a result, the attacker gains access to user accounts and full control over his device.
Let me remind you that a Child helped to detect malware in the Google Play, downloaded over 2.4 million times.

