Sysdig experts have found that more than 1,600 images on Docker Hub demonstrate various malicious behaviors. They can hide cryptocurrency miners, built-in secrets that can be used as backdoors, DNS compromise malware, and website redirectors.
Let me remind you that we also wrote that Many Repositories on GitHub Are Cloned and Distribute Malware, and also that Dozens of PyPI Packages Distribute W4SP Malware.More and more attackers are abusing Docker Hub, and more than a thousand malicious images pose a serious threat to unsuspecting users, researchers warn. After all, such dangerous images are eventually deployed in local or cloud containers.
It is noted that many malicious images use tiposquatting, that is, names that are as similar as possible to the names of popular projects, that is, attackers clearly seek to force victims to accidentally download them. Unfortunately, this tactic does not work well, for example, thanks to it, the two images from the illustration below were downloaded almost 17,000 times.
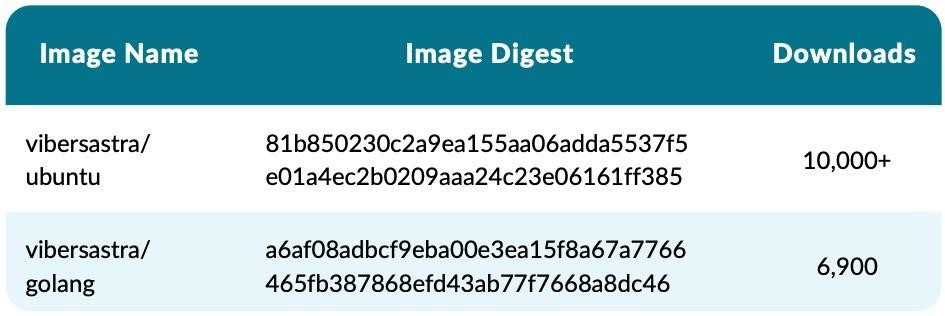
The expert report says that in addition to the images checked by the Docker Library Project, the service contains hundreds of thousands of images with an unknown status. To check them, Sysdig used automated scanners, carefully examining 250,000 unverified Linux images. As a result, 1652 of them turned out to be malicious.
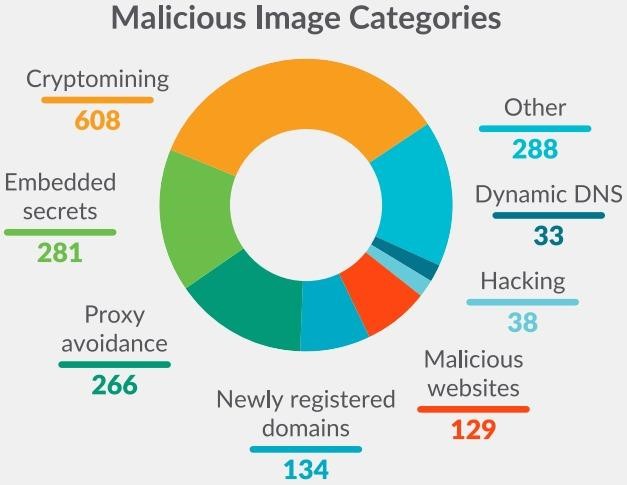
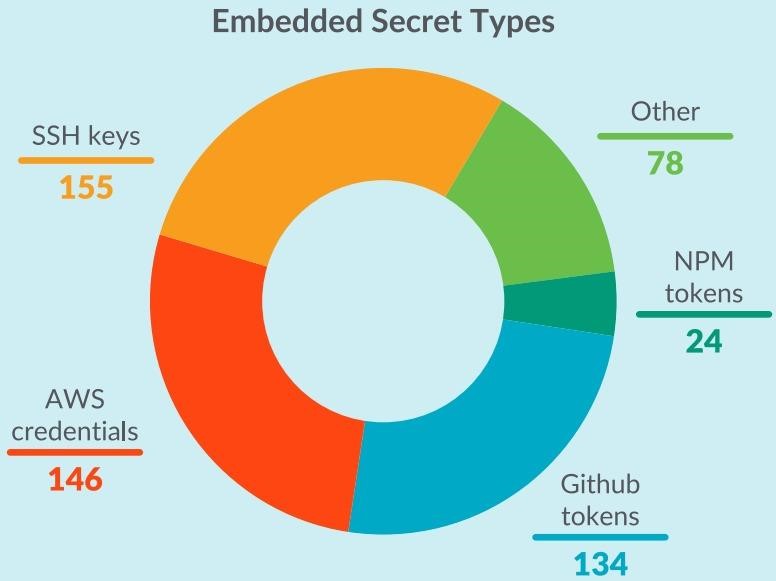
The most widespread in the Docker Hub were miners who used the resources of the victims to mine cryptocurrency. They were found in 608 images. In second place are images with built-in secrets (281 cases). Secrets are SSH keys, AWS credentials, GitHub tokens, NPM tokens, and so on. The researchers write that these secrets could be forgotten in the code by mistake, but they could also be deliberately introduced by attackers.
By the way, the media wrote that Miners Massively Use Free GitHub, Heroku and Buddy Accounts in Their Campaigns.
Sysdig summarizes that, unfortunately, the size of Docker Hub does not allow service operators to check all downloads daily and quickly, and because of this, many malicious images are simply not reported.

